Malware of the Day – Mythic – Apollo
What is Malware of the Day?
Lab Setup
“Malware”: Apollo (https://github.com/MythicAgents/Apollo)
MITRE Tactics: TA0011 Command and Control, T1056.001 Keylogging, T1055 Process Injection, T1573 Encrypted Channel
Traffic Type: Generic
Connection Type: HTTP
C2 Platform: Mythic
Origin of Sample: https://github.com/its-a-feature/Mythic
Host Payload Delivery Method: Windows Executable
Target Host/Victim: 10.0.0.60 – Windows 10 x64
C2 Server: 157.230.93.100
Beacon Timing: 10s
Jitter: 23%
Brief
Our focus is on identifying anomalous network activity in order to detect and respond to threats. Today we are using AC-Hunter/RITA as our network threat and C2 detection platform to visualize the network traffic generated from running Mythic C2. We encourage you to download and use the PCAP files included in the next section to analyze them independently using your preferred threat hunt platform to test your detection capabilities.
Mythic (formerly Apfell) is an open source C2 framework that supports a variety of payloads. It provides a highly sophisticated Web UI for read-teamers (or whomever else installs the program) to interact with a victim computer:
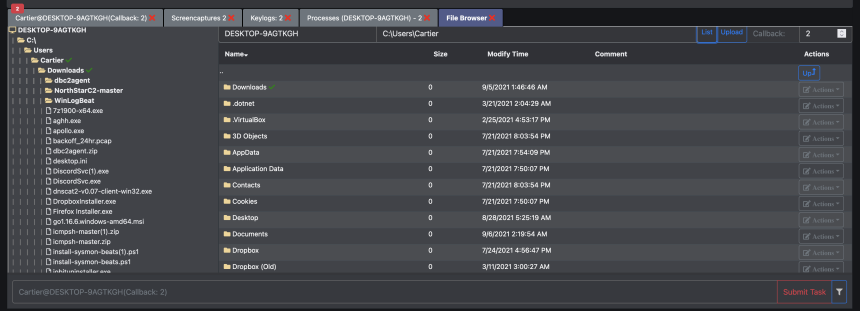
The above two screenshots are taken from the Mythic web interface. This is an example of some of what an adversary could see once they get an implant on a target machine. The first screenshot depicts the file browser which the adversary can use to browse the directory structure, upload/download or delete files.
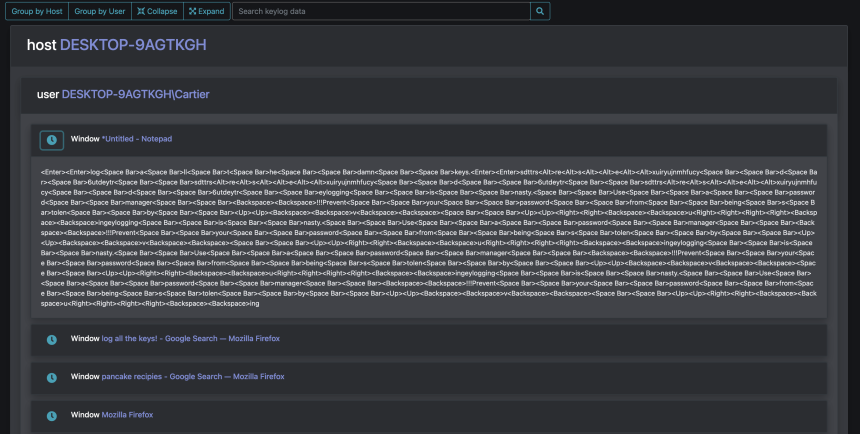
The second screenshot is from the Keylogs tab in the Mythic web interface. The Apollo payload used to compromise the machine allows the adversary to inject a keylogger into a running process. Process Injection is a sneaky way to fly under the radar by executing code in the address space of a legitimate process. After choosing a process ID and sending a short command to the target machine, the target will begin recording the users keystrokes and periodically sending them to the C2 server as displayed here. Any idea what was being typed in Notepad?
Now that we’ve seen what an adversary can see, here’s what you’ve all been waiting for, what we can see… the network traffic:
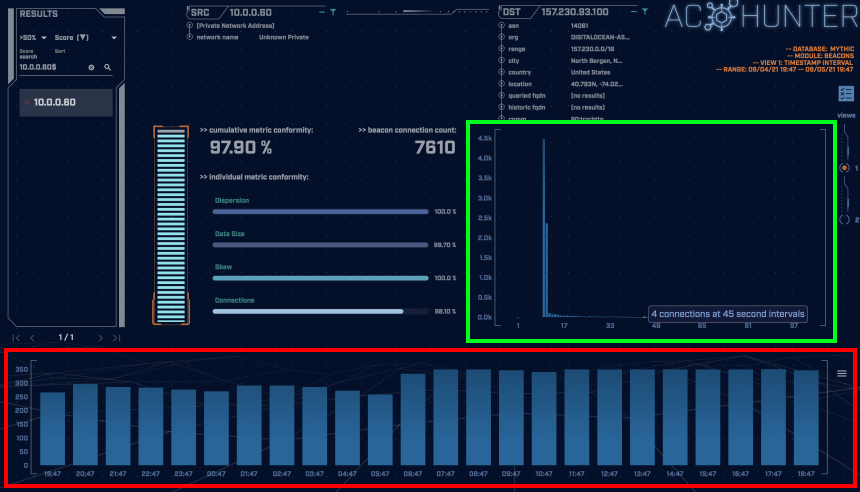
Above, taken from the AC-Hunter beacons module, and looking at the connection histogram on the bottom (highlighted in red) shows the number of connections per hour. The consistency of connections and the relatively high consistent number of connections per hour suggest that this is an automated program. There is also a fair amount of jitter introduced, depicted by the shallow peaks and valleys of the peak line. We can see an uptick in the middle of the graph at approximately 06:47; this suggests that the adversary began interacting with the channel at that time. In this case, it likely corresponds with the keylogger being activated.
The graph above (highlighted in green) shows connection time intervals on the x-axis, and number of connections on the y-axis. The majority of these connections are at 10 second intervals.
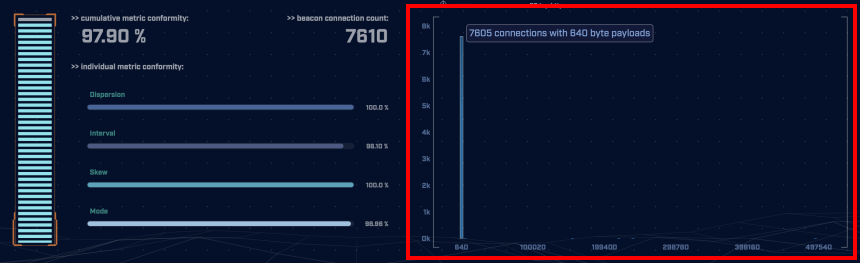
Zooming in on the data size graph above, we can clearly see the heartbeat of the C2 channel. Normal users’ network communications should vary greatly in data size. Worth noting within this graph is the much smaller scattered bars near the bottom representing outlying connections with much higher data sizes than the heartbeat, which is another indicator of varying interaction with the C2 channel.
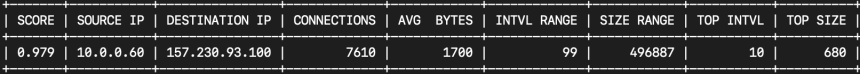
AC-Hunter identifies these communications as a very high probability of a potential threat, given a 97.90% beacon score.
A similar beacon analysis can be performed using our open-source framework for network traffic analysis, RITA:
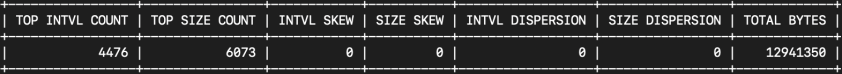
RITA shows a 97.9% beaconing score for this IP pair, as well as some statistical analysis on the data transfer. Especially worth paying attention to is the Average Bytes and the Dispersion. The dispersion being close to zero (this is a tad rounded) indicates a continuous uniform connection.
It is tempting at this point to dig into the full packet captures and see if we can figure out what the attacker was doing. We saw in AC-Hunter/RITA that the HTTP protocol was used so it’s possible data was transferred over plain text.
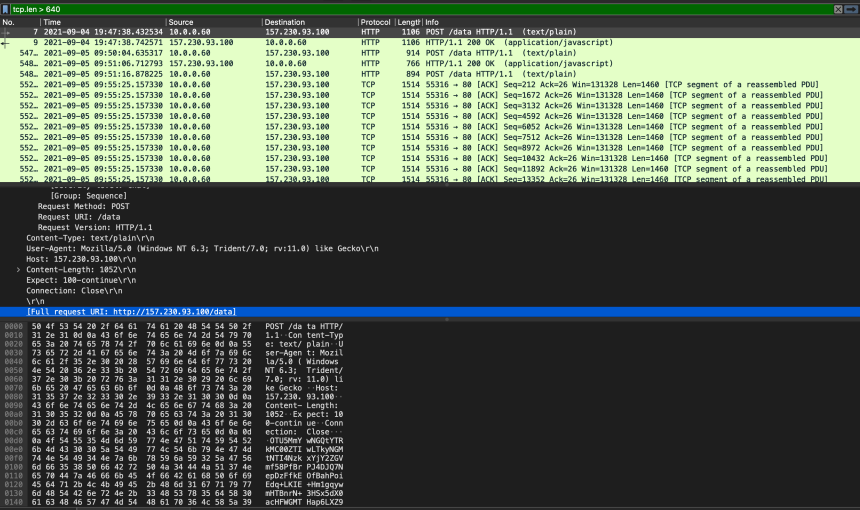
The screenshot above shows the packet capture opened in Wireshark. Earlier we learned that the heartbeat of the beacon had a 640 byte payload so we filtered for TCP segments larger than that using the filter “tcp.len > 640”. Looking at some of the packets we can see HTTP POST requests made to ‘http://157.230.93.100/data’. Visiting this page in a web browser (safely, in an isolated VM or “disposable” isolated system with limited networking) is a one potential way to verify that this is not a legitimate content-serving site (In this case it will no longer exist by the time you are reading this). The Apollo payload sends AES256 + HMAC encrypted data to the server which means payload analysis will not be possible.
We encourage you to download and use the PCAP files included below to analyze them independently using your preferred threat hunt platform to test your detection capabilities.
Capture Files
Because… PCAPs, or it didn’t happen. 😊
The following PCAP files are packet captures taken from the same lab environment over a 1-hour time frame and a 24-hour time frame. The files were generated using Wireshark from the target host and include normal systems OS traffic and normal network broadcast traffic. They have not been edited. The PCAPs are safe, standard PCAP files and do not include any actual malware.
Mythic 1 Hour Capture
mythic_1hr.pcap
Size: 66.62 KB
SHA256 Checksum: 5FF60C6A33A443B9D2735A625EE0107075D20FA8D4BE76BDAE47C4835C6A0841
Mythic 24 Hour Capture
mythic_24hr.pcap
Size: 15.46 MB
SHA256 Checksum: 6AB5B6F423A77FF43E87F1C37262474264DBE0CCA908254333891B8E83CEC31D
Discussion
Want to talk about this or anything else concerning threat hunting? Want to share how good (or not so good) other detection tools were able to detect this sample?
You are welcome to join our Discord server titled “Threat Hunter Community” to discuss topics surrounding threat hunting. We invite you to join our server here.

Hannah joined Active Countermeasures as an intern in 2020. She is currently a graduate student at the University of Utah.