AC-Hunter Long Connections
Attackers Attempt to Evade Beacon Analysis by Creating Persistent Connections
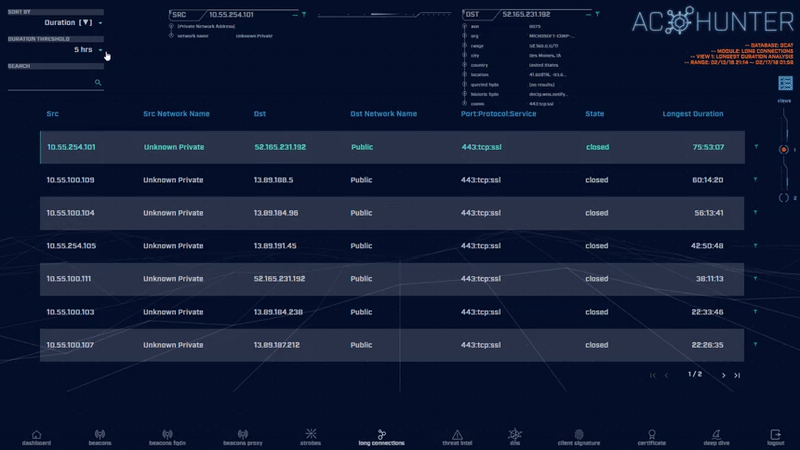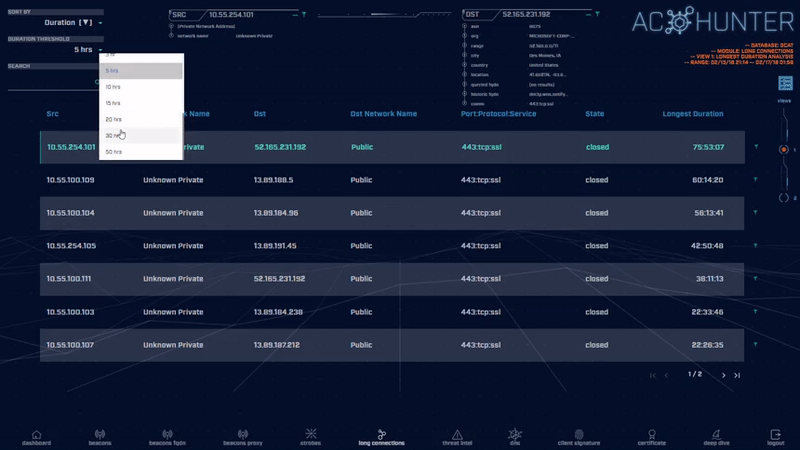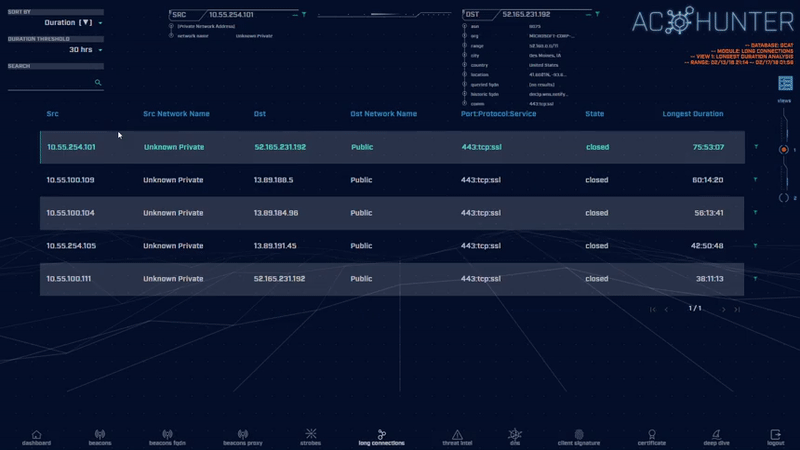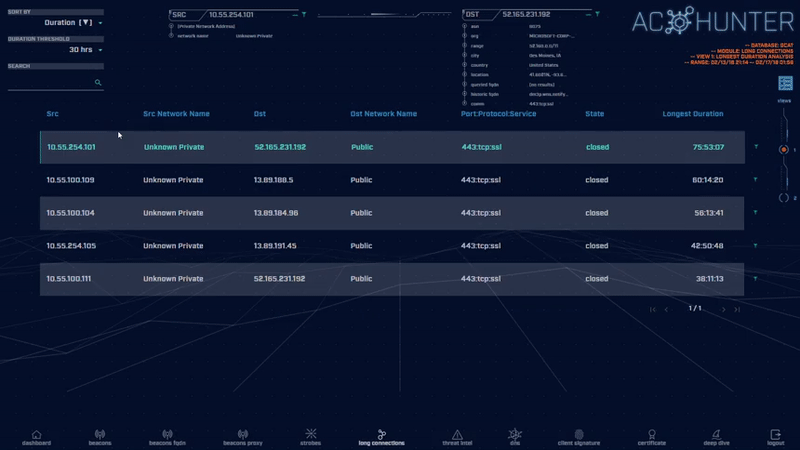
One way attackers attempt to evade beacon analysis is by creating persistent connections. In other words, they attempt to leave the connection active for as long as possible. This creates fewer firewall log entries and thus is indicative of more advanced malware.
Most legitimate connections run for one hour or less. By identifying connections that remain active for many hours or even many days, you can quickly spot suspicious activity.
This module will also provide data of total cumulative connection time between hosts and total bytes transferred during these connections.