Malware of the Day – Cryptomining and Cryptojacking
What is Malware of the Day?
Lab Setup
“Malware”: Cryptojacking
MITRE Tactics: T1496 Resource Hijacking
Traffic Type: Generic
Connection Type: TCP
Origin of Sample: https://bitcoin.org/en/bitcoin-core/
Host Payload Delivery Method: Binary
Target Host/Victim: 10.0.0.69
Brief
Cryptomining (cryptocurrency mining) refers to contributing resources, primarily computer processing power, to verify the hashes for new blocks on a blockchain. Crypto miners are not malware but legitimate pieces of software used for transactions. In exchange for their power contribution, miners are rewarded for completing blocks in the currency built on the given blockchain. When hardware and energy are inexpensive, cryptomining can be a lucrative business. Since the code for most cryptomining programs is open-source, malicious actors can modify the code to create and distribute their own versions. In today’s traffic analysis, we look at the traffic generated by the software Bitcoin Core.
Bitcoin Core is not malware. We are using it for analysis because the traffic generated by malicious crypto miners is almost indistinguishable from their legitimate counterparts.
One instance in which power is cheap is when the energy and processing resources you are using are not your own. Cybercriminals were quick to realize this, and as a result, developed cryptojacking malware. This type of malware uses a victim machine to mine cryptocurrency and send the profits to the attackers rather than the owner of the contributing machine. While cryptojacking malware is not designed to harm the victim machine or steal data, it can, in some cases, have unintended harmful side effects.
For example, there have been many instances of Denial of Service attacks resulting from the overutilization of resources by the malware. Most cryptomining malware is widely distributed and operates as a botnet. These botnets have been rising in popularity and have even been found in military networks. Various cryptomining malware is built for and found on a wide variety of devices, including but not limited to personal laptops, cloud servers, and even game consoles.
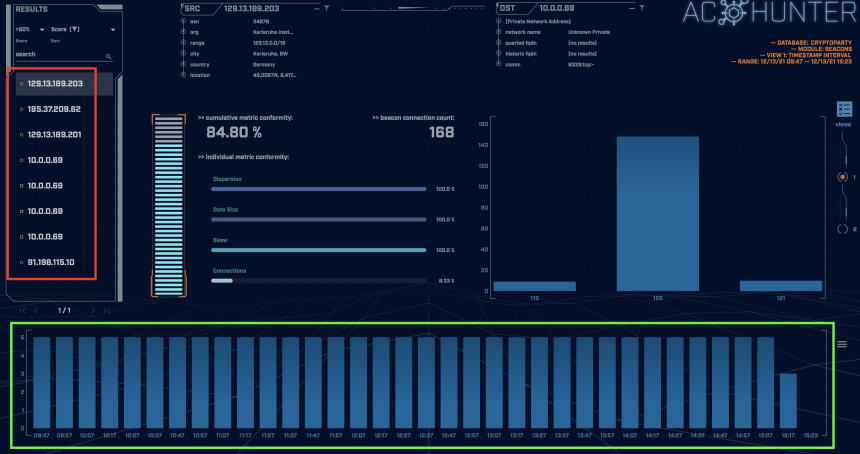
The screenshot above is taken from AC-Hunter’s beacon tab. The box highlighted in green shows the timing graph over five hours, with the interval set to 10 minutes. This is evidence of an automated network connection. If you were not aware that your computer was running a crypto miner, this would definitely be something worth investigating.
In this case, the connections (as well as many of the other top scorers highlighted in red) were made by the Bitcoin Core software. When Bitcoin Core starts, it establishes eight outbound connections to other nodes to download the latest blocks and transactions. Then, to contribute to verifying transactions, the machine will regularly accept inbound connections from other peers on the network.
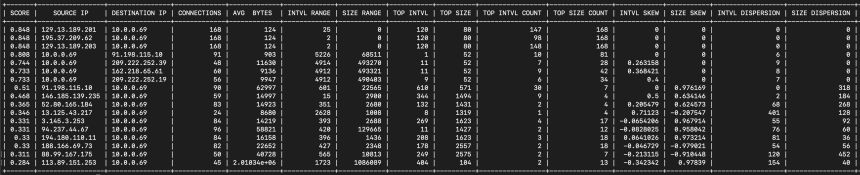
Above is the same data, but displayed by RITA, our open-source threat hunting tool, using the show-beacons command.
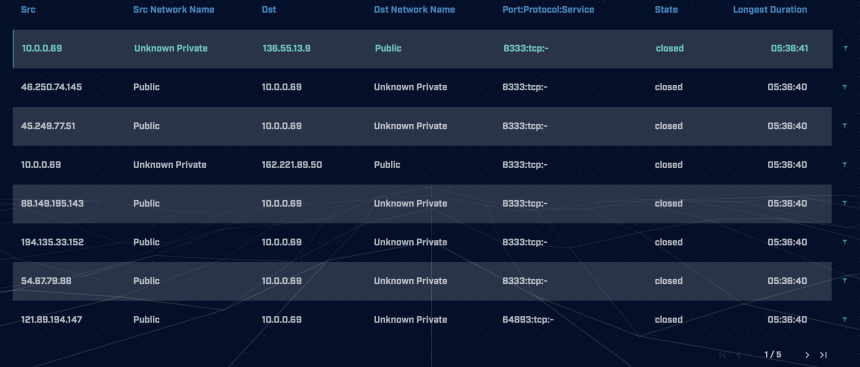
This is also very easy to see by looking at AC-Hunter’s long-connections screen. (Shown in the screenshot above). We can see all the inbound connections are using port 8333, which is our first clue that a Bitcoin Core client is running.
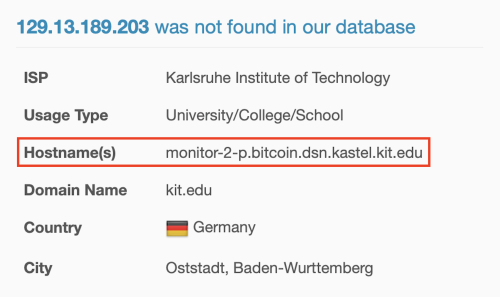
If we didn’t know what port the Bitcoin Core client connections used, we could investigate the IP addresses our machine was connecting to. AbuseIPDB and many other sites will show domains, hostnames, geolocation, etc., of any given IP address.
The screenshot above is from AbuseIPDB and shows the system’s hostname generating the connections is “monitor-2-p.bitcoin.dsn.kastel.kit.edu“. In this case, “bitcoin” in the hostname could be a clue.
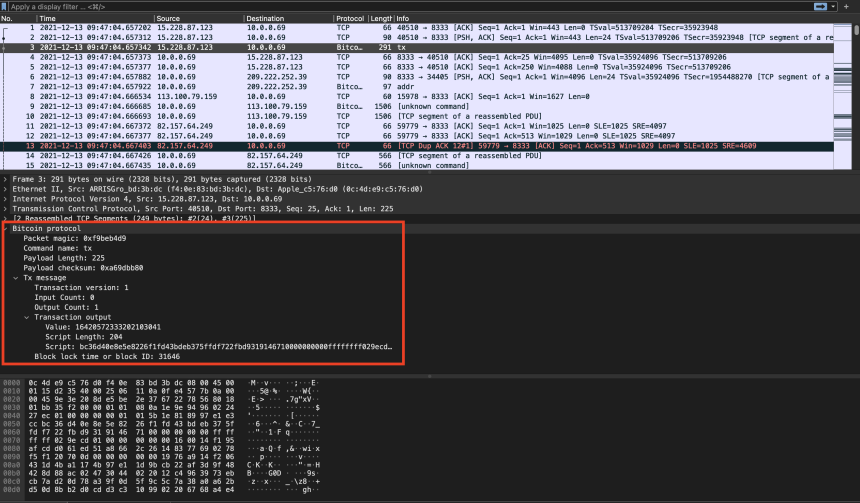
For deeper packet inspection, we turn to Wireshark. By inspecting the packets, we can see more details about the transactions, as well as the Bitcoin Protocol. The bitcoin packet highlighted is a “tx” message. It describes a bitcoin transaction and is sent in response to a “getdata” message. In total, there are 27 message types that are described in detail in the bitcoin protocol reference.
Digging further into the details of this PCAP is a task we leave to you, the reader.
We encourage you to download and use the PCAP files included below to analyze them independently using your preferred threat hunt platform to test your detection capabilities.
Capture Files
Because… PCAPs, or it didn’t happen. 😊
The following PCAP file is a packet capture taken from the same lab environment over a 5-hour timeframe. The file was generated using tcpdump from the target host and does not include normal traffic. It has been edited to remove some ipv6 traffic for privacy purposes. The PCAPs are safe, standard PCAP files and do not include any actual malware.
Cryptomining (Bitcoin Core) 5 Hour Capture
cryptomining_5hr.pcap
Size: 1.14 GB
SHA256 Checksum: AD1E736FC9C619D72F6EE8E19C499ED83D452091C95DF3E7D668B7EDE6C37C25
References
Bitcoin: https://github.com/bitcoin/bitcoin
Bitcoin Core: https://bitcoin.org/en/bitcoin-core/
Monero Botnet Article: https://www.zdnet.com/article/bug-hunter-finds-cryptocurrency-mining-botnet-on-dod-network/
Bitcoin Protocol: https://en.bitcoin.it/wiki/Protocol_documentation
Discussion
Want to talk about this or anything else concerning threat hunting? Want to share how good (or not so good) other detection tools were able to detect this sample?
You are welcome to join our Discord server titled “Threat Hunter Community” to discuss threat hunting topics. We invite you to join our server here.

Hannah joined Active Countermeasures as an intern in 2020. She is currently a graduate student at the University of Utah.