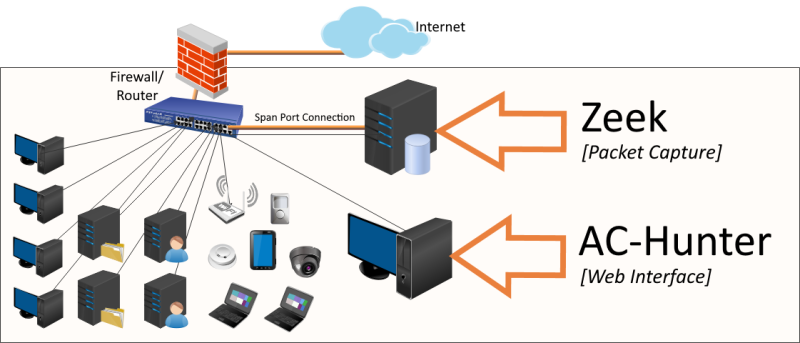
AC-Hunter – How It Works
AC-Hunter is a threat hunting software solution that provides a graphical front-end for network analysis. It is designed to simplify and expedite the process of identifying compromised systems on your network. It is a new class of security tools typically referred to as a “threat hunting analysis” tool.
- AC-Hunter utilizes two primary components; Zeek for capturing the network traffic data and AC-Hunter to analyze the data.
- AC-Hunter is designed to continuously analyze millions of network connections and is tuned to discover Command and Control (C2) channels and backdoor compromises. AC-Hunter’s analysis engine performs the first pass of a threat hunt for you. It highlights the connections that indicate one or more of your internal systems have been compromised by an external entity.
- AC-Hunter detects consistencies, patterns, and anomalies in the behavior of connections by utilizing a mixture of detection techniques that rely on attributes such as the intervals of connections, data size, dispersion, port usage, DNS queries, and advanced patented algorithms.
- AC-Hunter continuously live threat-hunts the prior 24-hours of your network data and automatically archives databases by calendar date. Concerned about what was happening on Tuesday two weeks ago? Simply load the database from that date to review the historical network data and threat analysis.
Since all network communications to and from the internet are collected at your firewall’s internal interface, AC-Hunter has visibility of all connections, regardless of the operating system, hardware, or type of device.