Malware Analysis as a Prey Animal

Intro
The year is 1453 and you’ve been ordered by the king to protect the kingdom from the Great Northern Basilisk. You have positioned yourself upon the highest point in the kingdom, your quiver full of the finest arrows. You are confident, skilled, and ready for the hunt. Then it strikes you… what does a Great Northern Basilisk look like? Does it only come out at night? Can it fly?
You are so screwed.

Threat hunting and protecting a computer network parallels the above scenario. You can be armed with the best tools and the sharpest of skills, but without a fair knowledge of your prey, you will not be a successful hunter.
Know your prey.
As a network threat hunter, one of your “prey animals” is malware. And more specifically for this article, malware beacons.
What Is Malware?
The title Malware is a portmanteau word formed from the words Malicious Software. Perfectly descriptive, right? Okay, we’re done here.
Not so fast there Skippy. Surely there’s more to know…
Malware is software, scripts or code that is designed or modified to be malicious in nature with the goal of establishing an unauthorized connection(s) between systems, exfiltrating data, implanting data, information reconnaissance, remotely running processes, as well as just causing general mayhem such as deleting all image files from a system, as a few examples.
How Does Malware Work?
So many ways. Volumes can be written about this and have been written about this.
Equally, an attacker can get malware onto a system using a variety of methods. Most common examples include; Email Phishing, whereas clicking a malicious link can run a script directly, or from an external web server or direct download, Remote Desktop Protocol credential hacking, or with a physical presence of malware being introduced from a USB device, such as a flash drive or other removable media.
Some malware code has a very small footprint on a target system and can be run entirely within a systems’ memory without writing anything to the system disk. Sneakiness, check.
For the simplicity of this article, we’ll focus on malware beacons.
Once malware is on a system or device, the first order of business for beaconing malware is to execute from the target system and establish a connection back to “home base”, most commonly an external server on the internet. This communication channel is referred to as the Command and Control channel/server or the abbreviations C2 or C&C. The malware is scripted to “phone home” to the C2 server to check for commands or “marching orders” upon a set interval of time. For the sake of example, every 30 seconds. This outbound consistent communication from the malware is what’s referred to as a beacon.
The C2 channel is used by the attacker to issue commands from the C2 server to the host malware. This can be a wide range of commands from “Show me the username on this PC” to “Export all customer credit card data”.
Keep in mind that a living malware environment is not constrained to PCs, workstations and servers. Malware can be run on any device that supports whatever programming language the malware was designed to use. Malware can and has been found on a multitude of devices, IoT & IIoT devices such as IP cameras, thermostats, refrigerators, industrial control units, etc.
These types of C2 connections will persist as long as nothing fails within the system, is decidedly torn down by the attacker, or is detected by YOU.
What Does Malware Look Like?
We can break it down to a very basic level to paint a picture of what malware looks like when viewed as network communications:
- Repetitive communications to an unfamiliar or unverified external IP address or domain
- A communication timing pattern that is strict (non-human in nature)
- Nonsensical communication to known services (why is my host pinging TeamViewer every 500ms?)
- Unexplainable data transfer (why is my host sending 46GB of data to jimbobsgarage.com?)
- Unconventional port usage
- A larger than expected number of connections
This basic outline provides us some of the building blocks for detecting malware beacons by monitoring and analyzing all the traffic entering and leaving your network. If all you have is raw network traffic logs and a lot of extra time, this will be fun. No, it will not be fun at all. Really.
Your hair may grow faster than finding compromises by sifting through logs.
Fortunately for us all, we have many great open-source tools to help us find these needles in our haystack. For network traffic capture, Zeek will provide high-fidelity network traffic logs for further analysis. For beacon analysis, RITA is the open-source star of the show, plus it works well with Zeek logs. And, if you have some PCAP captures from Wireshark or another tool, these can be imported into RITA for beacon analysis also.
In a lab environment, we ran a malware replication of Havex, a real-life RAT malware that was first discovered in-the-wild in 2013 as one example of what type of behavior can be observed. This one-hour traffic example was captured by Wireshark as a PCAP file then imported into RITA for beacon analysis and visualized through AI-Hunter. I am using AI-Hunter for a screenshot of the malware, as it provides a clear visualization of the data generated by RITA.
This is an HTTP beacon with a 30-second timing interval for calling back to the C2 server. The host “victim” is 10.0.2.15 and the C2 server is 68.183.138.51:
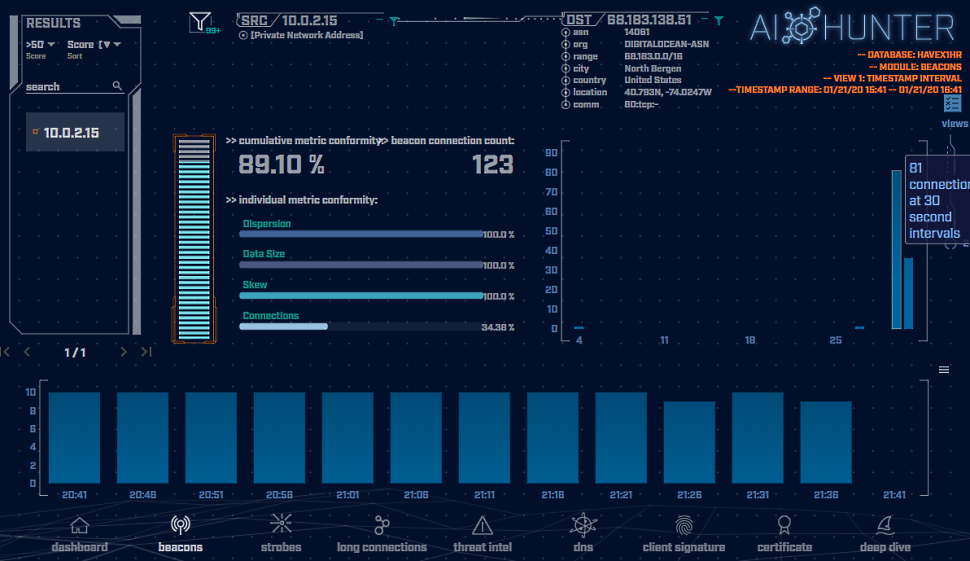
Using a one-hour long PCAP capture, the Havex malware traffic is reaching a high 89.10% beacon score right out of the gate. One tell-tale sign of a beacon is shown in the graph towards the bottom of the screen. This is the connection count over time. Each blue bar is a 5-minute block of time and we can see how consistent the connection count is over the time period. So much so that you can almost draw a flat line across the top.
In the center-right of the screenshot, this graph is displaying the connection intervals. As you see, the majority are 30 and 31-second intervals. Normal human-system activity will be much more randomized in nature, so this is suggesting a solid probability that what we are seeing is programmed communications.
These indicators become more absolutely defined over a longer capture time period. This is clearly a beacon, and in this case, we know it’s malicious malware. This knowledge and research are key while threat hunting for malware beacons, as not all beacons are malware and not all beacons are malicious in nature. There are normal non-malicious processes running within your network that will generate similar traffic patterns such as NTP (Network Time Protocol) and software update services that will exhibit similar behaviors, however, you should be able to verify the communications by doing an investigation of the destination and classify it safe or not.
The PCAP file used here is available below for you to run through any tool you wish or for further inspection. This is a replication of Havex traffic in a PCAP file, not actual malware, so it is safe.
Know your prey and happy threat hunting!

Keith’s appreciation for computing and processes originates from working with his first personal computer in 1982, a TI-99/4A. Keith sees himself as fortunate for the opportunity to apply his passion towards a career that assists in the advance of technology and continuing education.