Malware of the Day – Saefko
What is Malware of the Day?
Lab Setup
Malware: Saefko
AKA: Saefko RAT
Traffic Type: Crimeware
Connection Type: Reverse HTTP
C2 Platform: Cobalt Strike
Origin of Sample: https://github.com/xx0hcd/Malleable-C2-Profiles/blob/master/crimeware/saefko.profile
Host Payload Delivery Method: Powershell one-liner
Target Host/Victim: 192.168.99.51 – Windows 10 x64
C2 Server: 104.248.234.238
Beacon Timing: 5s
Jitter: 33%
Brief
Our focus is on identifying and detecting network beaconing behavior. We are using AI-Hunter/RITA as our network threat and C2/beacon detection platform to visualize the network traffic generated from running the Saefko malware replication. We encourage you to download and use the PCAP files included in the next section to analyze these files independently using your preferred threat hunt platform to test your detection capabilities.
This week we have a “fast” beacon of 5 second primary timing.
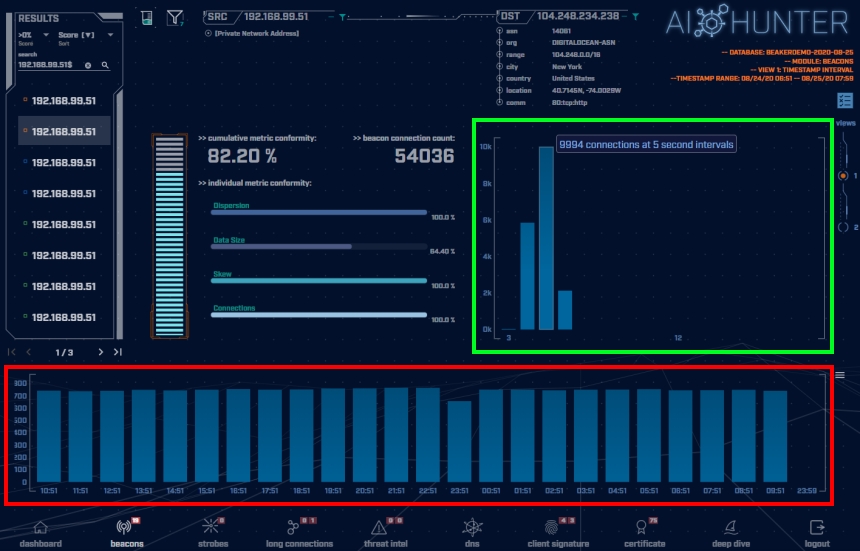
The above screenshot is taken of the AI-Hunter Beacons module from a 24-hour traffic capture. The Saefko traffic has been detected as a strong beacon signal of 82.20%.
In the green highlighted box is the beacon timing showing the number of connections of each interval of time in seconds. Here we can see a range of connection timing distributions from 3 second intervals up to 6 second intervals. Commonly, malware C2 heartbeats will have one strong signal at a particular time interval that will create an obvious peak that will stand out in a graph, even with jitter. Here we have multiple strong signals that spread out across the number of connections.
Viewing the connections timing in a graph like this we can observe the jitter that has been introduced into the timing of a deviation of 33% from 5 seconds, creating a range of intervals from 3 to 6 seconds. This amount of jitter will most likely spoof most beacon detection tools that are looking for very rigid timing patterns. These consistent clusters of connection timings are still evidence of programmed machine communications.
In the red highlighted box above are the number of connections per hour (each blue block is a one-hour time frame). The consistency of the number of connections per hour is a tell-tale indicator of non-human behavior. Notice the flatness and uniformity of the hourly histogram. Normal users’ traffic will be much more random in nature and would display greater peaks and valleys in the graph over time.
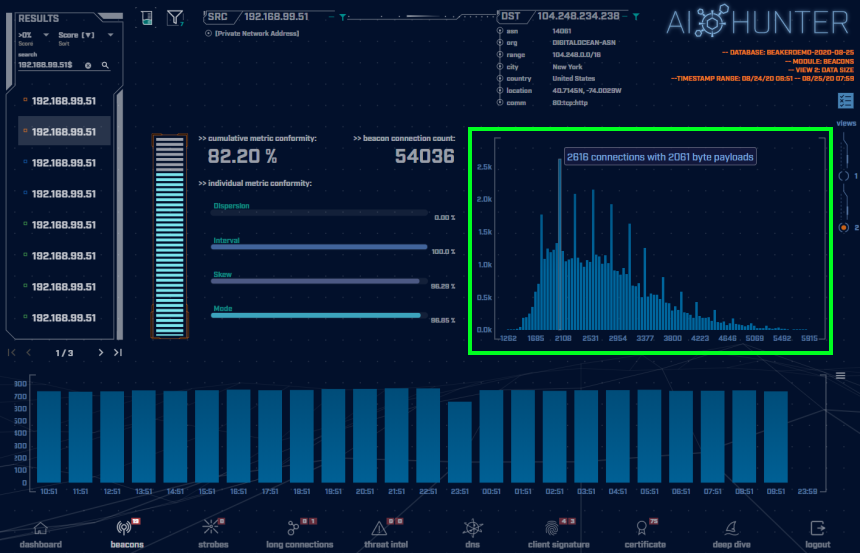
Switching to the connections data size view (shown in the green highlighted box above) is where things get a bit more interesting. Again, common malware C2 heartbeats will have one strong signal at a particular data size that will create a clear singular peak that will stand out in a graph. This is what can be referred to as the “heartbeat”. As can be seen in the above graph, the Saefko payload sizes have a broad distribution which causes the connections to appear unique and similar to normal network traffic. For this sample, the greatest number of connections of the same data size is only 2616 connections out of 54,036. This adds to the complexity of detecting the Saefko traffic.
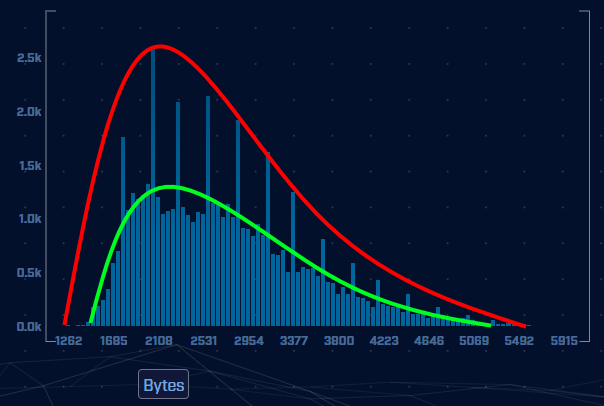
However, we can detect this as programmed communications by observing the plot of connection data sizes. Normal traffic will be truly randomized and will present the data as being scattered across the graph. Since programming languages cannot truly randomize, what will be observed from programmed randomization is pseudo-randomization. Pseudo-randomization when plotted in a graph will recurrently present itself as a bell curve. This can be clearly seen in the image above. Note how the two communal plot lines are showing a clear bell curve. This type of data size analysis is confirming these are most likely programmed communications and should be investigated.
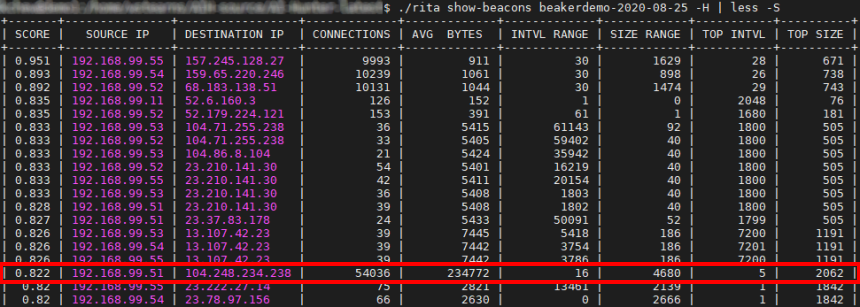
A similar beacon analysis can be performed using our open-source framework RITA ( RITA information and download page ). RITA detected the Saefko sample traffic as a strong threat, giving it a score of 0.822 (82.2% beacon/threat). The network RITA is analyzing is our malware lab and the Saefko sample is definitely a threat to be investigated.
Capture Files
Because… PCAPs, or it didn’t happen. 😊
The following PCAP files are packet captures taken from our lab environment over a one-hour time frame and a 24-hour time frame. The files were generated using Wireshark from the target host and include normal Windows OS traffic and normal network broadcast traffic. They have not been edited. The PCAPs are safe, standard PCAP files and do not include any actual malware.
Saefko 1 Hour Capture
saefko_1hr.pcap (served by Dropbox)
Size: 177 MB
MD5 Checksum: a5e3f471cf61ecc93e324f271a0a129e
Saefko 24 Hour Capture
saefko_24hr.pcap (served by Dropbox)
Size: 4.09 GB (large file, lots of beaconing)
MD5 Checksum: 8ee0dbb74ee44be45c06b912681339d2
Discussion
Want to talk about this or anything else concerning threat hunting? Want to share how good (or bad) other detection tools were able to detect this Saefko sample?
Join our Discord server titled “Threat Hunter Community” to discuss topics surrounding threat hunting. We invite you to join our server here.
Additional Resources
https://www.zscaler.com/blogs/research/saefko-new-multi-layered-rat
https://www.zdnet.com/article/new-saefko-trojan-focuses-on-stealing-your-credit-card-details/
Until the next!

Keith’s appreciation for computing and processes originates from working with his first personal computer in 1982, a TI-99/4A. Keith sees himself as fortunate for the opportunity to apply his passion towards a career that assists in the advance of technology and continuing education.