AC-Hunter Safelisting
AC-Hunter Lets You Quickly Safelist Known-To-Be-Safe Communications
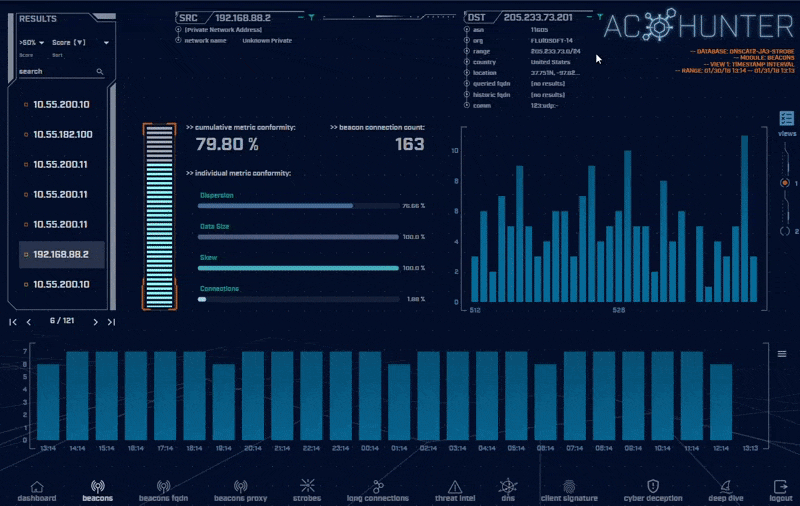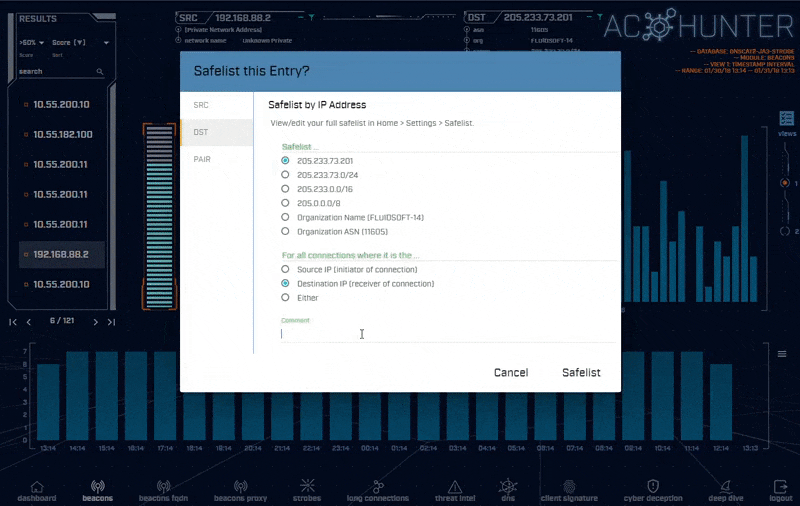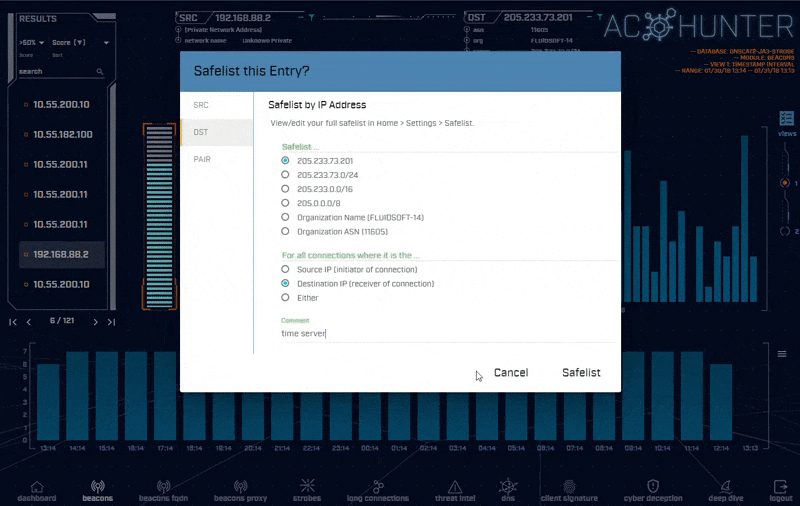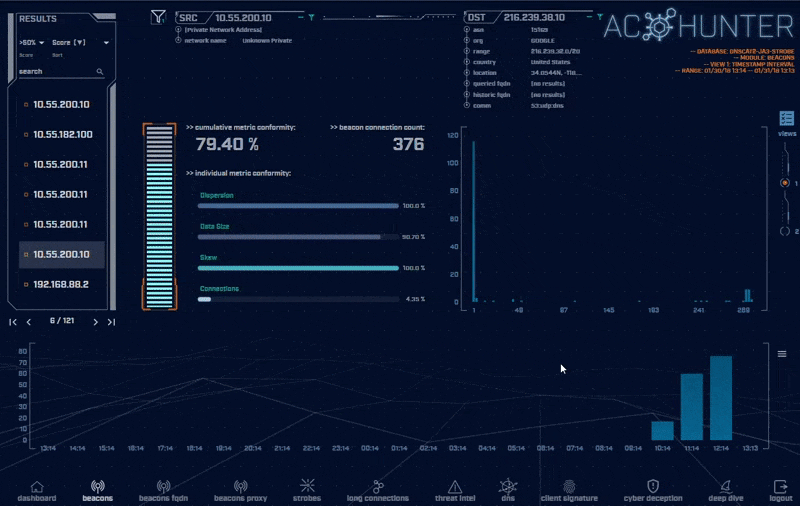
There may be times AC-Hunter flags a communication as suspicious, which you actually know is legitimate. For example, you may have your systems configured to verify their time to a customized time server.
AC-Hunter makes it easy to set up exceptions for these systems so they no longer appear in the final report. Safelists can be created directly from the UI based on source, destination, pairs, single IP address, class A, B, or C range, domain, choice of sub-domain level, Org Name, or ASN.