Version 2.0 Released

Hi folks!
We are proud to announce that version 2.0 of AI-Hunter has just been released. This update is a major change to the way you use the product, and it is focused on simplifying and expediting the threat hunting process.
In the past, we’ve given you all the tools you need to identify compromised systems calling home to their command and control servers. This required a bit of skill on your part, as you would need to know what tell tale signs to hunt for. As of version 2.0, we do the first pass at a threat hunt for you.
Here’s the new home screen:
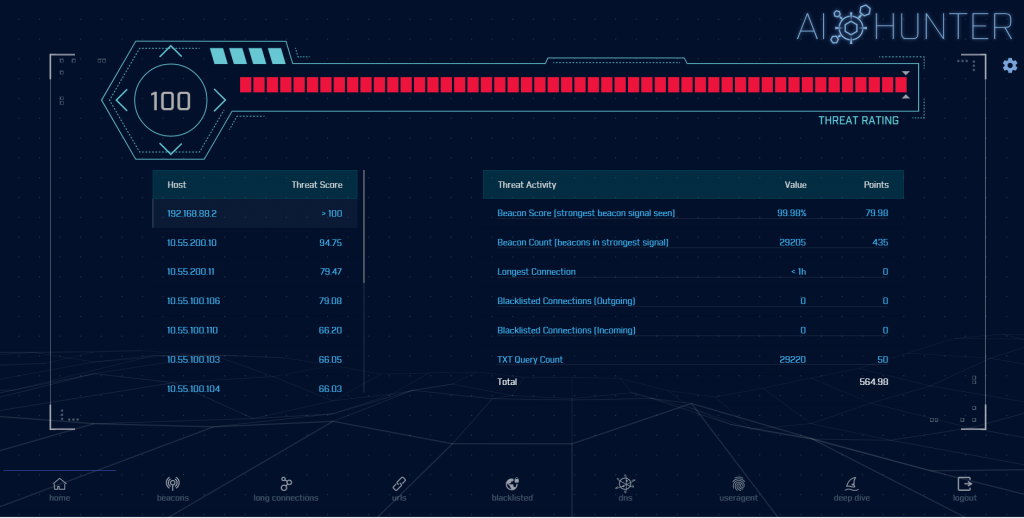
The panel on the left hand side identifies which internal IP addresses are the greatest suspect of compromise, score ranked from highest to lowest. Think of this as your action item list. Just start at the top and work your way down. The closer the threat score is to 100, the greater the chance you have a situation that needs to be mitigated.
The panel on the right is the details on how we derived the threat score. For example, if we see strong beacon activity and thousands of beacons per day, the score is going to go up significantly. All of the threat activity items are clickable, so you can drill down into the data yourself to verify our findings.
This is just the beginning. With this framework in place, we have a lot more changes moving through Engineering that will dramatically improve the accuracy of the threat score. We plan to have AI-Hunter perform even more of the threat hunting process for you. Stay tuned for the next release!

Chris has been a leader in the IT and security industry for over 20 years. He’s a published author of multiple security books and the primary author of the Cloud Security Alliance’s online training material. As a Fellow Instructor, Chris developed and delivered multiple courses for the SANS Institute. As an alumni of Y-Combinator, Chris has assisted multiple startups, helping them to improve their product security through continuous development and identifying their product market fit.