Log Analysis Part 3 – Lateral Movement
This is Part 3 of a 3 Part Series
Lateral Movement
Let’s take a few moments and walk through just a few underpinnings of detecting lateral movement by looking at the security logs from a domain controller.
For this section we will be looking at the logs through the lens of LogonTracer and by the local Windows Event Viewer itself.
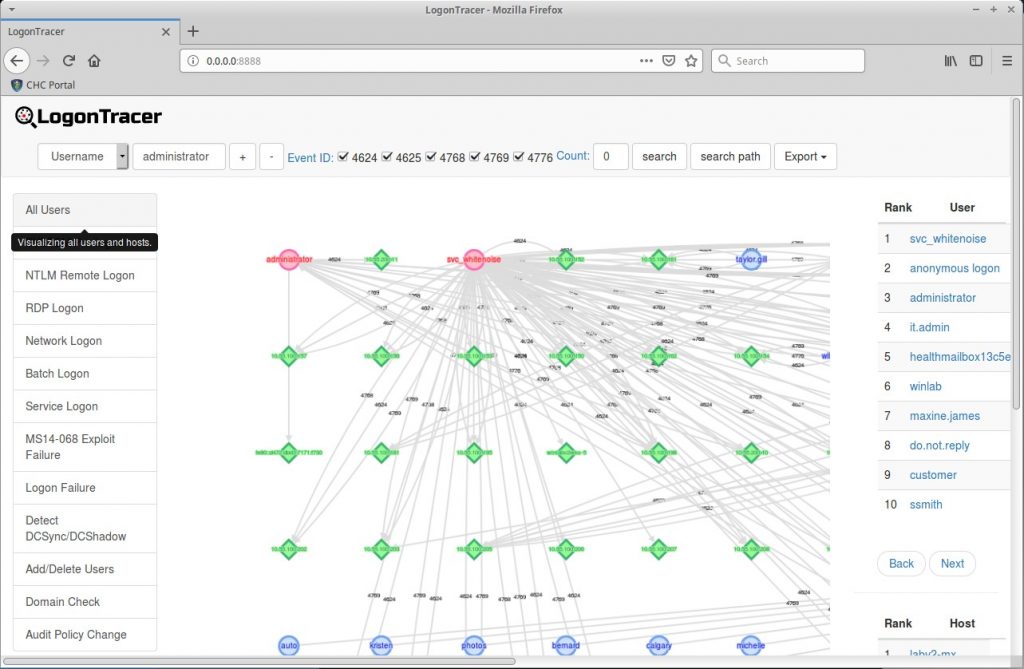
Logon Tracer is one of the cooler standalone UBEA tools you can have in your Incident handler bag of tricks. It does not have nearly as many features as a full fledged UBEA in a SIEM. However, it is very solid for standalone IR and for demonstrating and graphing attacks. It has the ability to review multiple .evtx files and tie together the authentication graph of a domain. In the above screenshot we can see there are multiple different systems, represented in green diamonds, being accessed by multiple accounts, represented with red circles.
LogonTracer with Lateral Movement
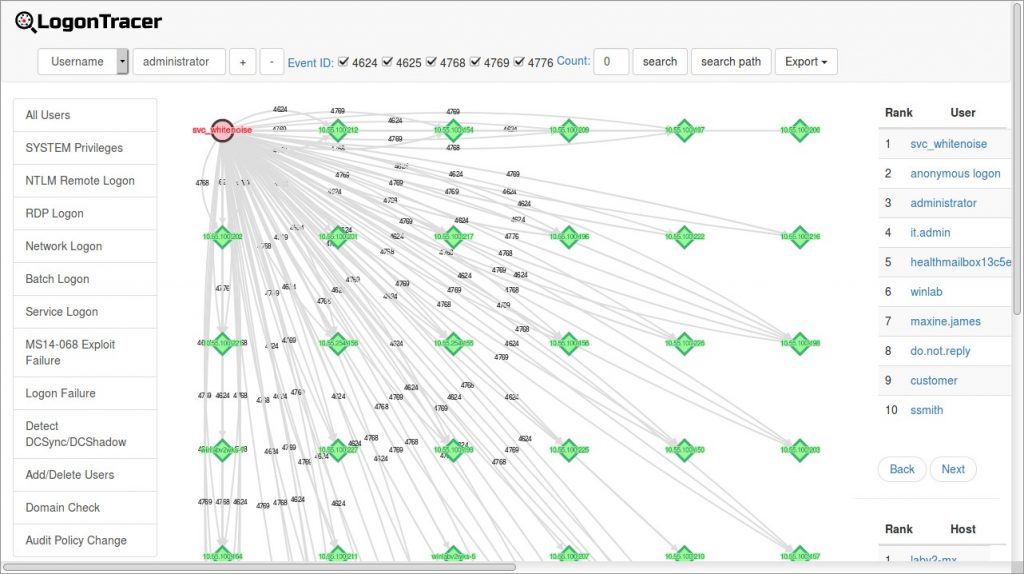
If we focus on one of these accounts. we can see all of the systems that the account is currently authenticated to. In the above example, we have the svc whitenoise account logged into multiple systems at the same time. This could be a service account doing service account things. However, it could also be a compromised service account or a user account that is being used as a puppet by an attacker. Attacks like Pass-the-Hash and simply using a compromised account would create this type of an effect on a network.
This attack technique is also used by groups like APT28 and is referenced below:
https://attack.mitre.org/techniques/T1075/
Bloodhound

Another tactic is for attackers to use an existing account and access multiple systems to check the accounts permissions on that system. This can be used to quickly identify paths where an unprivileged account has local administrator privileges on a system. But, on another system they may have local administrator rights. Tools like Bloodhound and Deathstar have this ability and can quickly discover a path to Domain Administrator.
In the above screenshot there are multiple 4769 events being triggered. Every one of them is by the Maxine.James account.
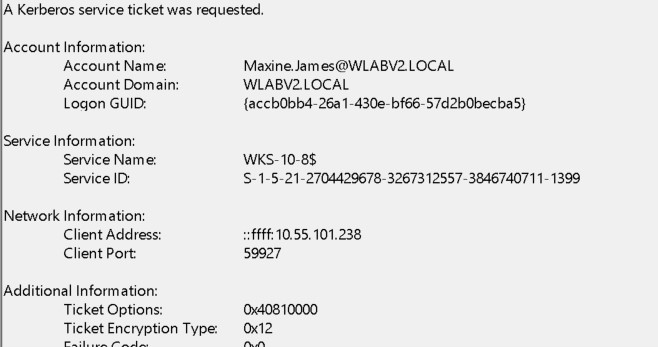
They are also for multiple systems:
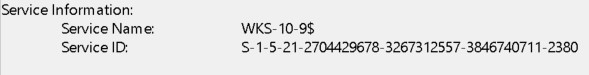
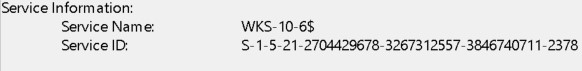
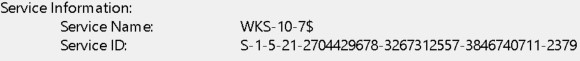
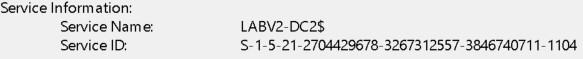
In this example, the attacker compromised the user account and then pivoted to multiple machines to find a path to domain administrator.
It is very, very important to have a firm understanding of how these tools work and exactly what situations we can hunt for in an environment. True, tools like LogonTracer are not nearly on par with features and alerting that you would get from a commercial UBEA. But, it should work just fine to demonstrate the value proposition for having these tools added to the defenders arsenal.
This is Part 3 of a 3 Part Series – PART 1 | PART 2 | PART 3

John has both consulted and taught hundreds of organizations in the areas of security, regulatory compliance, and penetration testing. He is a coveted speaker and much loved SANS teacher. John is a contributor to the industry shaping Penetration Testing Execution Standard and 20 Critical Controls frameworks.