AC-Hunter Strobes
A Strobe Makes No Attempt At Being Stealthy
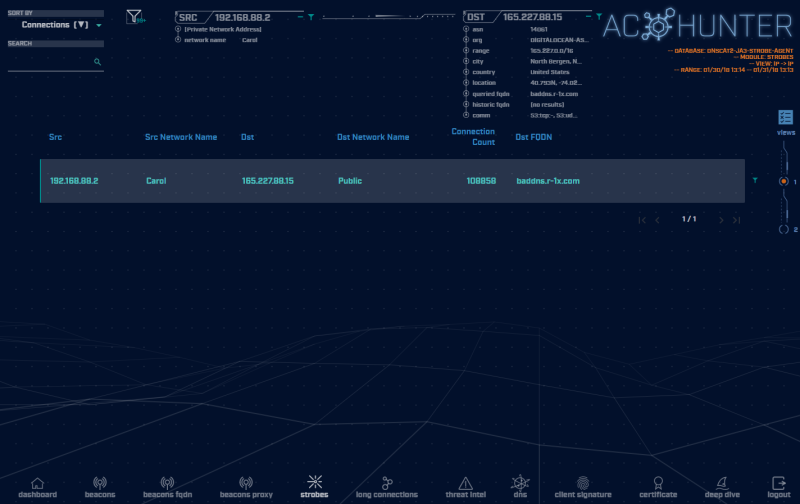
Strobes are similar to beacons in that they are repeated connections between two IP addresses. However, unlike a beacon which may try and hide its signaling, a strobe does not attempt being stealthy. A signal that triggers two or three times a second is an excellent example of a strobe.
Because strobes are so noisy, you may find that the source is due to poorly written code or a misconfiguration rather than actual malware. Most malware will at least attempt to be stealthy.
These types of rapidly repeated connections will be shown in this module.