Network Cyber Threat Hunting Class – A Letter From Chris

Hey Folks,
I want to start with some statistics from the Network Cyber Threat Hunting webcast this weekend as it sets the context for the rest of this note.
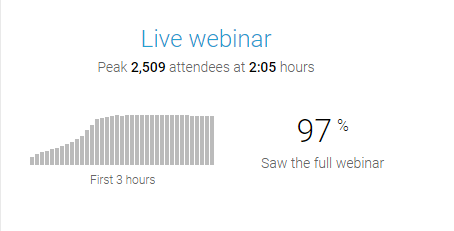
These results are pretty amazing. We had just under 6,000 sign up for the class. We handled hundreds of support emails prior to the event. We had 2,500 people go through six hours of cyber threat hunter training that included hands-on labs. We are now handling many hundreds of follow up questions.
The feedback we are receiving is overwhelmingly positive. I think the best comment I saw was that someone took what they learned on Saturday, and on Monday was able to turn that knowledge into a job promotion within their company. This is exactly why John and I do this type of training!
However, the webcast did not go off without a few bumps. The first lesson learned is that if you are going to offer six hours of training, you need to break it up into smaller parts. The webcast cut out about an hour before completion. Trying to create a video that long simply broke the system (this is why chat was online while the video/audio cut out). Further, we presented new concepts and techniques that people said they needed time to digest. One comparison I saw was that it was more than just drinking through a firehose, it was drinking from a geyser. So in the future, these webcasts will be smaller and easier to consume.
We had some positive feedback on the changes we made to chat. Folks liked having the open forum, as it permitted them to interact with each other. I’ve seen quite a few notes from people that were pretty sad once chat was closed down, as they were meeting cool people and exchanging ideas. This to me is awesome, as we are trying to build a community. On the converse, some folks were frustrated as they found the chat to be distracting and felt info didn’t stay on the screen long enough to consume. They missed having a moderated chat channel. We are thinking through the concerns on both sides and may have a solution that will make everyone happy. Stay tuned for more on that as the pieces fall into place.
We have some follow up tasks like getting the recording online and sending out class certificates. We are a small team, so I appreciate your patience. It may be the end of the week before we close out all post webcast tasks. I know that seems like a huge delay, but again, check out the above attendance graphic. 😉 Attendees will be able to access everything from the password-protected page they have been using throughout the webcast.
If you enjoyed the training and want more hands-on time, or if you missed it but really want a deep dive, We’ll be offering a two-day network cyber threat hunting class in San Diego at Wild West Hackin’ Fest Way West. This will be in San Diego on March 10th and 11th, 2020. The name of the class is “Network Cyber Threat Hunting With Security Onion“. As the name implies, the class is focused on turning Security Onion into a hardcore network threat hunting tool. A huge portion of this class will be labs. My goal is to take people from nothing to a platform that can be used to mine command and control channels which students can immediately apply back at the office.
Thanks again for the awesome turnout,
Chris

Chris has been a leader in the IT and security industry for over 20 years. He’s a published author of multiple security books and the primary author of the Cloud Security Alliance’s online training material. As a Fellow Instructor, Chris developed and delivered multiple courses for the SANS Institute. As an alumni of Y-Combinator, Chris has assisted multiple startups, helping them to improve their product security through continuous development and identifying their product market fit.