AC-Hunter DNS
DNS Can Be Used as a Covert Communication Channel and as a Way to Exfiltrate Data
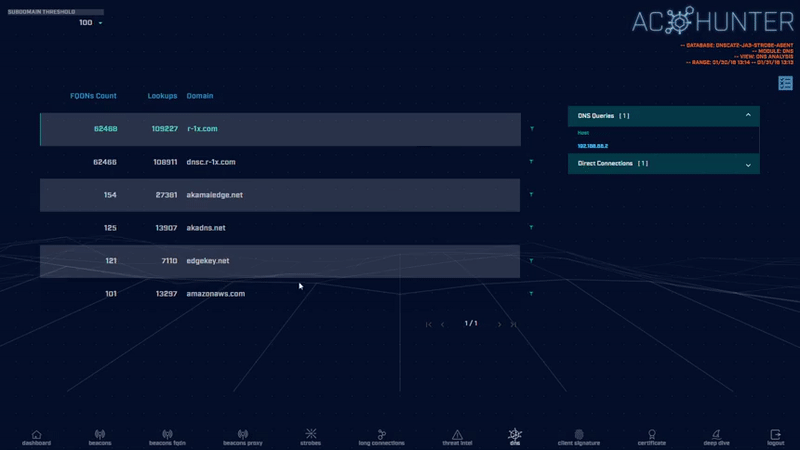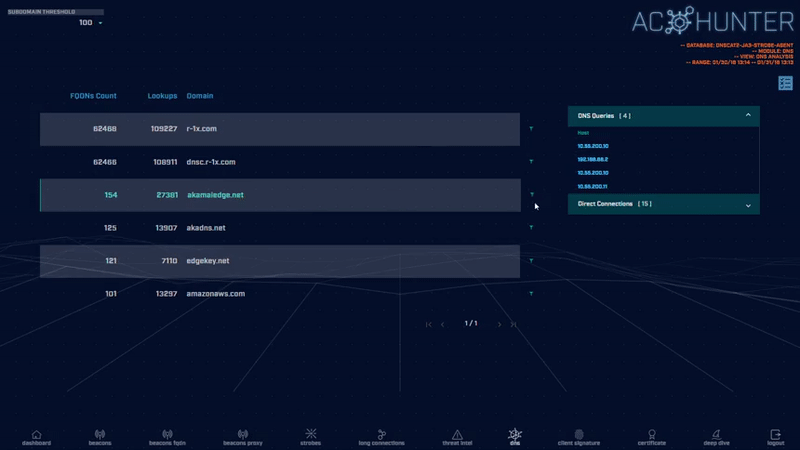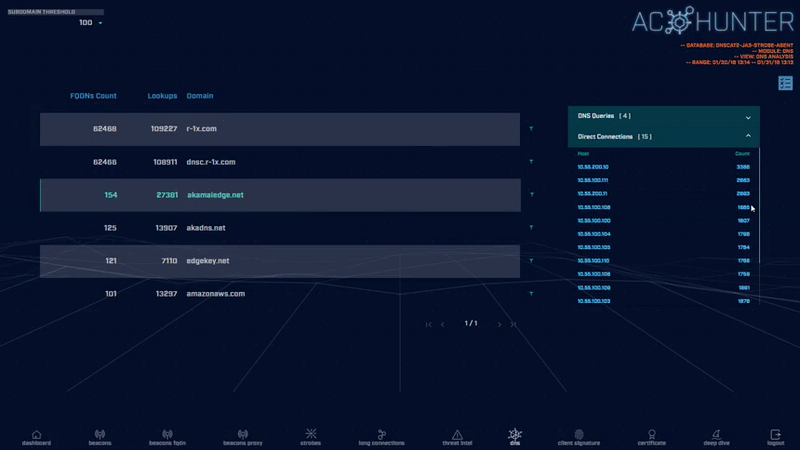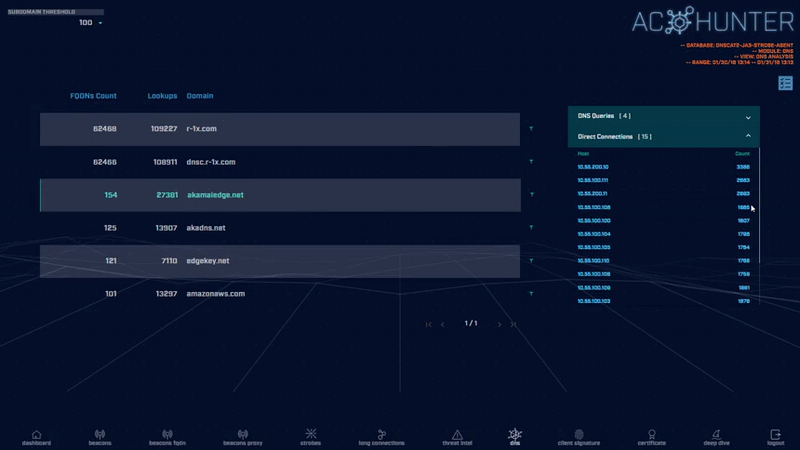
Because DNS is such a noisy protocol, it tends to have minimal logging enabled. Combine that with the fact that most environments permit DNS out of their environment, and it makes a good choice for hiding suspect traffic patterns in plain sight.
DNS C2 is one of the most common means for attackers to exploit highly-secure environments. For most organizations, DNS is a required protocol and it is usually between two trusted endpoints. For example, most DNS traffic will use a Domain Controller or use “trusted” DNS providers like Google.
We detect this by looking at the number of subdomains per domain and will flag suspicious quantities. AC-Hunter easily identifies excessive sub-domains.