Installation of AC-Hunter
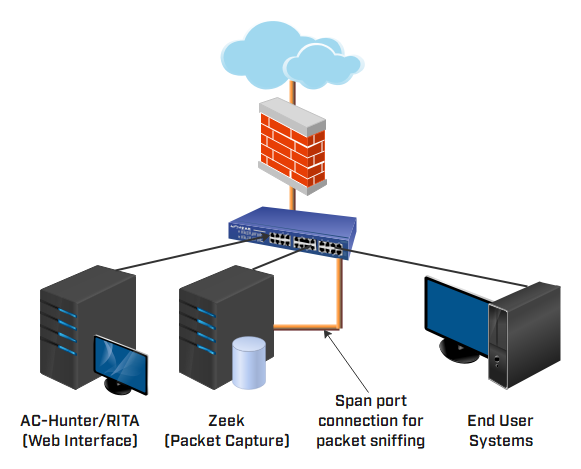
AC-Hunter leverages Zeek to collect packet information from your network and analyze the results. Zeek runs on a single system and connects to a span port just inside your firewall. The AC-Hunter system can be located anywhere on your internal network, provided it has connectivity to the Zeek system.
System Requirements and Installation
AC-Hunter requires two systems; one running AC-Hunter (network analysis) and another running Zeek (network monitor).
Both systems are designed to run on 64-bit Linux operating systems. The preferred and supported platforms are Ubuntu 16.04 LTS, Ubuntu 18.04 LTS, Ubuntu 20.04 LTS, CentOS 7, and RHEL 7.
The AC-Hunter install script will install AC-Hunter on one server and Zeek on another. The installation process will automatically synchronize both systems to function together correctly.
If you have multiple connections to the Internet, you can install multiple Zeek systems or sensors, all feeding data back to the same AC-Hunter instance.

System Running AC-Hunter
(network analysis)
Suggested Minimum Specifications
- Processor: Two cores minimum. Four are recommended.
- Memory: 16GB minimum. 32GB or more recommended.
- Storage: 300GB minimum. Additional storage is recommended if you plan to keep data for an extended period (more than a few weeks).
- Network: Standard Ethernet network card interface (physical or virtual).
- Virtualization: Can be run inside a virtual machine.

System Running Zeek
(network monitor)
Suggested Minimum Specifications
- Processor: Two cores plus an additional core for every 100 Mbps of traffic being captured (three cores minimum).
- Memory: 16GB minimum. 32GB if monitoring 1000Mb or more of network traffic.
- Storage: 300GB minimum. 1TB or more is recommended to reduce log maintenance.
- Network: To capture traffic with Zeek, you will need 2 network interface cards (NICs). One will be for the management of the system, and the other will be the dedicated capture port. Intel NICs perform well and are recommended.
- Virtualization: This should be dedicated hardware as opposed to virtual machines. VM scheduling and resource congestion with other VMs can cause packets to be dropped or missed. We discourage running Zeek inside a virtual machine.