Port Forwarding With VirtualBox

This blog post assumes that you are running the latest version of VirtualBox, which at the time of this writing is version 7.0.6. You can check the version by going to Help → About.
The goal of this blog will be to set up port forwarding so that open ports on your VM can be accessed from the host system. The VM needs to be shut down prior to performing these steps.
Highlight the VM you will be working with and select Settings → Network. You should see the network adapter screen.
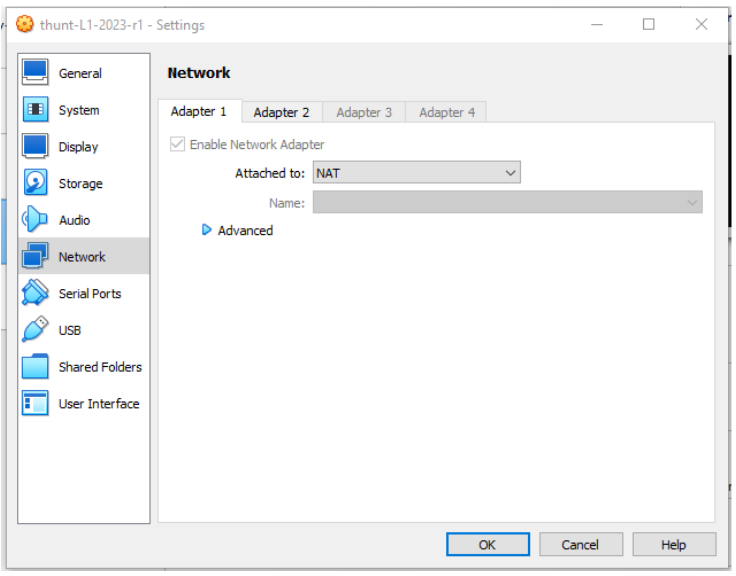
The “Adapter 1” tab should be showing. Verify that the “Attached to” field is set to “NAT”. Now, click the Advanced drop down and then click the Port Forwarding button.
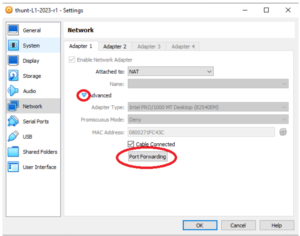
With port forwarding, we effectively make a “tunnel” from a port on the host system to a port on the VM. When you access the port on the host, your traffic will automatically get forwarded to the defined port on the VM.
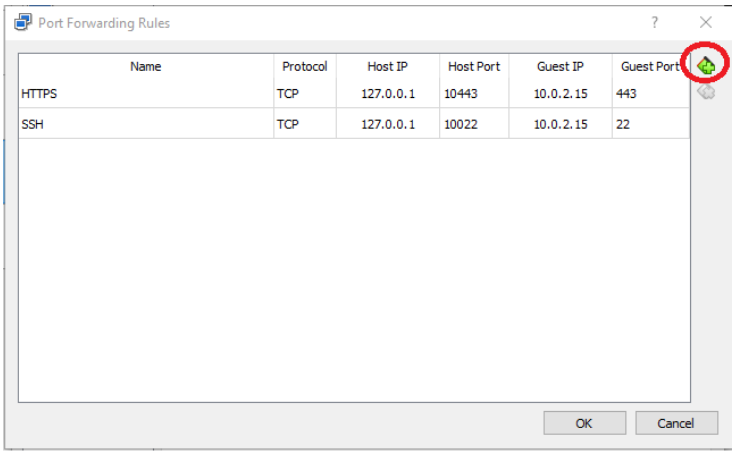
We are going to create two entries, one for SSH and another for HTTPS. Click the green plus symbol on the right, and create two entries using the following values:
Name: HTTPS
Protocol: TCP
Host IP: 127.0.0.1
Host Port: <A port not in use on the host, 10443 or similar>
Guest IP: <IP assigned to VM, usually 10.0.2.15>
Guest Port: 443
Name: SSH
Protocol: TCP
Host IP: 127.0.0.1
Host Port: <A port not in use on the host, 10022 or similar>
Guest IP: <IP assigned to VM, usually 10.0.2.15>
Guest Port: 22
Your port forwarding rules should look like this:
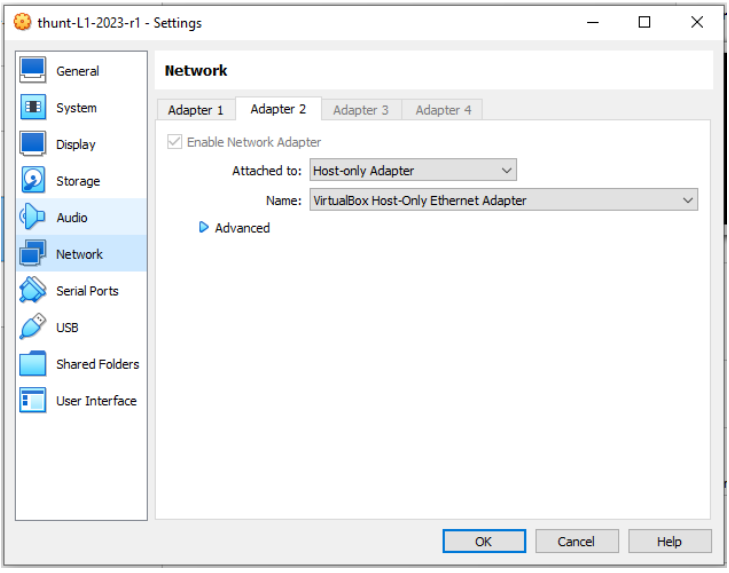
Click the “Adapter 2” tab. Enable this adapter and set the “Attached to” field to be “Host-only Adapter”.
Once complete, click the “OK” button. You can now start up the VM. Once the VM boots, you should be able to access SSH and HTTPS via the loopback address. For example, if I used the same “Host Port” defined above, I can point my Web browser at:
and connect to the Web server running on the VM. If I SSH to:
ssh [email protected]:10022
I’ll connect to the SSH server running on the VM.

Chris has been a leader in the IT and security industry for over 20 years. He’s a published author of multiple security books and the primary author of the Cloud Security Alliance’s online training material. As a Fellow Instructor, Chris developed and delivered multiple courses for the SANS Institute. As an alumni of Y-Combinator, Chris has assisted multiple startups, helping them to improve their product security through continuous development and identifying their product market fit.