RITA
Real Intelligence Threat Analytics
About RITA
Real Intelligence Threat Analytics (R-I-T-A) is an open-source framework for detecting command and control communication through network traffic analysis. The RITA framework ingests Zeek logs or PCAPs converted to Zeek logs for analysis.
There is often a massive disconnect between what attackers are doing and what we, as defenders, are doing to detect them. There is currently a huge push to develop better and better Indicators of Compromise (IOC) or better threat intelligence.
A newer development in information security is hunt teaming. This is where an organization has a team of individuals who actively go looking for evil on a network. This makes some significant assumptions on the part of the defenders. The first assumption is that security automation has failed somewhere. The second assumption is that the existing technologies will not be sufficient to find the bad guys.
But how can a team even begin approaching these issues? It requires a fundamental shift in how we approach detecting attacks.
Traditionally, this requires a set of simple signatures designed to detect evil. However, this can be very hard.
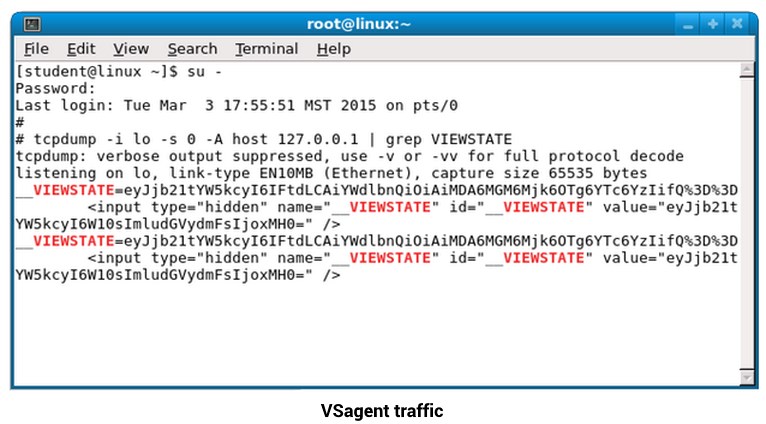
For example, one of Black Hills Information Security’s tools is called VSagent. It hides its Command and Control (C2) traffic into the “__VIEWSTATE” parameter, which is base64 encoded. Further, it beacons every 30 seconds.
Unfortunately, the ideas of this backdoor can be easily modified to bypass any simple signature you throw at it.
How then, exactly, can we approach malware like this? It requires us not to look at individual TCP streams but rather at the communication related to much larger timeframes.
To help with this, we have released Real Intelligence Threat Analytics (RITA). We hope this is the beginning of a new framework for hunt teaming. There are several different frameworks for Pentesting, such as Metasploit, SET, and Recon-ng. The idea of a framework is that it is effective, extensible, and allows people in the InfoSec community to add additional modules to it continuously is our goal.
Primary Features
- Beacon Detection: Identify signs of beaconing behavior in and out of your network.
- DNS Tunneling Detection: Identify signs of DNS-based covert channels.
- Identify Long Connections.
- View User-Agent strings.
- Blacklist Checking: Query blacklists to search for suspicious domains and hosts.
Download Details
Additional Resources
Blog Posts:
Getting Started on Contributing to RITA
Webcasts:
Getting Started with RITA
Hacking RITA
If you get value from using RITA and would like to go a step further with threat hunting automation, futuristic visualizations, data enrichment, and extended features, take a look at AC-Hunter.