Malware of the Day – Who Started This? Threat Hunting Meets SIEM
What is Malware of the Day?
Lab Setup
“Malware”: PoshC2 Beacon
Traffic Type: Reverse HTTPS
MITRE Tactics: TA0011 Command and Control
Connection Type: HTTPS
C2 Platform: PoshC2
Origin of Sample: https://github.com/nettitude/PoshC2
Host Payload Delivery Method: Executable (EXE)
Target Host/Victim: 10.0.0.64 – Windows 10 x64
C2 Server: 157.230.93.100
Beacon Timing: 120s
Jitter: 0%
Brief
Our focus is on identifying and detecting network beaconing behavior. In today’s post, Threat Hunting Meets SIEM, we are investigating the network traffic generated by PoshC2 as well as demonstrating how our open-source tool BeaKer can be used to further our investigation. We are using AC-Hunter/RITA as our network threat and C2 beacon detection platform to visualize the network traffic generated from running the open-source command and control server PoshC2.
The first step to classifying potentially malicious network connections is determining that a given connection could be actually malicious. Sometimes finding threats can be straightforward to classify. For example, is one of your endpoints sending packets off on a regular basis to an IP or domain based in a country or region where you do not have a business relationship or legitimate need? That may be malicious. Most of the time however, it is not that easy to tell which traffic is legitimate and which is not.
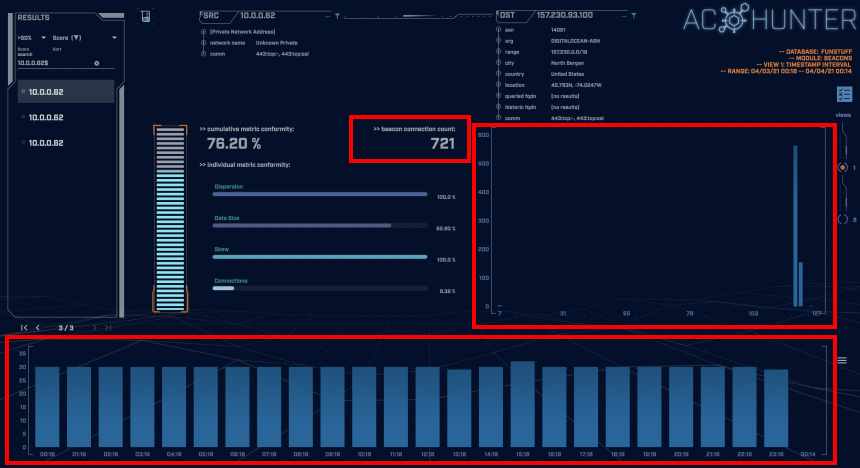
In the above screenshot, we have an interesting connection going to an unknown address identified as a beacon by AC-Hunter/RITA. It clearly displays beaconing behavior but has a fairly low connection count over 24-hours. In the bottom graph, each blue block represents the number of connections per hour. Moreover, there doesn’t seem to be any timing jitter, so perhaps it may be a legitimate service. However, as a threat hunter this is not something we would want to ignore since it could be an adversary on our network attempting to hide their tracks using a slow beacon.
In this case, this is the traffic to our external server running PoshC2. The default delay between PoshC2 connections is five seconds however this can easily be edited in the PoshC2 server config file, as has been done here. This is a 120 second beacon, which is plenty slow enough to avoid beacon detection among many tools.
As displayed in the screenshot below, the average data size of the beacon’s communications is around 900 bytes, which shows us that not a large amount of data is being transferred.
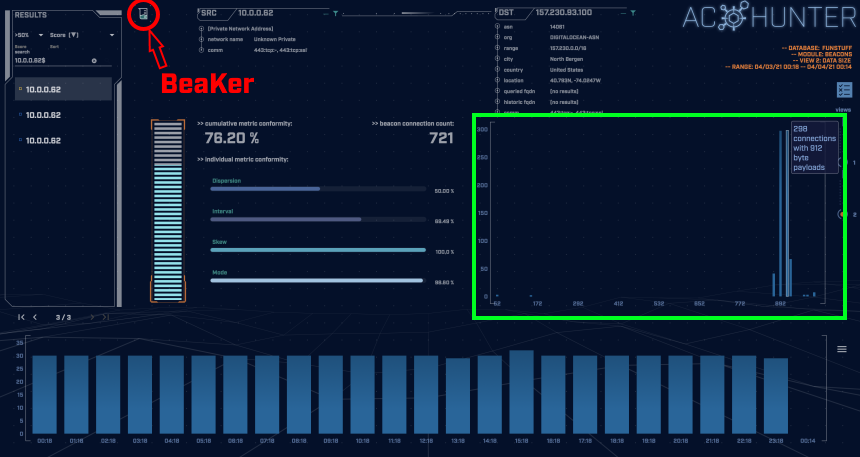
We have stated that this traffic came from running an external PoshC2 server, but what if we didn’t know that? What else could we do to determine if the local machine may have been compromised? It would be very useful to know exactly where the process making these connections originated. Luckily, using BeaKer we can do exactly that.
BeaKer is an open-source tool that visualizes Microsoft Sysmon endpoint data to help threat hunters track down the source of suspicious network connections. If installed alongside AC-Hunter, we can click the BeaKer icon in the top-left of AC-Hunter (shown above) and it will take us directly to the Kibana dashboard with the connection details loaded.
(BeaKer can be installed independently from AC-Hunter and will work just as well.)
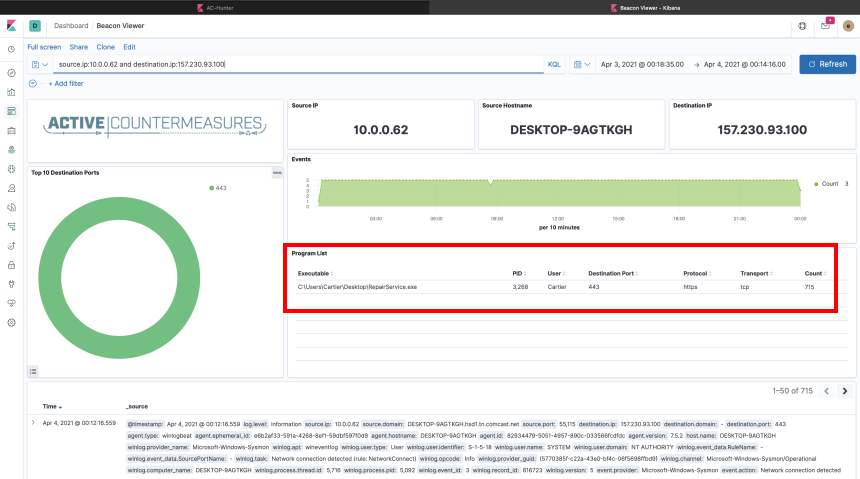
The above screenshot is taken from the BeaKer dashboard. What we are most interested in is which process or processes are responsible for these connections.
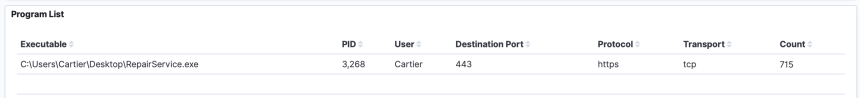
Looking at the connections between 10.0.0.62 & 157.230.93.100, we can see under Program List, a singular program was responsible for this traffic. The highlighted box shows us information about the process that we are interested in. It appears the program was called “RepairService.exe”. That looks suspicious but almost normal. Not as suspicious as something like “Posh_v4_dropper_migrate_x64.exe”, but still suspicious.
We continue our investigation by looking at who started the process and where it lives. It is more likely that a “repair service” or any legitimate service for that matter would be started by the SYSTEM or LOCAL SERVICE rather than a regular user. In this instance, a big giveaway is the location. We can see it was started from the desktop, whereas most system programs are running under a system subdirectory. Why would it be running on the desktop? Maybe “someone in IT” called and asked the user to download and run the program?
We cannot make any definitive claims about what happened from this alone but the information regarding the responsible program gives us a decent advantage in determining the legitimacy of the connection, where to start to investigate further, and to determining the probability of a compromise.
At the very least, we now know what questions to ask and where to ask them.
As always, we encourage you to download the associated PCAP files below and analyze them in a program/tool of your choosing to test your detection abilities.
Capture Files
Because… PCAPs, or it didn’t happen. 😊
The following PCAP files are packet captures taken from the same lab environment over a one-hour time frame and a 24-hour time frame. The files were generated using Wireshark from the target host. The PCAPs are safe, standard PCAP files and do not include any actual malware.
PoshC2 Stealthy 1 Hour Capture
posh_stealthy_1hr.pcap (served by Dropbox)
Size: 5.56 MB
SHA256 Checksum: 4456B3127223D2CEA3B7281341375250A0A0BA737DC7F9C23F88A462A4066DDD
PoshC2 Stealthy 24 Hour Capture
posh_stealthy_24hr.pcap (served by Dropbox)
Size: 99.8 MB
SHA256 Checksum: A46699496E3BD0E6D274D37CBF39D6EA67758BAE7109F8B3603C8B1B3B7A2B06
Discussion
Want to talk about this or anything else concerning threat hunting? Want to share how good (or not so good) other detection tools were able to detect this sample?
You are welcome to join our Discord server titled “Threat Hunter Community” to discuss topics surrounding threat hunting. We invite you to join our server here.

Hannah joined Active Countermeasures as an intern in 2020. She is currently a graduate student at the University of Utah.