AC-Hunter Cyber Deception
Cyber Deception Is a Strategy to Attract Cyber Criminals Away From an Enterprise’s True Assets and Divert Them to a Monitored Decoy
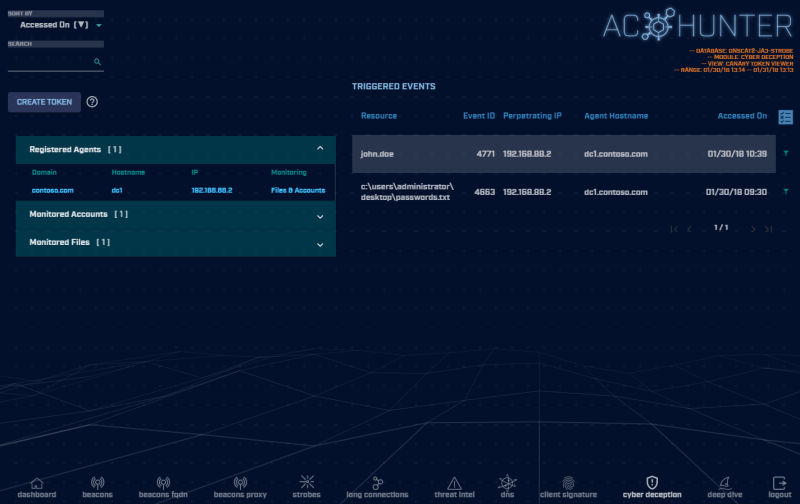
The cyber deception module allows for the creation and monitoring of canary tokens. There are two types of canary tokens available. File-access tokens will generate an alert when a designated file has been accessed. User-access tokens will generate an alert when an authentication attempt is made against a monitored user, or a Kerberos ticket is requested for that user.
This module requires listening agents to be registered on your Domain Controller, which will allow for file and/or user account monitoring. Once these agents and monitored resources are properly set up, triggered deception events will appear within the “Triggered Events” table in the AC-Hunter cyber deception module for any alerts generated from the tokens.