Malware of the Day – EvilOSX
What is Malware of the Day?
Lab Setup
Malware: EvilOSX
MITRE Tactics: TA0011 Command and Control, T1219 Remote Access Software
Traffic Type: Generic
Connection Type: HTTP
C2 Platform: EvilOSX
Origin of Sample: https://github.com/Marten4n6/EvilOSX
Host Payload Delivery Method: Python Script
Target Host/Victim: 10.0.0.25 – macOS
C2 Server: 157.230.93.100
Beacon Timing: 30s
Jitter: 0%
Brief
Our focus is on identifying anomalous network activity in order to detect and respond to threats. Today we are using AC-Hunter/RITA as our network threat and C2 detection platform to visualize the network traffic generated from running EvilOSX, a command and control software that targets macOS/OSX operating systems.
EvilOSX is a RAT (Remote Access Trojan) written primarily in Python. It provides the user with a simple remote terminal instance on the compromised machine. A remote shell can be used to collect data, cause harm to the machine, install additional malware, etc. Our goal in analyzing the traffic generated by this tool, among others, is to give us a well-informed view of what malicious network activity looks like.
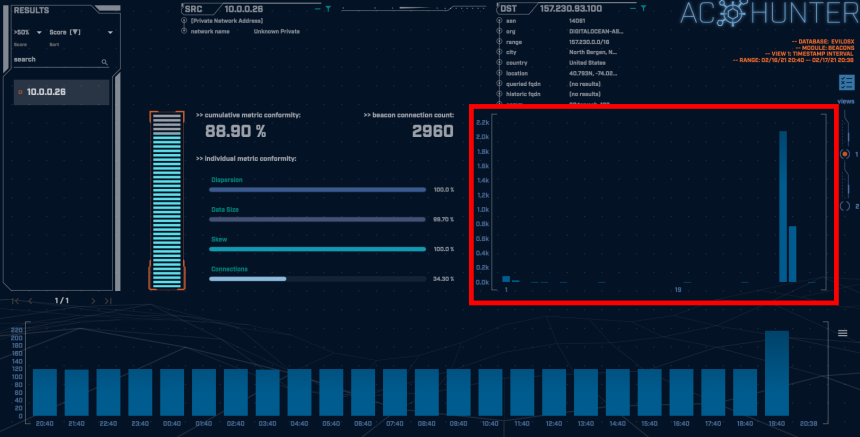
The above screenshot is taken of the AC-Hunter Beacons module from a 24-hour traffic capture. The client machine makes a connection to the server once every 30 seconds as shown by the box highlighted in red. The graph shows several outliers which we can attribute to a combination of remote commands being run and natural network delays.
The graph at the bottom of the screen shows the number of connections per hour, each blue block representing a one-hour time frame. The consistency of the number of connections is a strong indicator of non-human behavior. In almost all cases it is safe to assume that a normal human user on the network is not initiating a connection directly to an IP address over one hundred times an hour.
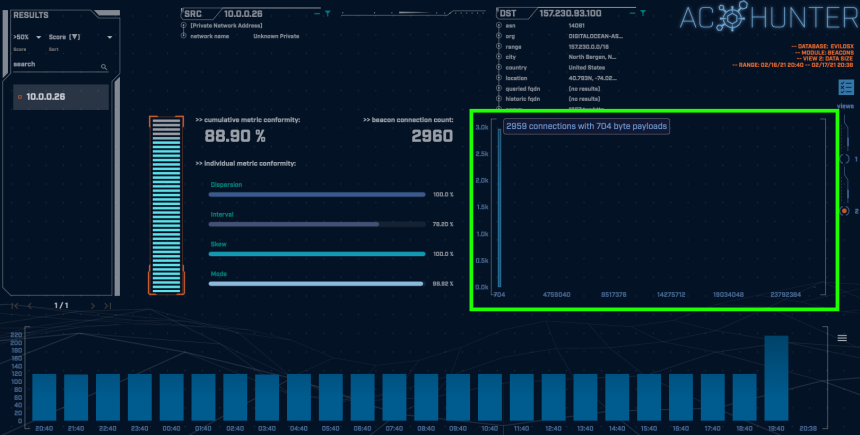
Switching to the connections data size view (shown in the green highlighted box above), it appears all of the connections have the same size, transferring only 704 bytes of data.
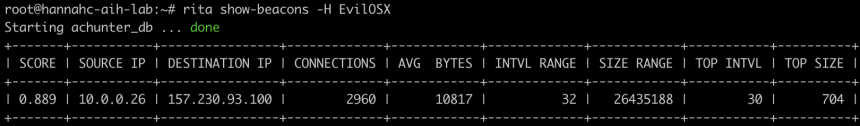
This beacon analysis can also be performed using our open-source tool for network traffic analysis, RITA (Real Intelligence Threat Analytics). RITA gives this connection between IP pairs an 88.90% threat score. We can also see statistics about the data size distributions as well as the total amount of bytes sent:
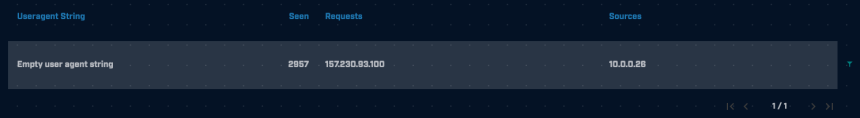
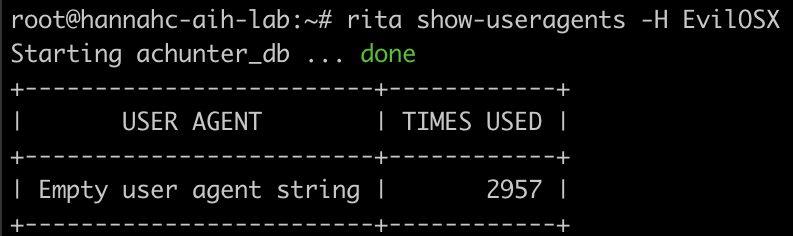
Beaconing behavior aside, another indicator that this connection may be malicious is an empty user-agent string. A “user-agent” is a string contained within the HTTP header designed to provide information to the server about the client in order for the server to properly display the requested content on multiple types of devices. An empty user-agent is suspicious because web browsers as well as most legitimate programs attach a user-agent string automatically. The screenshot below shows the user-agent analysis provided by AC-Hunter.
This can also be viewed in RITA by running the command:
rita show-useragents -H EvilOSX
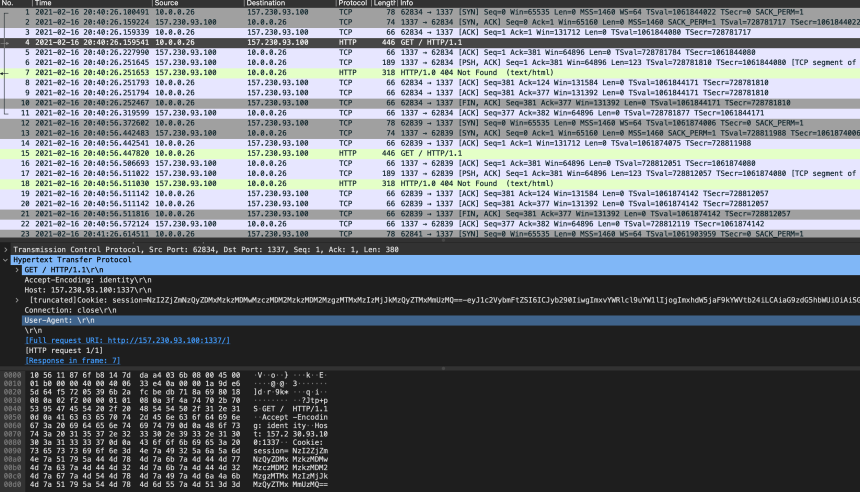
The below screenshot shows the HTTP request in Wireshark. Looking at the individual fields of the HTTP header directly is another way to inspect user-agent strings, or the lack thereof.
We encourage you to download and use the PCAP files included in the next section to analyze them independently using your preferred threat hunt platform to test your detection capabilities.
Capture Files
Because… PCAPs, or it didn’t happen. 😊
The following PCAP files are packet captures taken from the same lab environment over a 1-hour time frame and a 24-hour time frame. The files were generated using Wireshark from the target host and include normal systems OS traffic and normal network broadcast traffic. They have not been edited. The PCAPs are safe, standard PCAP files and do not include any actual malware.
EvilOSX 1 Hour Capture
evilosx_1hr.pcap
Size: 467.32 KB
SHA256 Checksum: 964542714ED93132CC2D0430065C239E3277C47D1609BD8A01751FA9BE3DF85C
EvilOSX 24 Hour Capture
evilosx_24hr.pcap
Size: 32.3 MB
SHA256 Checksum: 1B9C9901541F508A507E96E5903190C5211C8DCD18DC881611B0CFB0A63A14C3
Discussion
Want to talk about this or anything else concerning threat hunting? Want to share how good (or not so good) other detection tools were able to detect this sample?
You are welcome to join our Discord server titled “Threat Hunter Community” to discuss topics surrounding threat hunting. We invite you to join our server here.

Hannah joined Active Countermeasures as an intern in 2020. She is currently a graduate student at the University of Utah.