AC-Hunter Beacons
A System Frequently Calling Home to a Command and Control Server Is a Clear Indication of a Compromise
Today’s advanced backdoors are extremely hard to detect. Simple signature detection cannot detect encrypted and malleable Command and Control (C2) sessions. AC-Hunter detects malware by targeting its network communications rather than analyzing the host itself, where malware writers can leverage a wide range of evasion techniques.
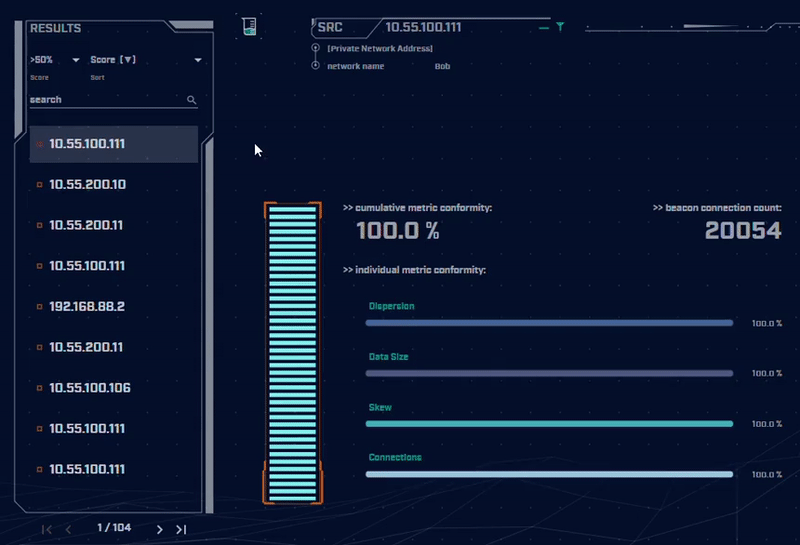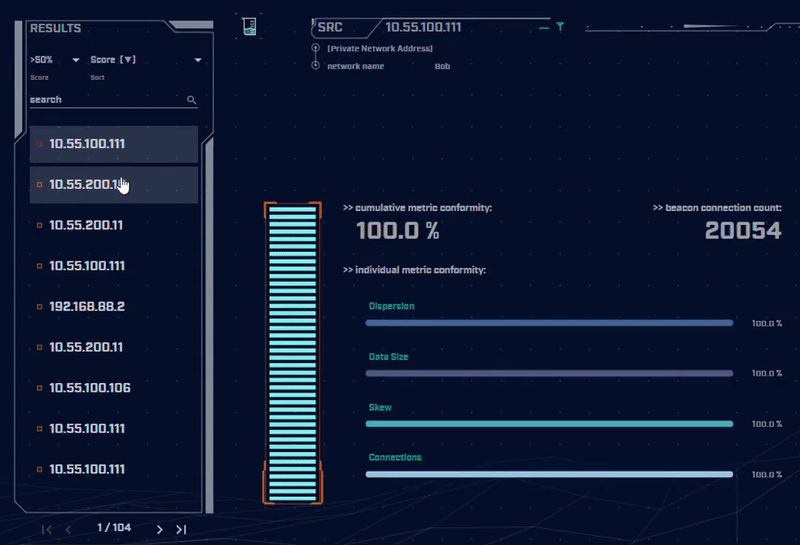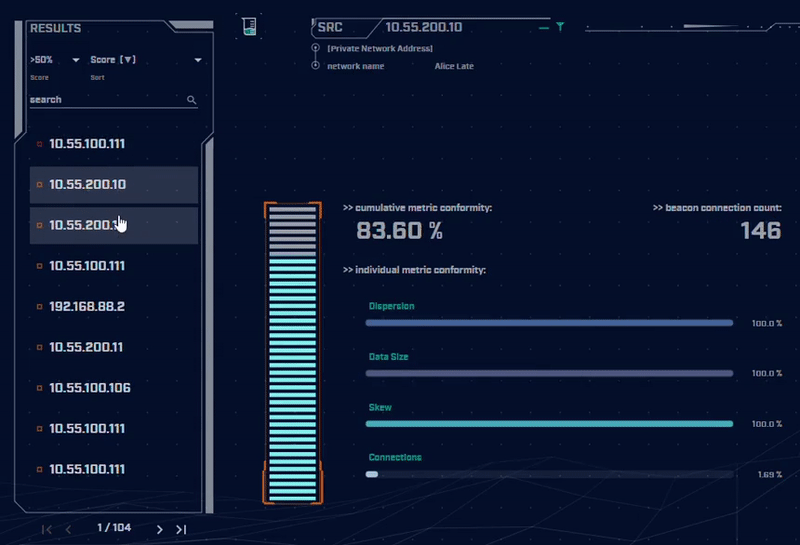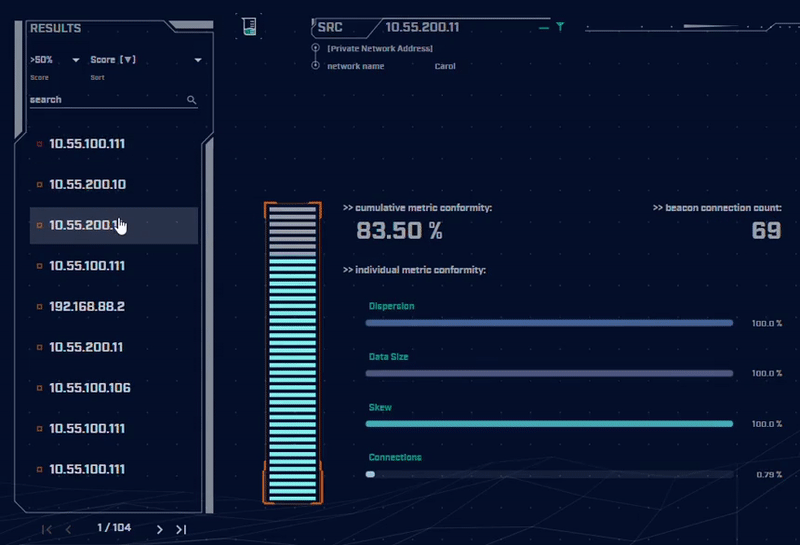
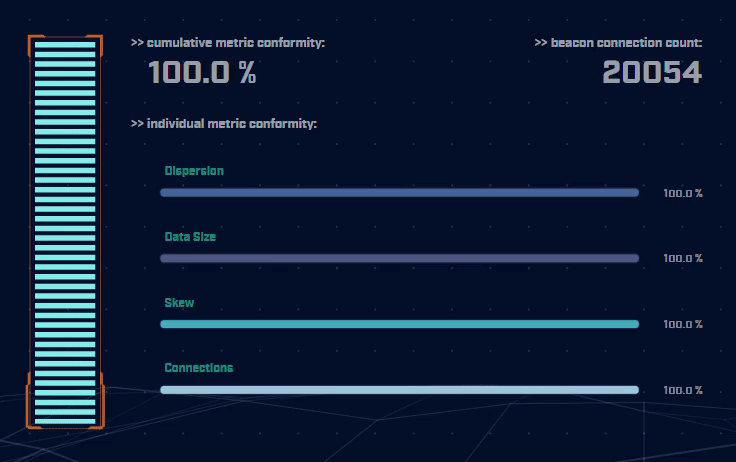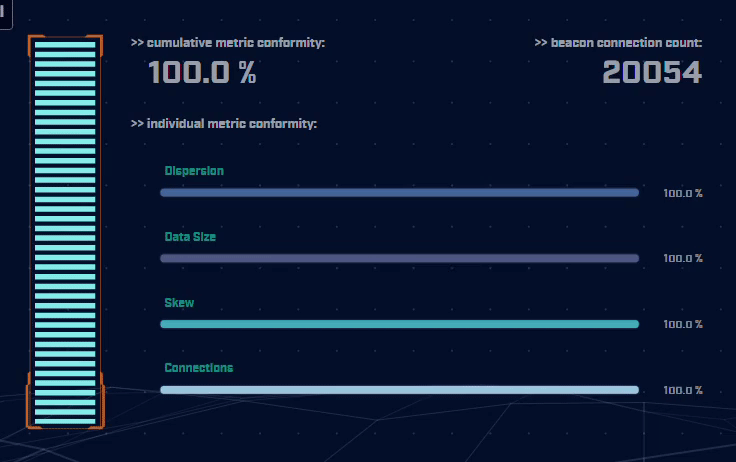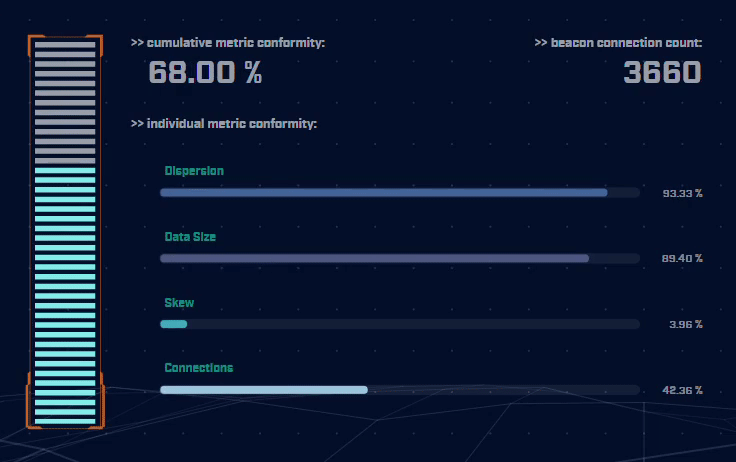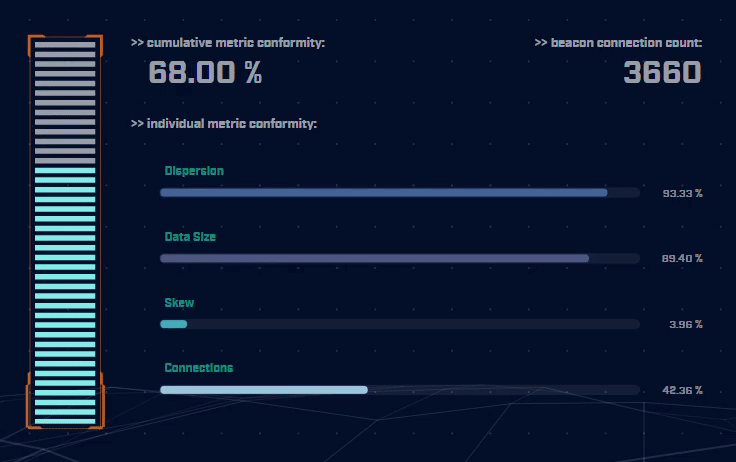
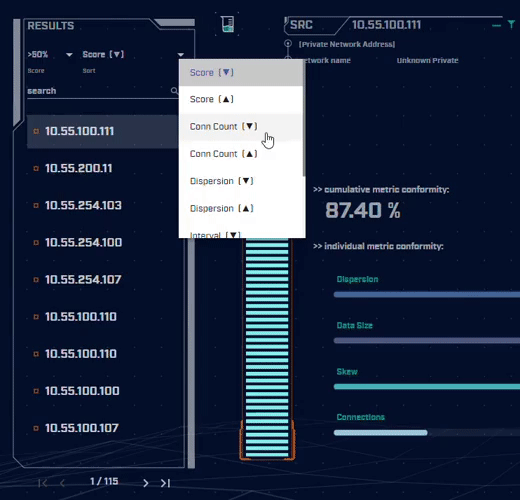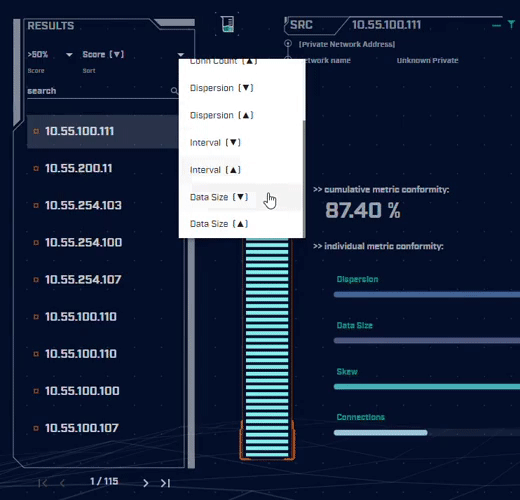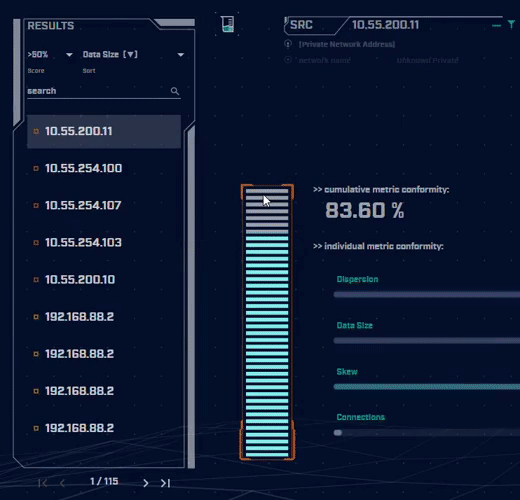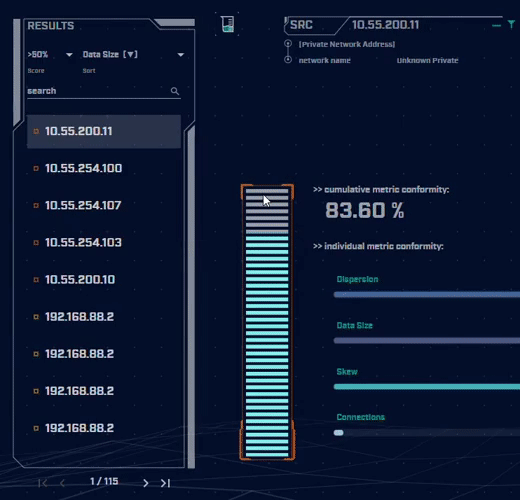
Rather than focus on signatures for known bad actors, AC-Hunter detects consistencies and patterns in the behavior of backdoors. How? It utilizes a mixture of detection techniques that rely on attributes like an interval of connections, data size, dispersion, and advanced algorithms.
Want to dig into the details of the communication session to understand what makes it suspicious? AC-Hunter provides a wealth of information to support your threat hunting activities. We also provide many options for the analyst to filter and re-sort the criteria they are reviewing on the fly!
Using only one way to detect advanced backdoors is not an effective detection strategy. All the attacker would have to do is change one aspect of the C2 traffic to avoid detection. To address this, AC-Hunter uses 24 patented processes to analyze timing and data size characteristics and will quickly segregate normal communications from malicious communications.