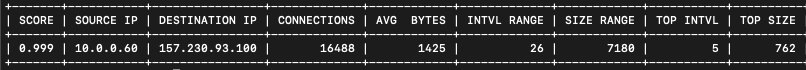Malware of the Day – Octopus
What is Malware of the Day?
Lab Setup
“Malware”: Octopus
MITRE Tactics: TA0011 Command and Control, T1082 System Information Discovery, T1124 System Time Discovery
Traffic Type: Generic
Connection Type: HTTPS
C2 Platform: Octopus
Origin of Sample: https://github.com/mhaskar/Octopus
Host Payload Delivery Method: mshta
Target Host/Victim: 10.0.0.60 – Windows 10 x64
C2 Server: 157.230.93.100
Beacon Timing: 5s
Jitter: 0%
Brief
Our focus is on identifying anomalous network activity in order to detect and respond to threats. We are using AC-Hunter/RITA as our network threat and C2 detection platform to visualize the network traffic generated from running Octopus, an open-source command and control framework written in Python3. Octopus communicates via HTTP or HTTPS to a PowerShell agent on the target machine.
Octopus is an open source tool designed with red-teamers in mind. However, any remote access tool that can be used for good, can also be used for evil. In 2020, Octopus was found being used by an APT group targeting entities in Burma. This highlights the importance of analyzing open-source tools such as this one, since any could be easily incorporated into a real offensive operation.
Octopus is described as a “pre-operation” C2 server. It is designed to be simple and stealthy, ideal for the early phases of an attack. By default, Octopus uses AES-256 to encrypt communications and if set up with the HTTPS listener, can use SSL/TLS as well.
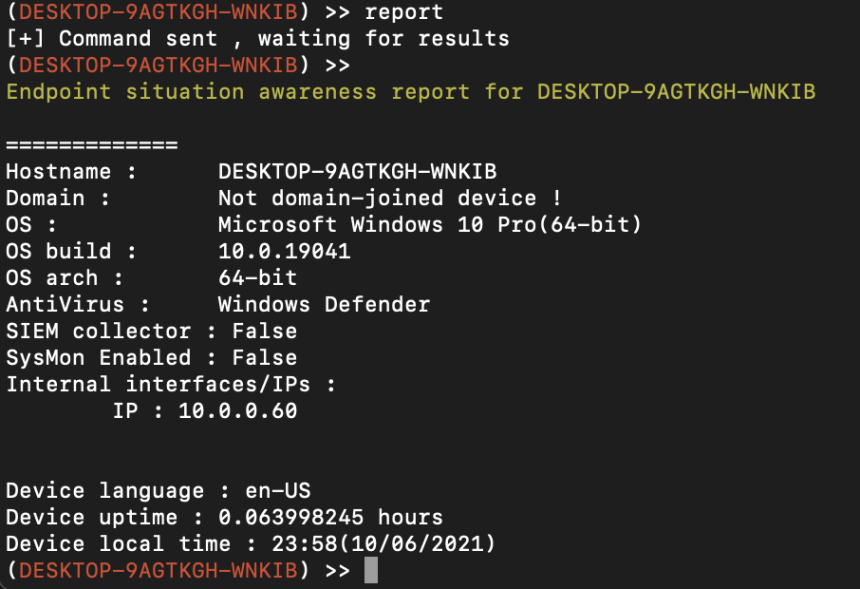
Among the open-source C2’s we have looked at, one unique thing about Octopus C2 is its Endpoint Situational Awareness (ESR) feature. This is implemented as a command that gathers important information about the compromised machine to help an adversary understand the environment they are attacking. The following screenshot shows the results of running this command on our lab machine:
The network traffic generated by Octopus C2 is very similar compared with others with beaconing C2 channels, and with the right tools is fairly easy to detect.
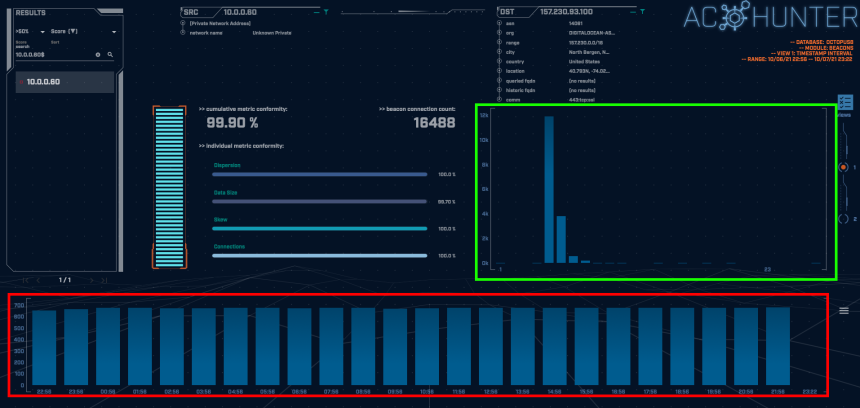
The above screenshot is taken from the AC-Hunter Beacons tab. The Octopus agent sends a beacon very frequently and does not introduce jitter which results in it receiving an extremely high beacon score of 99.9%
The timing graph highlighted in green above shows the number of connections at a given interval. Here we can see the majority of the connections are at exactly 5 second intervals. The bars trailing to the right show that some connections were around 6 to 8 seconds apart. In cases such as this one where the timing was not intentionally jittered, the variation is due to minor disturbances in the network and/or the C2 channel being actively used.
The red highlighted box above shows the number of connections per hour (each blue block represents a one-hour time frame). The consistency in connections over time is a tell-tale indicator of non-human behavior. Looking just above the timing interval graph we can see that the connection was made over port 443 using SSL. This type of connection is typically from humans when browsing the web, which is suspicious when we consider the consistency shown by the connections per hour.
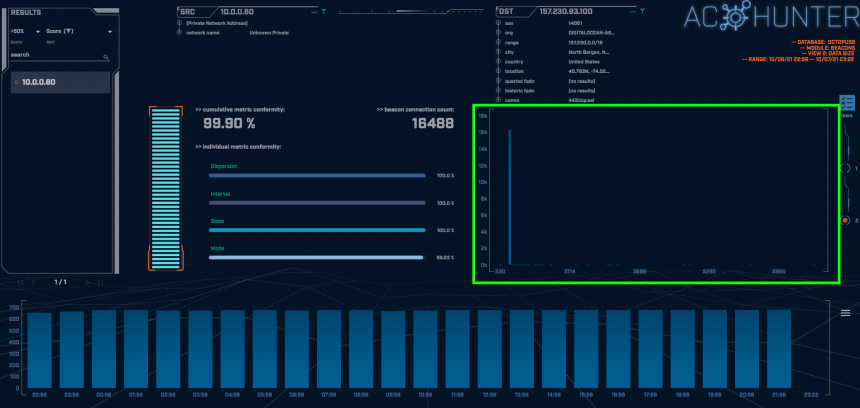
Switching to the connections data size view (shown in the green highlighted box above), we can immediately see that almost all of the individual communications are the same data size. In this case the vast majority of the connections contained 746 byte payloads which is smaller than we would expect from a legitimate HTTPS session. A normal user’s network communications should vary greatly in data size. The data size analysis is confirming these are programmed communications to be investigated.
A similar analysis can be done with our open source tool RITA using the ‘show-beacons’ command:
The low skew and dispersion metrics are representative of the conformity of the data, which suggests this is an automated connection worth investigating. We can also see the total bytes transferred between the hosts on the far right for reference.
We encourage you to download and use the PCAP files included below to analyze them independently using your preferred threat hunt platform to test your detection capabilities.
Capture Files
Because… PCAPs, or it didn’t happen. 😊
The following PCAP files are packet captures taken from the same lab environment over a 1-hour time frame and a 24-hour time frame. The files were generated using Wireshark from the target host and include normal systems OS traffic and normal network broadcast traffic. They have not been edited. The PCAPs are safe, standard PCAP files and do not include any actual malware.
Octopus 1 Hour Capture
octopus_1hr.pcap
Size: 1.39 MB
SHA256 Checksum: 7366298D4272DF14A45363025FB6927679256B5F166DE4EE84FC2EC3460B8D4C
Octopus 24 Hour Capture
octopus_24hr.pcap
Size: 31.97 MB
SHA256 Checksum: 0DDCA079134BD498B5608DCE98B2F1025579AE8D5F5A59BAFC71C7FFAB64F79C
References
https://www.anomali.com/blog/unknown-china-based-apt-targeting-myanmarese-entities
Discussion
Want to talk about this or anything else concerning threat hunting? Want to share how good (or not so good) other detection tools were able to detect this sample?
You are welcome to join our Discord server titled “Threat Hunter Community” to discuss topics surrounding threat hunting. We invite you to join our server here.

Hannah joined Active Countermeasures as an intern in 2020. She is currently a graduate student at the University of Utah.