Version 1.2 Release

We’ve just released version 1.2 of AI-Hunter! There have been a number of tweaks and improvements, but there are three in particular that I wanted to highlight here.
Whitelist Comments and Default Recommendations
We’ve had a number of folks express that AI-Hunter’s whitelisting capability is a real time saver. This allows you to quickly weed out false positives so that they don’t appear in later threat hunts. The problem was that once you have a few dozen whitelist entries, it can be easy to lose track of why each one was created. To resolve this issue, we’ve added the ability to add comments to whitelist entries.
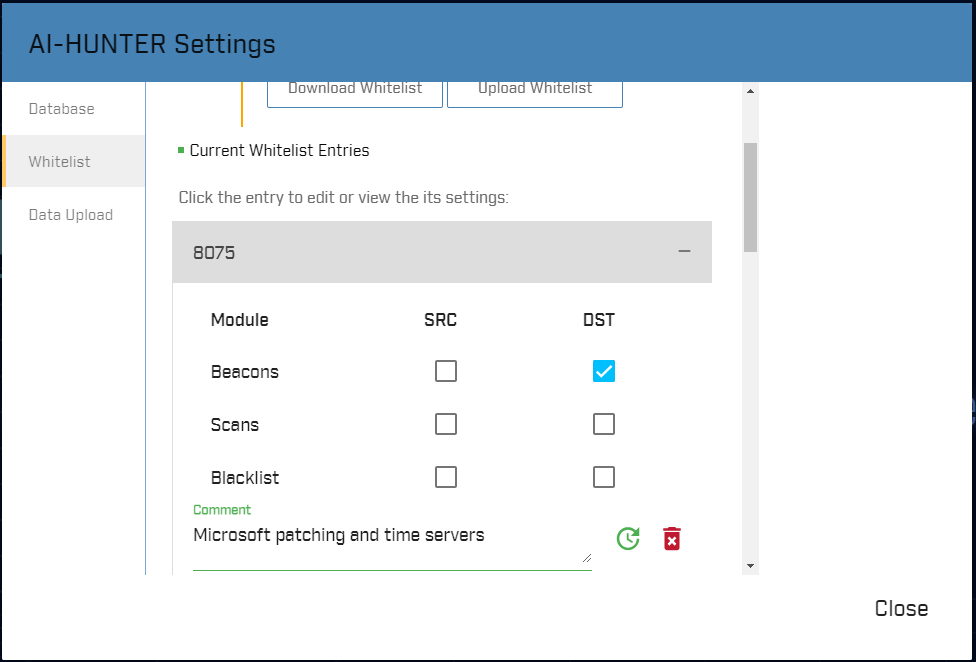
You can use the comment space to identify why the whitelist entry was created. If you need to maintain a tight audit trail, you can even reference the ticket number responsible for creating the entry. The field is free-form, so you can add whatever additional info that you need.
We’ve also started including a recommended set of whitelist entries for folks to use. This will be available as a separate download via your Portal account. This is a list of the top conditions that we’ve found which may generate false positives. If you already have a set of whitelists you are using, you can merge our defaults in with your existing list. You can also use our list as a starting point and add your own entries as needed.
Protocol IDentification
When analyzing beacon traffic, it can be extremely helpful to know what protocols and ports were being used during the communication session. In the past, you had to go back to the original Bro logs to retrieve this data. As of version 1.2, AI-Hunter now makes that info available directly in the beacons module. This should be a huge time saver!
![]()
The syntax is:
(transport / port; service)
For example, in the above screen capture, we can see that we are analyzing UDP/53 traffic, which contains DNS header information. We can also see that TCP/53 was used, but no DNS header is present. If additional protocols were used, we would see them listed here as well.
New Deep Dive Module
OK, this new feature is huge! The current modules in AI-Hunter are focused on threat vector. For example, you can check one module for beaconing behavior and another for connections that are constantly persistent. At the end of the day, however, we are looking to identify compromised systems, not necessarily threat vectors. Our new deep dive module is designed to tie all of these attack vectors together into a per system view.
Here’s an example screenshot:
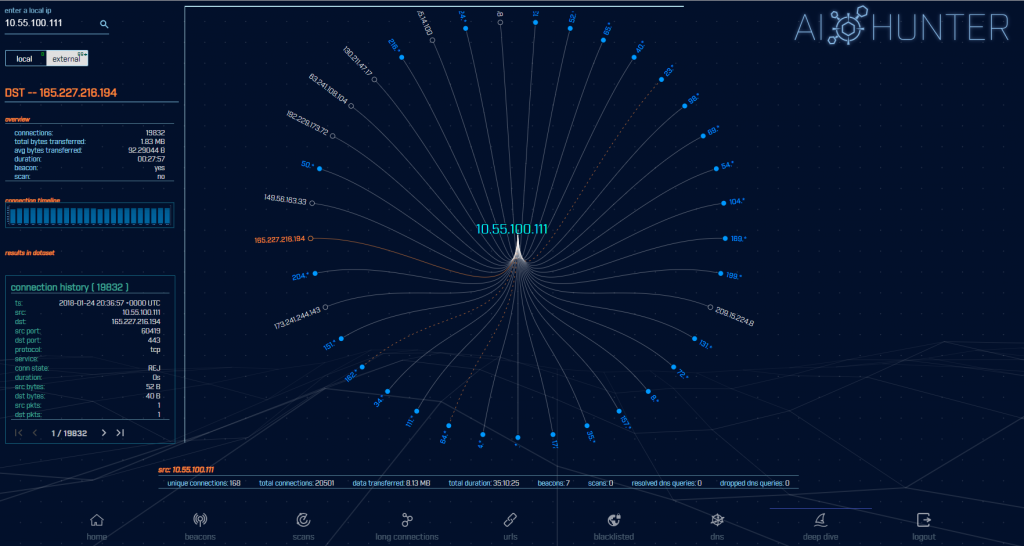
There is a lot of data to unpack here, and I plan to expand on how to use this module in later blog entries but let me run you through the highlights:
- This view is system centric. You identify the internal IP you wish to analyze and we pull together data from all of the other modules as well as additional recon info.
- The circular graphic shows all connections initiated by the system being analyzed. You can drag and zoom as needed to focus on different communication sessions.
- You can click through on specific sessions to drill down on additional details.
- The graph is color-coded to help draw your eye to potential threats.
- You can review a summary of all communications, communications between a specific destination IP, and even step through info in unique sessions, all at the same time.
In a previous blog post, I discussed the threat level rating scale and how our job as threat hunters is to move the needle as close to 0 or 100 as possible in order to disposition the session under analysis. This module is specifically designed to help you do that. By consolidating all of the data into a single view, it is now much easier to identify whether an internal system has been compromised and poses a threat to our environment.
The AI-Hunter user guide has a walkthrough on using this module, so please check that out after you upgrade. As mentioned, I’ll dig deeper into how to effectively use this module in later blog entries.
We are already working on the next release which will introduce even more goodies. Stay tuned to this channel for more info!

Chris has been a leader in the IT and security industry for over 20 years. He’s a published author of multiple security books and the primary author of the Cloud Security Alliance’s online training material. As a Fellow Instructor, Chris developed and delivered multiple courses for the SANS Institute. As an alumni of Y-Combinator, Chris has assisted multiple startups, helping them to improve their product security through continuous development and identifying their product market fit.