DNS Backdoors?

There has been a lot of confusion about DNS backdoors and how hard they are or ar not to detect. I wanted to do a quick run-through on what they are and how we can detect them using some free and open source software.
A little bit of background. DNS is like the technical phone book of the Internet. When you put in www.activecountermeasures.com in your browser, your system has no idea what that is. It has to convert it to a number, much like converting a business or person to a phone number. Your computer will then ask a local DNS server to look this number up on the user’s behalf.

Because taking directions from random strangers is never bad.
https://www.youtube.com/watch?v=zfmZSiFlgKU
Then the local DNS server will go online and look up the IP address, sometimes going to multiple DNS servers to find the answer. I don’t want to do a full walkthrough of a DNS lookup here. But, the important thing to remember, is that when your local DNS server gets the answer for www.activecountermeasures.com it will then cache the IP address for a period of time. That way, when any other systems look up the same address, it will pull its local cache and give that answer forgoing the full lookup on the Internet.
When attackers use DNS as a backdoor C2 there are a couple of really cool advantages in their favor. First, DNS is often allowed out of sensitive network segments when everything else is blocked. Second, the connection to lookup an IP address rarely goes directly to an evil server. Some other DNS server performing recursion on the implants behalf does. For example, an internal system can have malware that does DNS lookups to Google’s DNS server (8.8.8.8). All of the C2 traffic will look like it is coming from Google. And, Google’s motto is don’t be evil…

Well. At least it was..
However, we can detect it.
For example, Real Intelligence Threat Analytics (RITA) does an exploded DNS view. This allows you to see how many subdomains were observed for a domain, then, rank them in order from most to least. For example, in www.google.com, www is the subdomain. Some domains (like Google) will have lots of subdomains.
However, for a malicious C2 DNS channel there will be even more…. Like a lot more. This is because of caching. We cannot use a DNS lookup for or C2 which is always www.evil-c2.com. This is because, after the first request, the cached answer will always come back from the local DNS server. So, if we were to use a DNS backdoor it would have to generate a separate subdomain for every request. Below is a screenshot from RITA showing what that looks like.
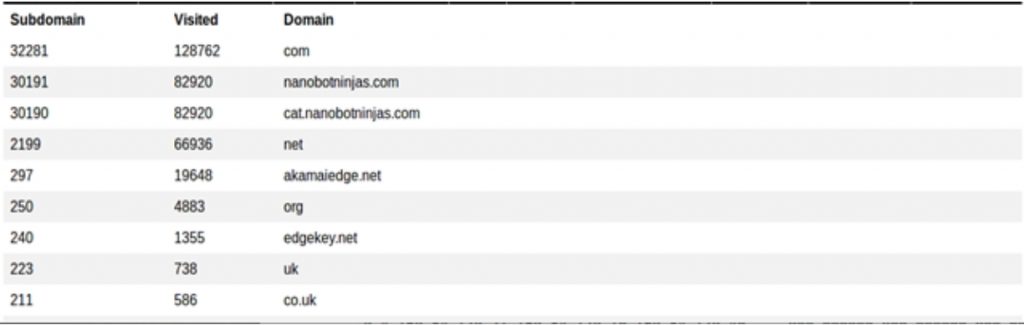
Notice that nanobotninjas.com has 30191 subdomains? Yea, that is not normal. And RITA pulls that information and sorts it.
If we wanted to see the raw Bro logs to see what was going on, we just need to do a little grepping.
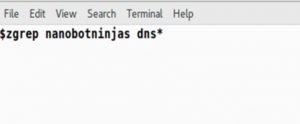
For the above example, I am using zgrep which allows us to grep inside of compressed Bro files.
And below is what we get:
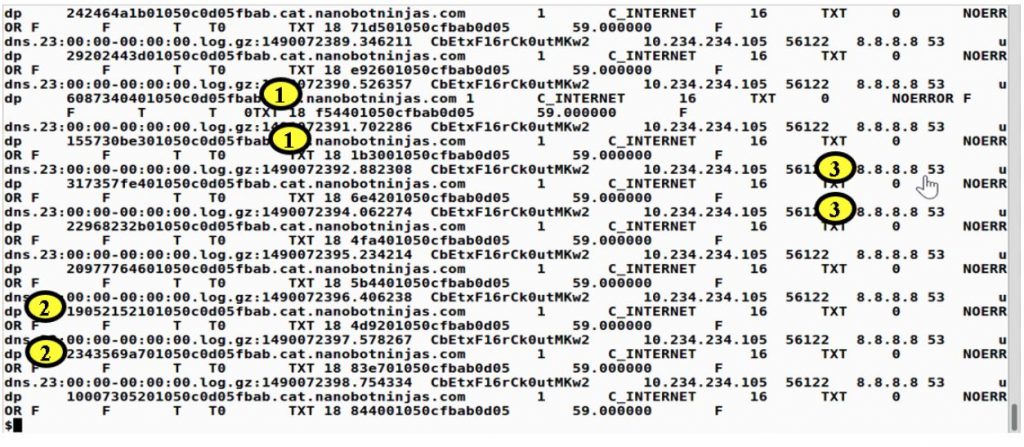
Notice in the (1) sections there is the suspect domain, nanobotninjas.com. Notice in the (2) we have the random subdomains. And finally, in the (3) notice the remote server is 8.8.8.8. Google’s DNS server.
I hope this post helps clear up DNS backdoors and how to catch them.
Below are the tools I used for this post.
https://github.com/activecm/rita
https://github.com/iagox86/dnscat2
Thanks!
John

John has both consulted and taught hundreds of organizations in the areas of security, regulatory compliance, and penetration testing. He is a coveted speaker and much loved SANS teacher. John is a contributor to the industry shaping Penetration Testing Execution Standard and 20 Critical Controls frameworks.