Malware of the Day – APT1 Virtually There
What is Malware of the Day?
Lab Setup
Malware: APT1 Virtually There
AKA: APT1 Virtuallythere, APT1 Virtuallythere SSL, APT1
Traffic Type: APT
Connection Type: Reverse HTTPS
C2 Platform: Cobalt Strike
Origin of Sample: https://github.com/rsmudge/Malleable-C2-Profiles/blob/master/APT/apt1_virtuallythere.profile
Host Payload Delivery Method: Powershell one-liner
Target Host/Victim: 192.168.99.55 – Windows 10 x64
C2 Server: 157.245.128.27
Beacon Timing: 60s
Jitter: 0%
Brief
Our focus is on identifying and detecting network beaconing behavior. We are using AI-Hunter/RITA as our network threat and C2/beacon detection platform to visualize the network traffic generated from running the APT1 Virtually There malware replication. We encourage you to download and use the PCAP files included in the next section to analyze them independently using your preferred threat hunt platform to test your detection capabilities.
This week we are looking at APT1 Virtually There, one of the many strains and methods of malware used by the APT1 group. The beaconing behavior of this sample is not necessarily a direct representation of traffic observed from the original C2 communications used by APT1, it is purely an example 60 second beacon with zero jitter. The focal point of this sample is to observe the correlation between beaconing communications using the HTTPS protocol and the SSL certificates used.
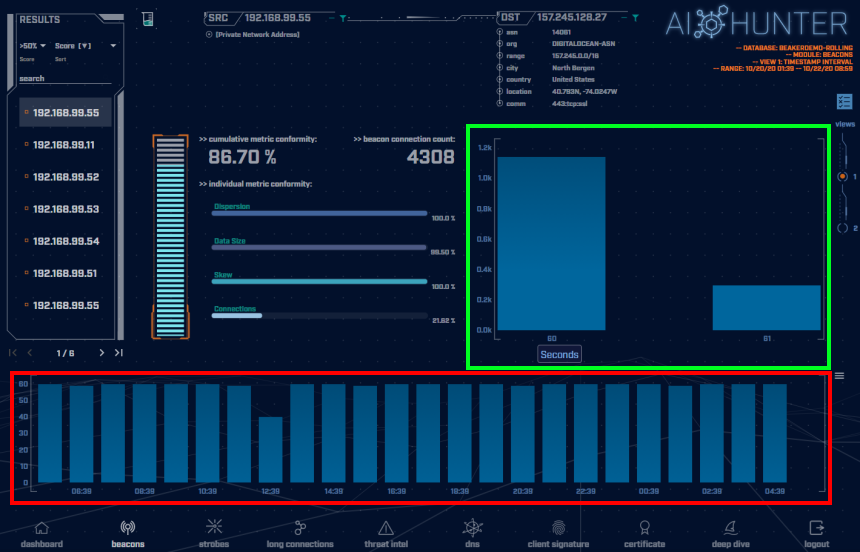
The above screenshot is taken of the AI-Hunter Beacons module from a 24-hour traffic capture. The APT1 Virtually There traffic has been detected as a strong beacon signal of 86.70%.
In the green highlighted box is the beacon timing showing the number of connections of each interval of time in seconds. Here we can see the majority of the connection timing distributions are 60 second intervals. We have some outliers at 61 second intervals, however, those can be contributed to slight time stamping variations, communication or network delays. This confirms our beacon timing is rigid.
In the red highlighted box above are the number of connections per hour (each blue block is a one-hour time frame). The consistency of the number of connections per hour is a tell-tale indicator of non-human behavior. Notice the flatness and uniformity of the hourly histogram. Normal users’ traffic will be much more random in nature and would display greater peaks and valleys in the graph over time.
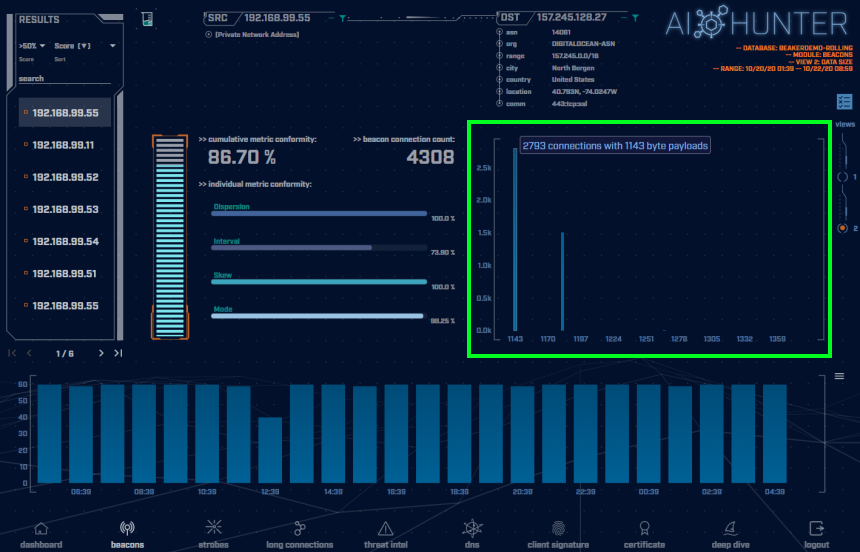
Switching to the connections data size view (shown in the green highlighted box above), we can immediately see the majority of communications are the same data size. For this sample, we have a total of 4308 connections. 2793 of them with 1143 byte payloads. This is obviously uniform and structured communications and is a solid representation of a potential C2 channel “heartbeat” of checking in for marching orders or to maintain persistence.
Normal users’ network communications will vary greatly in data size. The data size analysis is confirming these are programmed communications to be investigated.
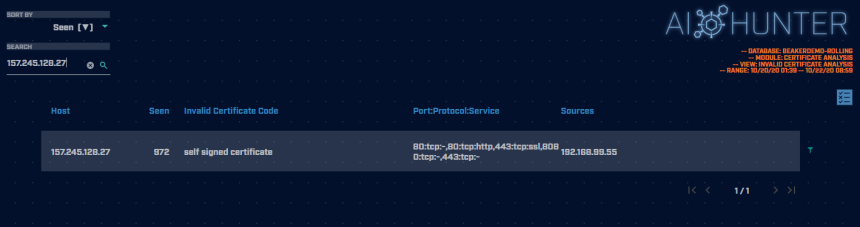
Switching to the Certificates module and searching for our destination IP shows us the SSL certificate being used is self signed which is an indicator of weak security properties. Most credible and reputable public servers will be using a SSL certificate that is signed by a certificate authority (CA). When analyzing communication behaviors looking for abnormal or unexpected network traffic, this is another piece of our puzzle that just doesn’t fit right and adds more weight leaning us towards this as being a potentially malicious communication session.
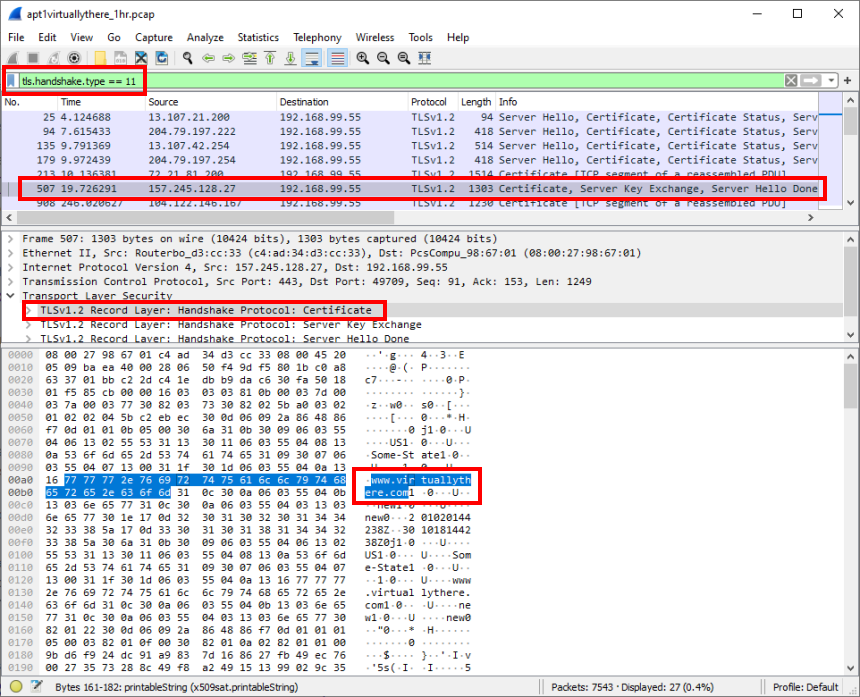
Inspecting the initial TLS handshake in Wireshark, using the ‘apt1virtuallythere_1hr.pcap’ file below, we can view the SSL certificate details:
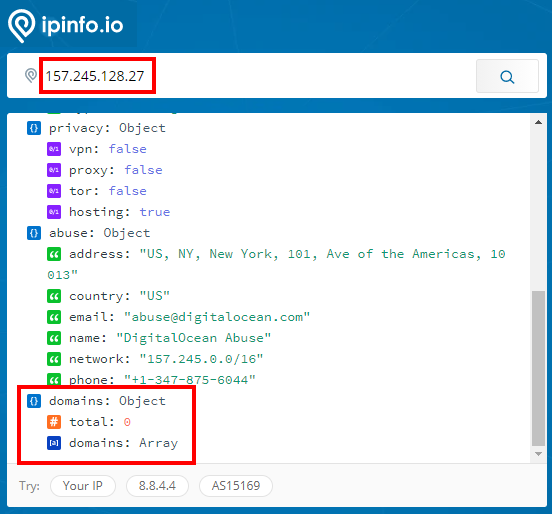
Okay, this is just strange. The certificate is claiming to be associated with www.virtuallythere.com. If this were true, we would see the fully qualified domain name (FQDN) displayed in AI-Hunter associated with 157.245.128.27. We see no FQDN information associated with this destination IP.
A quick online check using ipinfo.io of our destination IP (157.245.128.27) that is serving this certificate shows there are no domains associated with this IP:
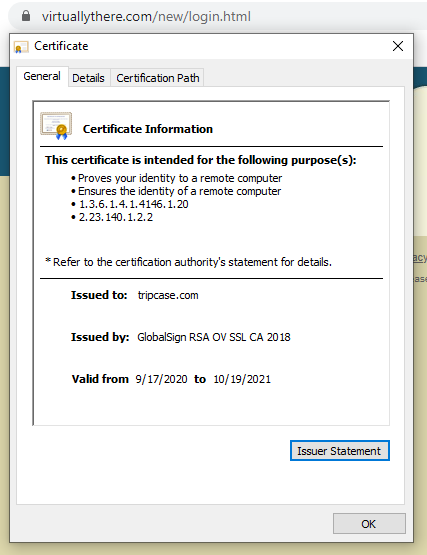
Browsing to the domain of www.virtuallythere.com (which I don’t recommend doing unless you are certain the domain is not malicious. In this case it has been confirmed it is a valid business) and checking the certificate in a browser, we can see the actual certificate being used by the domain in question is issued by a valid CA (GlobalSign):
The certificate in question being served from 157.245.128.27 is not a valid certificate.
The above is a quick and very basic certificate investigation. There are many other methods and tools available to perform a more thorough investigation.
The bottom line is; when investigating unknown encrypted traffic you will not be able to inspect the communication itself, as it is encrypted, but you can at least verify it is using proper TLS protocols and the SSL certificate being used is the first and easiest place to start your investigation.
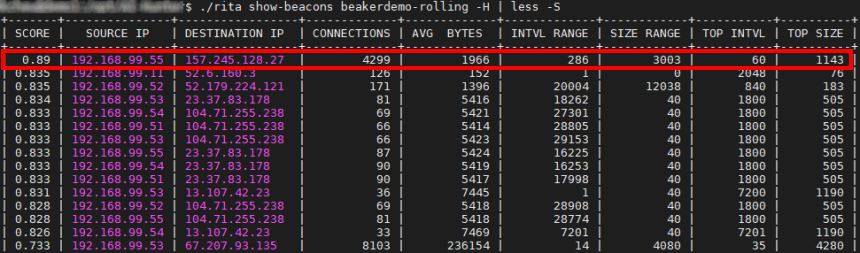
A similar beacon analysis can be performed using our open-source framework for network traffic analysis, RITA (Real Intelligence Threat Analytics). RITA detected the APT1 Virtually There sample traffic as a very strong threat, giving it a score of 0.89 (89.0% beacon/threat score). The network RITA is analyzing here is a malware lab and the APT1 Virtually There sample is definitely a threat to be investigated.
Capture Files
Because… PCAPs, or it didn’t happen. 😊
The AI-Hunter and RITA results above are a 24-hour observation and analysis from Zeek logs running in a lab 24/7. The following PCAP files are packet captures taken from the same lab environment over a one-hour time frame and a 24-hour time frame. The files were generated using Wireshark from the target host and include normal Windows OS traffic and normal network broadcast traffic. They have not been edited. The PCAPs are safe, standard PCAP files and do not include any actual malware.
Note: Only the 1hr PCAP has the initial SSL handshake and certificate.
APT1 Virtually There 1 Hour Capture
apt1virtuallythere_1hr.pcap
Size: 1.85 MB
MD5 Checksum: 32417bf3c7469c27359adf4dcb519627
APT1 Virtually There 24 Hour Capture
apt1virtuallythere_24hr.pcap
Size: 108.96 MB
MD5 Checksum: 1e1824d26122159683d3d71d2a65ba6f
Discussion
Want to talk about this or anything else concerning threat hunting? Want to share how good (or not so good) other detection tools were able to detect this APT1 Virtually There sample?
You are welcome to join our Discord server titled “Threat Hunter Community” to discuss topics surrounding threat hunting. We invite you to join our server here.
Additional Resources
https://attack.mitre.org/groups/G0006/
https://otx.alienvault.com/pulse/5e135cdde24c50bb2b54d2c2
https://vulners.com/nessus/SSL_APT1.NASL
Until the next!

Keith’s appreciation for computing and processes originates from working with his first personal computer in 1982, a TI-99/4A. Keith sees himself as fortunate for the opportunity to apply his passion towards a career that assists in the advance of technology and continuing education.