AI-Hunter v4.0 Is in the Wild!

Intro
Version 4.0 of AI-Hunter has been released! This release was packed with a lot of improvements behind the scenes, but we still have some goodies to be excited about.
New Features
More Investigation Menus!
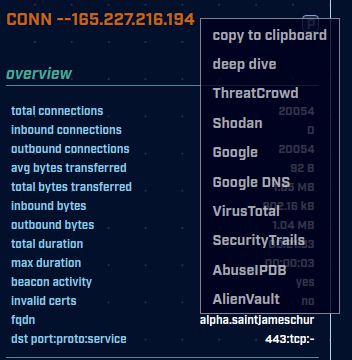
We now support investigation menus for ASN’s, FQDN’s, JA3 hashes, and UserAgent strings. These menus can be found in many more places¹, and we hope that these new menu types will aid you in your threat hunting adventures. All of these new menu types support the “copy to clipboard” functionality released in v.3.8.
We also now have dropdowns for multiple addresses! If you have a row of multiple sources, requests, or domains, each source in that row has its own submenu, allowing you to hunt each individual address.

There’s also an IP investigation menu for the CONN– IP in deepdive!
__________________
¹New Menu Locations
- ASN menus
– All modules with DST Recon (when available) - User Agent menus
– Client Signature View 1 - JA3 hash menus
– Client Signature View 2 - FQDN (Domain) menus
– Deepdive overview (when available)
– Client Signature View 1 & 2 Requests column
– DNS module Domain column
– All modules with DST Recon (when available)
– All modules with SRC Recon (when available)
– Strobes module Dst FQDN column
New Threat Intel View!
In previous versions, Threat Intel view 1) displayed outbound threats and Threat Intel view & 2) displayed inbound threats. These two separate views have now been combined into a single view! The new view displays both inbound and outbound threat intel IP connections.

There’s a new column with an icon that indicates whether the threat connection is inbound or outbound. Notice that the first IP in the table (orange) is an outbound connection, as the arrow is pointing away from the internal IP and out towards the internet. The last IP in the table (blue) is an inbound connection, as the arrow is pointing from the internet towards the internal IP. If an internal IP has both inbound and outbound connections, each connection will display in it’s own row (as shown above) since each connection can have different connection counts, bytes transferred, and comm ports.
More Items in Tables per Page!
Depending on your screen size, the tables across modules will display more items per page, reducing the number of pages you’ll need to flip through.

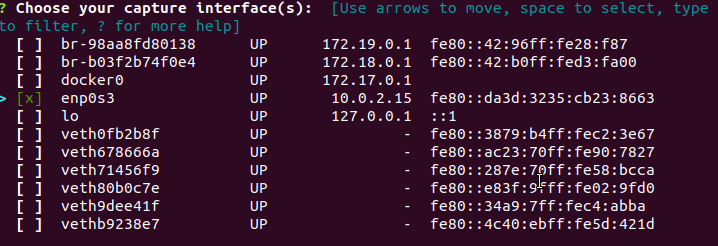
Installer Now Has a Capture Interface Selection Prompt
There’s now a much nicer selection prompt for choosing which capture interfaces you want Zeek to listen to, including interface recommendation to help clear up any confusion and avoid breaking the install.
Added Auth0 Signals as Disabled Investigation Source
Apility.io has been acquired by Auth0 and will eventually be taken down. It will be replaced with Auth0 Signals. We’ve preemptively added Auth0 Signals as a disabled source in case you’ve decided to move over to their new platform.
Potentially Breaking Changes
- Disabled external Mongo listening port as it doesn’t need to be seen by the outside world.
- Disabled TLSv1 & TLSv1.1 as these are considered insecure. Since all modern browsers support TLS v1.2 and above, this should have no effect on accessing AI-Hunter.
- Default web account credentials no longer stored in env file
- Install in /opt/AI-Hunter and link scripts in /usr/local/bin so that utilities will be accessible from anywhere.
- Cleanup deprecated scripts
– Removed `delete-databases.sh`
– Removed `rita-import.sh`
– `install_bro.sh` no longer uninstalls RITA on upgrade - Convert AI-Hunter to use Zeek, replacing the older “Bro”.
- Install Zeek init script
- Removed helpers directory
Bug Fixes
- Upgrade prompt in installer will only prompt for recent datasets
- BeakerHost entry in YAML config will not be duplicated if it already exists
- Fix bug where Beaker was inaccessible from UI if host had an IPv6 address.
- Fixed sorting in strobes
- Fixed miscellaneous sorting issues
- Fixed bug where dns threshold wasn’t cleared when visiting another page
Wrap Up
All current customers can access the new version via their Portal account. Please be sure to check the release notes for install instructions. If you have any problems, do not hesitate to reach out to our support team.
Not an AI-Hunter user yet? See a rundown of how AI-Hunter works, schedule a personal demo, or check out AI-Hunter purchase details.

Naomi Kramer is a senior at Dakota State University majoring in Computer Science.
She has been working in software development for three years and specializes in modern full-stack web development.
Her interests include oil painting, graphic design, Swedish ciders, paddleboarding, and adventuring with her two Siberian Huskies.