The Gap Filled By Threat Hunting

Where is the Gap?
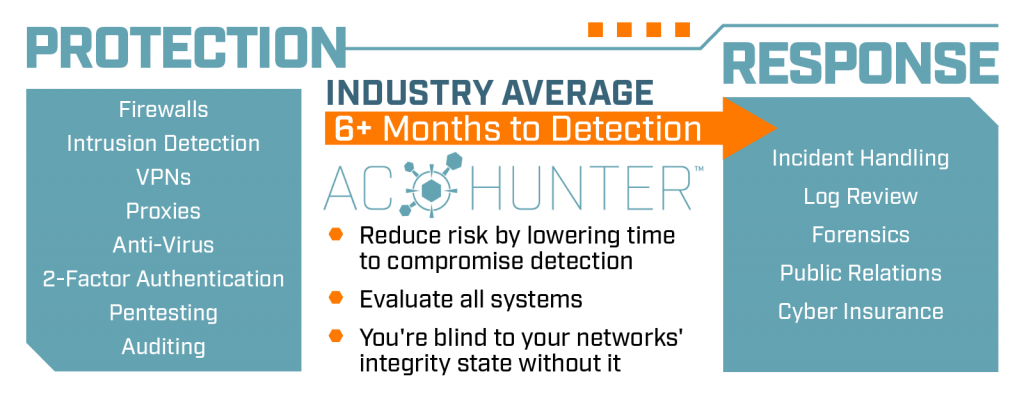
When you look at existing security solutions, they fall into one of two categories. They are either protection based, which is focused on keeping the bad guys out. Firewalls, intrusion detection, two-factor authentication fall into that category. Or they are response based and designed to be implemented once we know the bad guys are in the network. Incident handling is a great example of that.
The problem is, only using these two practices leaves a giant gap in your company’s security. If the bad guys can manage to get past your protection solutions, it could be a while before you actually see them in your network. By the time you see them, they have already stolen your company’s data!
As an analogy, imagine thinking your bank was “secure” because you checked the locks and perimeter cameras, but never bothered to look in the vault to see if any criminals are actively emptying all of the strongboxes. This is why we have seen numerous companies receive their security attestations at the exact same time an active compromise was taking place.
Average Detection Time
The current industry average detection time for network security breaches is 6 months. That means the bad guys have been in your network for half a year stealing your companies’ data without you knowing. The now-famous “SolarWinds Compromise” is a perfect example of this. The breach happened in March, and it wasn’t discovered/made public until December.
The “best” part is… most of the time these breaches are discovered by outside sources! That means you didn’t even find out your company was breached… the FBI or another organization had to tell you. Again, the SolarWinds breach is a perfect example, as the compromise was discovered by FireEye.
Allowing a breach like this to go undetected on your network could tremendously affect what companies or consumers are willing to do business with you.
Filling the Gap
By threat hunting your company’s network, you are performing the ultimate validation test of your network’s security. It does not matter if you have every protection security solution in place possible… if intruders are on your systems, one or more of those controls have failed and they will wreak havoc in your network until you eventually see them. As we know, this can take months.
If your goal is to keep the integrity of your network, threat hunting provides the ultimate verification of whether you are secure.
Our Threat Hunt Tools
RITA
Real Intelligence Threat Analysis (RITA) is an Open-Source framework that ingests Zeek Logs, and currently supports the following major features:
- Detection of Command & Control (C2) Channels: Search for signs of beaconing behavior in and out of your network
- DNS Tunneling Detection: Search for signs of DNS based covert channels
- Blacklist Checking: Query blacklists to search for suspicious domains and hosts
AC-Hunter
AC-Hunter is our commercial product. It will analyze the previous 24 hours of your network traffic to identify if there are any indications of an internal system that’s been calling out to the internet and creating a command and control channel (C2). That’s our core focus, that’s what we go after – C2 beaconing.
We have a unique solution. To begin with, we’re low touch — we need to monitor traffic going in and out of the internet and that’s it. There are no agents that need to be installed and we can protect everything, including Internet of Things (IoT) devices that you can’t install software on. If the attackers are encrypting data, we can still spot those command and control channels also.
We’ve created a tool that’s very simple and easy to use. So, it’s not just the smartest person in your Security Operations Center that can do the threat hunting, this can go all the way to the junior analyst level!
We’ve also kept it affordable, with it thousands below our competitors’ prices.
Explore the AC-Hunter features
Schedule a personal AC-Hunter Demo

Shelby has a strong background in Social Media Marketing and Event Management. Her interpersonal skills and passion for community building are what lead her to her position as Content & Community Manager at Active Countermeasures. When she’s not working, Shelby enjoys spending time with her husband, daughter, and four cats.