BeaKer
System Forensics Simplified
About BeaKer
Microsoft Sysmon is well-known as a free, trusted, and convenient tool for host-based threat hunting. One of our favorite Sysmon features is its ability to log network traffic and the executables associated with each connection. This makes it the perfect link for tracking down which hosts, users, and programs contributed to a set of network connections.
Gathering Sysmon data takes time and effort. Setting up Windows logging, integrating with a SIEM, and deploying agents are all crucial steps in the journey. Here at Active Countermeasures, we wanted to provide a free and open-source solution to this problem: BeaKer.
BeaKer combines Microsoft Sysmon, WinLogBeat, Elasticsearch, and Kibana to provide insights into your network traffic. Quickly determine your network’s top talkers on both the host and application levels. Dig down into the connections made by a pair of hosts and see which users and executables contributed to the traffic. If you’re running a network threat hunt with a tool like RITA or AC-Hunter, BeaKer provides you the host-based information you need to take the next step in your investigation.
Primary Features
- Find which users and executables connected from one machine to another
- Determine the hosts and applications which make the most connections
- Collect network logs without tapping the network at a single location
Using BeaKer with AC-Hunter
Finding a threat is a straightforward task in AC-Hunter; we’ve worked hard to pull in the relevant facts, so you don’t have to. Unfortunately, once you’ve found a likely threat, the next step is inspecting the suspect system.
We wanted to make this simple as well. When you’re investigating a threat, you can switch over to BeaKer to see the name of the Windows system, the process that created them, and the user under which it’s run. These should quickly give you a picture of whether the traffic is benign, malicious, or needs more investigation.
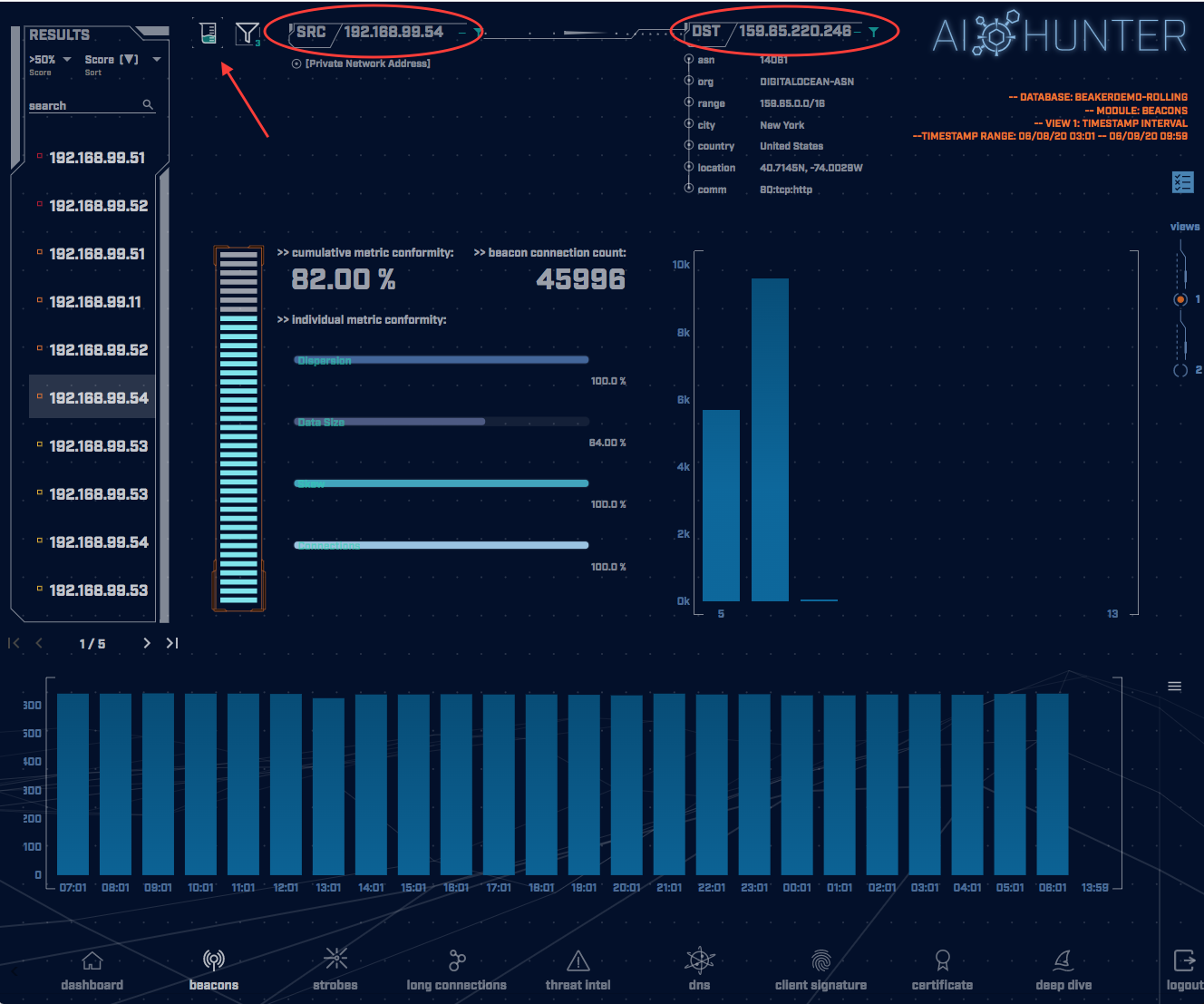
Let’s take a look at an example; as part of working with AC-Hunter, you come across beacon-like behavior from one of your systems to an unknown host on the Internet (which happens to be a cloud server):
The traffic is coming from 192.168.99.54. The next step is to look at that internal system to see what program is generating hundreds of beacons an hour. To do this, you click on the BeaKer icon indicated by the arrow in the above picture.
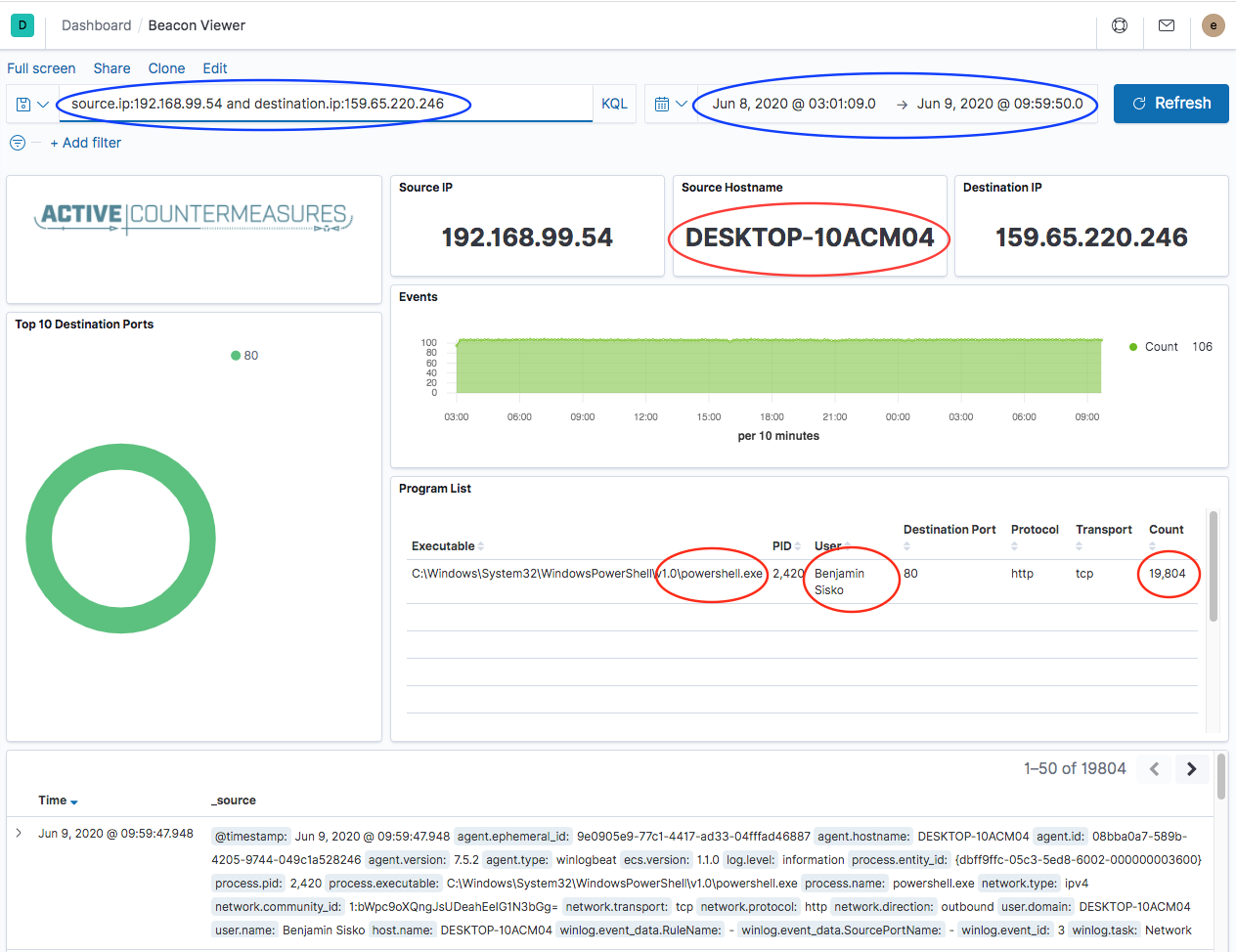
Your browser will open a new tab with this display:
Kibana has been told to only show information about traffic between these two IP addresses for the time in question – see the blue ovals.
Further down in the display, we get some additional information in the red ovals; the hostname of the machine, the program generating the traffic, the person under which that program is run, and how many connections were generated. In this example, Benjamin Sisko works in Finance and has no legitimate reason to be running PowerShell on his Windows system, let alone more than 19,000 times!
These few pieces of information are just what we need to identify that the traffic we saw in AC-Hunter is likely malicious and needs some follow-up. Benjamin may have some malware running on his system that needs attention.
Download Details
In the above example, BeaKer runs as part of AC-Hunter. However, AC-Hunter is not required. BeaKer has full functionality running as a stand-alone application.
When you perform the install, you get an additional set of services (ElasticSearch and Kibana are loaded onto either the AC-Hunter server or a separate machine if the load requires). These accept network connection information from your Windows systems provided by an agent that runs on them. The agent keeps sending over this connection data, so when you need to look up details about a connection, it’s waiting for you.
As part of our ongoing commitment to free and open-source software, we’ve made both BeaKer and the BeaKer Windows agent open source.
Download BeaKer: https://github.com/activecm/BeaKer
Additional Resources