V1.1 Release

Hey Folks!
We just performed another release this week and I’m psyched to fill you in on some of the new features! The two biggest are the addition of a module to analyze long communication sessions and a module that analyzes long URIs. Let’s jump into a bit about each.
Long Connection Analysis
As you may know, the beacons module analyzes network data in 24 hour chunks. This way, even when a system beacons home infrequently, we still collect enough data points to tag the system as a beacon. However, this begs the question, what if the malware does not beacon home? What if the attacker simply sets up a session back to the command and control server and leaves it active all of the time? This is where long connection analysis comes in.
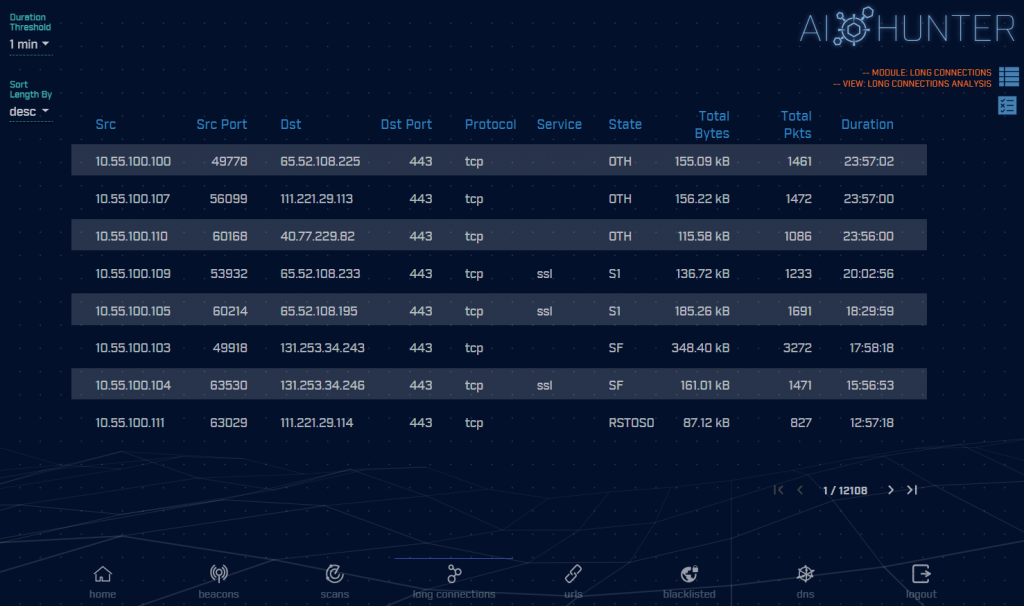
By selecting the “long connections” module, you will be presented with a list of the longest duration connections taking place on your network. The list is sorted from longest to shortest, but you can change this using the sort option in the top left of the screen. You can also set a threshold for the minimum connection duration time you want to be shown.
There are times when long connections are expected behavior. For example, BGP sessions between routers tend to persist as long as possible in order to update route information. There are even times when long connections are not optimal, but not necessarily evil. A good example would be an SSH user that leaves their connections active even when they are done on the system. For the most part, however, excessively long connection times (more than an hour) should be scrutinized carefully. If they are not evil, they may at least be in breach of policy.
Long URL Analysis
Our customers love AI-Hunter’s ability to identify when DNS is being used as a backdoor. Our new URL analysis module brings that same type of functionality to analyzing URIs. What may look like an internal system connecting to an external Web server may, in fact, be malware encoding information into the URI and passing that data out of your network. The url module is designed to allow you to quickly hone in on that type of activity.
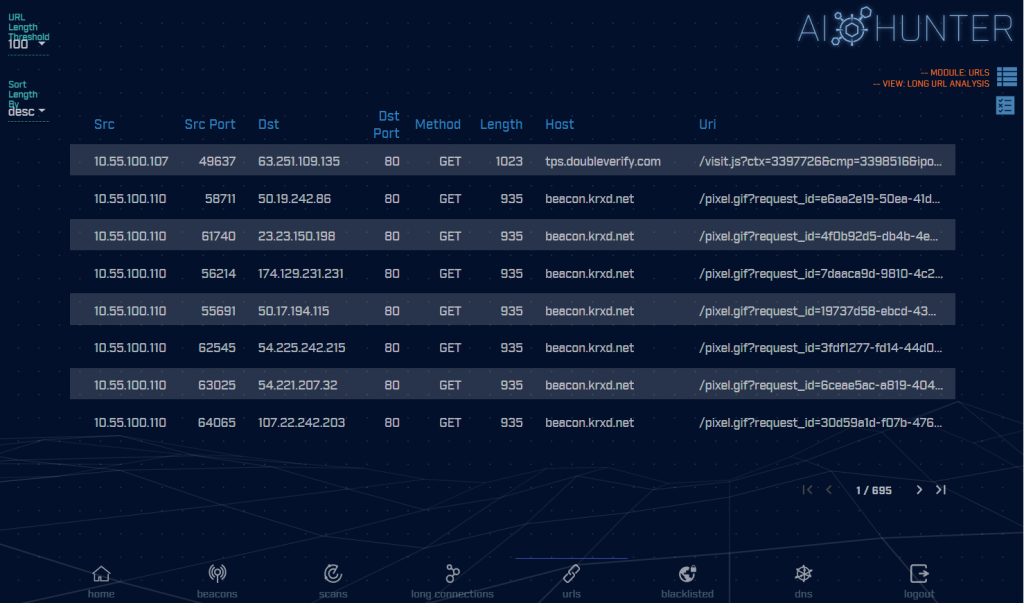
Similar to the long connections module, the URL module displays the connections that took place with the greatest amount of URI data. Also, like the long connections module, you can change the sort option or the threshold on minimum URI length to report. Most users should be fine going with the defaults.
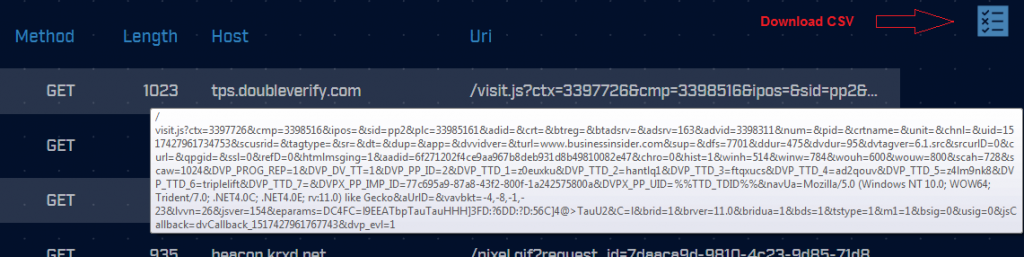
When URI exfiltration is taking place, it is not uncommon to see the data passed in the clear. However, using a simple XOR to obfuscate the data pattern, is a common technique as well. This means it can be helpful to extract the URI information for additional processing. If you mouse over the URI, a dialog box will appear showing the complete URI (this normally cannot be displayed due to its length). If you click on the report icon, you can download the data in comma separated format. This lets you perform additional processing in another tool.
A huge thank you goes out to our beta testers that helped us vet these new modules!
We have another new module in the works and wow, this one is a game changer. It really ties together the whole threat hunting experience! At ACM our goals are to simplify the threat hunting process so that:
- More people can threat hunt their network
- Those threat hunts take less time to complete
This new module will go a long way toward accomplishing both of those goals. Intrigued? Stay tuned to this blog/channel over the next few weeks for further announcements.

Chris has been a leader in the IT and security industry for over 20 years. He’s a published author of multiple security books and the primary author of the Cloud Security Alliance’s online training material. As a Fellow Instructor, Chris developed and delivered multiple courses for the SANS Institute. As an alumni of Y-Combinator, Chris has assisted multiple startups, helping them to improve their product security through continuous development and identifying their product market fit.