AC-Hunter Threat Intel
Customizable Threat Intel Feed Analysis
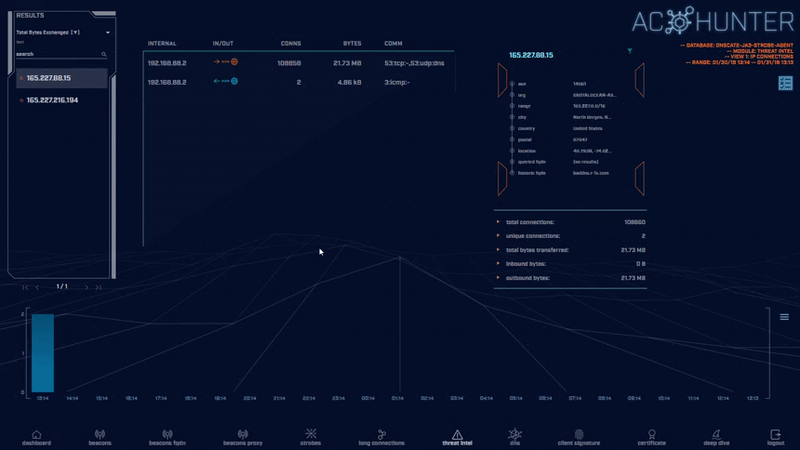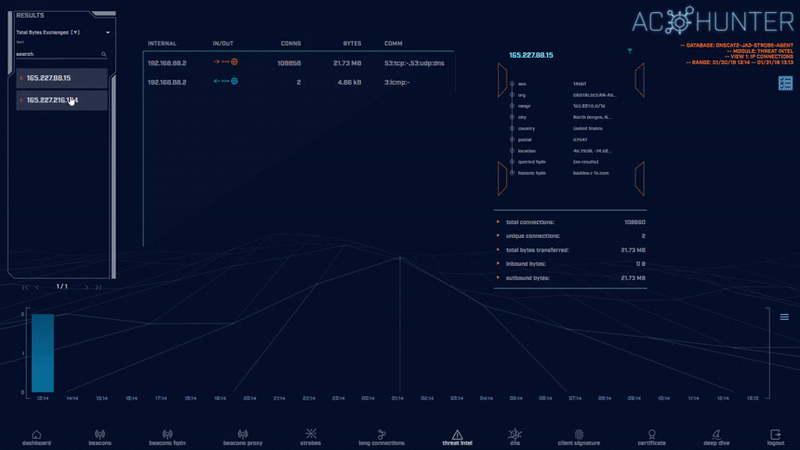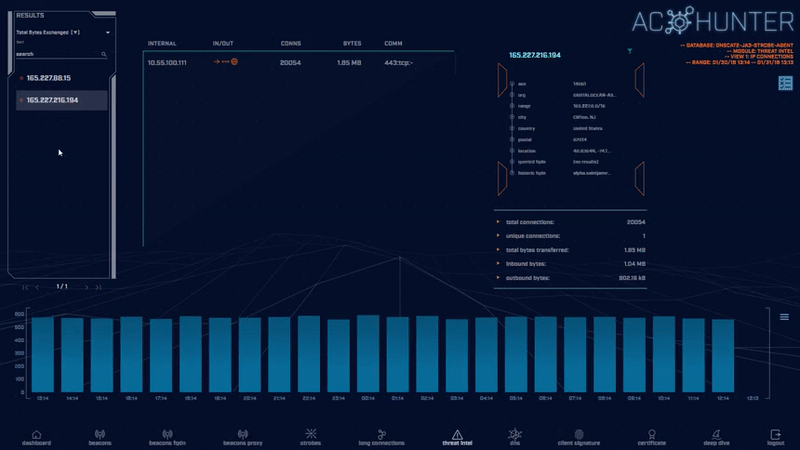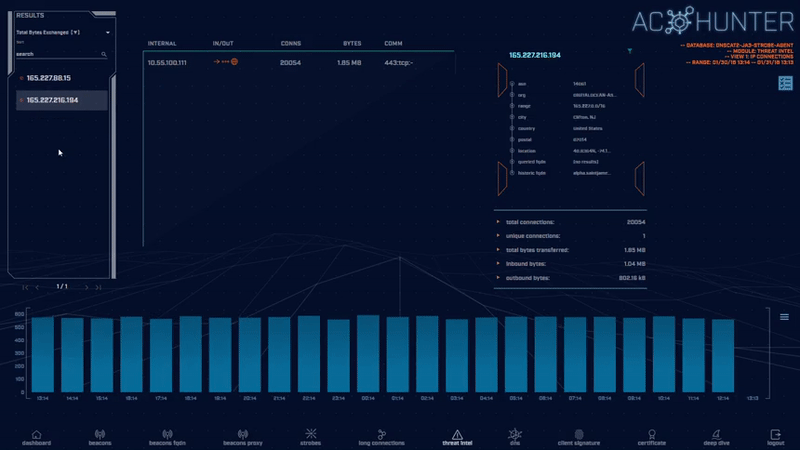
The Threat Intel module identifies when known-to-be-compromised systems are communicating with hosts on your internal network. We aggregate results from multiple threat intelligence feeds so that you have a single interface to spot highly suspect activity.
This module also displays summary information that indicates whether the threat connection is inbound or outbound, as well as the total bytes exchanged.
The threat intelligence feeds served in AC-Hunter can be user-configured to use sources of your choosing.