Malware of the Day – Attack Vectors: TeamViewer
What is Malware of the Day?
Lab Setup
Malware: N/A
Application: TeamViewer
MITRE Tactics: TA0007 Discovery, TA0006 Credential Access, TA0011 Command and Control
AKA: N/A
Traffic Type: Application
Connection Type: HTTPS/UDP/TCP
C2 Platform: N/A
Origin of Sample: https://www.teamviewer.com/en-us/
Host Payload Delivery Method: N/A
Target Host/Victim: 192.168.99.52 – Windows 10 x64
C2 Server: N/A
Beacon Timing: N/A
Jitter: N/A
Remote Access as a Command and Control Channel
It should be stated at the outset that TeamViewer is NOT malware. TeamViewer is a proprietary software application for remote control, desktop sharing, online meetings, web conferencing and file transfer between computers. It is a useful and widely used platform to allow users remote access to computer systems. Because of its wide-spread use and powerful features, it has become a popular target as an attack vector to compromise network assets.
Historically, there have been many systems and networks compromised using TeamViewer as an entry point. The most recent public disclosure of which happened only days ago by an attacker that gained access through the TeamViewer application and attempted to poison a Florida city’s water supply by manipulating an industrial control system:
https://www.wired.com/story/oldsmar-florida-water-utility-hack/
Is TeamViewer bad? Absolutely not. A good number of these application compromises are gained by cracking user credentials. One of the quickest and easiest defenses to this is to implement strong and long application passwords. By default, TeamViewer generates a random 6-character password for remote connections. This can be easily changed by the user to anything desired and using a minimum of 16-characters of password length is a good start. This does not entirely solve the problem, but at the least, makes the password harder to solve. There will continue to be discussions and increased hardening measures concerning internet-facing applications such as these. However, our focus here is upon the network traffic and indications of nefarious communications.
If your network environment does not use the TeamViewer application, monitoring your network traffic for this specific attack vector becomes very clear; if you witness any communications to or from TeamViewer domains or TeamViewer owned IPs, those connections should be investigated.
If your network environment does use the TeamViewer application, monitoring your network traffic has increased importance pertaining to these specific communications.
In this TeamViewer lab test, we are connecting to our internal host at 192.168.99.52 from a remote system through the TeamViewer application.
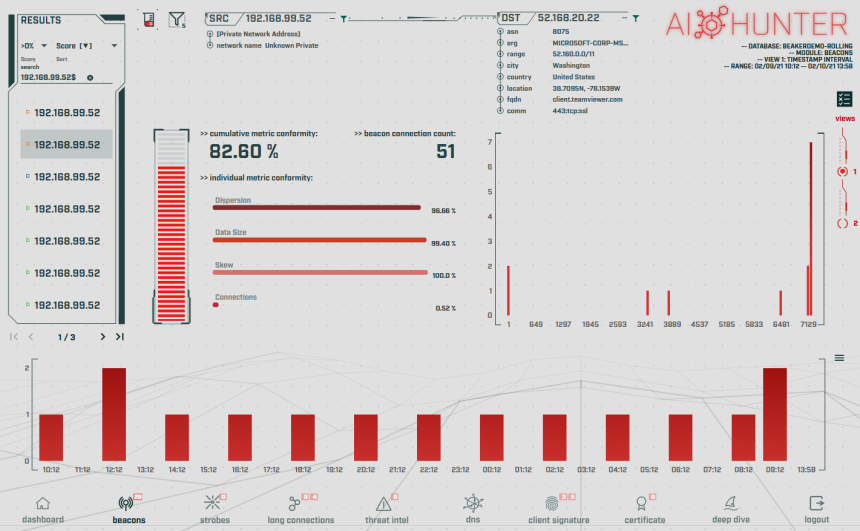
We have captured the network traffic generated by running TeamViewer, both at “idle” and being used as a remotely accessed computer system. The traffic pattern and beaconing activity can be viewed clearly using AC-Hunter.
AC-Hunter has flagged these communications as a potential threat and has scored a strong beacon signal of 82.60% beacon conformity. The traffic patterns observed look very similar to command and control traffic. Notice the consistent pattern of connections within the bottom hourly histogram graph. Does this mean this is evil? Not necessarily, however it brings it to our attention as connections that should be investigated.
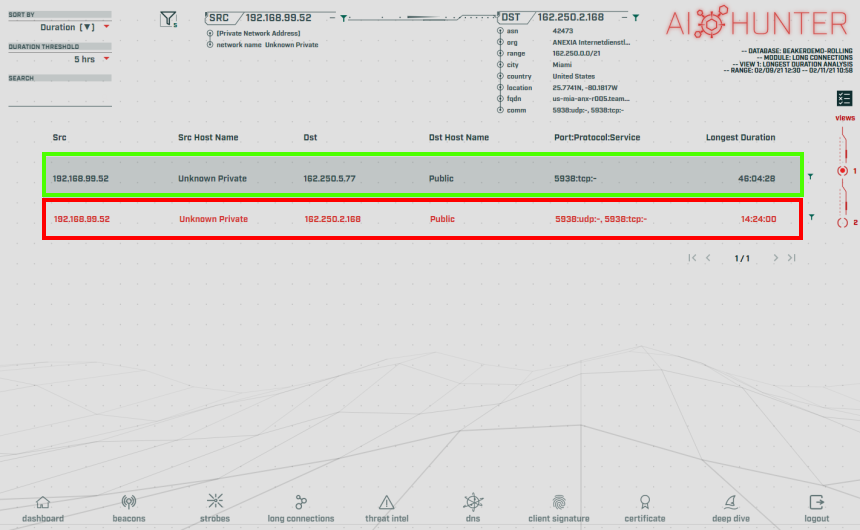
Another method for viewing TeamViewer use within AC-Hunter is in the Long Connections module:
We have two things going on here. The long connection of 46h:04m:28s highlighted in the green box is when the TeamViewer application was installed on the host. This was installation only, no remote connections were made by the user and the application was left alone. The long connection of 14h:24m:00s highlighted in the red box is from when a remote connection was established and left connected.
This information is not only useful for overall visibility of TeamViewer connections, but also for the timing of these connections. As an example, let’s say that your employees use TeamViewer for remote connections during their normal 08:00-17:00 UTC work schedule. Further analysis of the timing of these remote connections should align with that schedule. If we were to see a 2-hour long connection at 02:00 UTC, that would definitely appear suspicious and should be investigated.
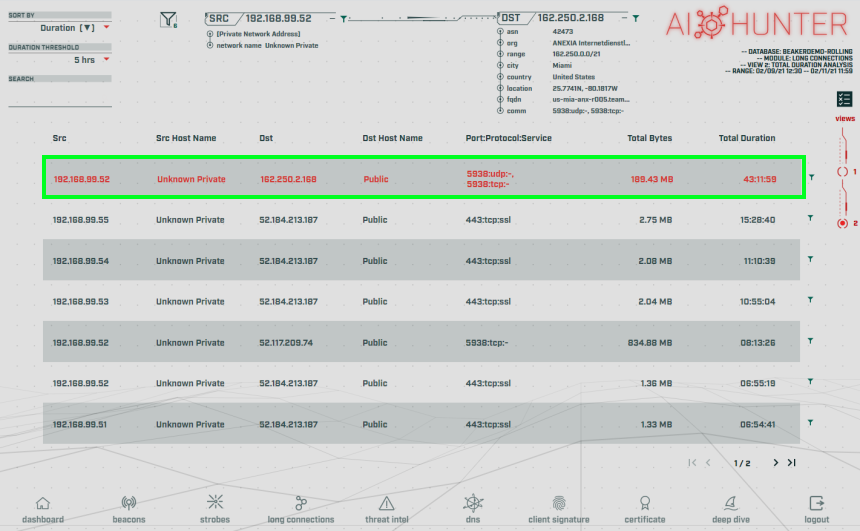
Taking this a step further, we can switch to View 2 within the Long Connections module:
This displays the cumulative connection time and total bytes transferred. The total bytes transferred can be extremely useful as an analysis of usage. As an example, should a normal user performing their daily work be transferring 1TB of data across the wire using TeamViewer? Probably not.
This only scratches the surface of threat hunting, securing and monitoring such applications. Visibility is key.
Don’t have AC-Hunter yet? The same network traffic analyses can be performed using our open-source tool RITA. It’s free!
So, what does TeamViewer traffic look like on your network? We’ve included 2 network capture files below. The 1-hour capture file is of TeamViewer connected remotely, but unattended/idle. The 24-hour capture file is of TeamViewer unattended/idle for the first 19 hours, then a remote connection was made at 09:36 EST, then a 255MB file was transferred from the host to the remote starting at 09:40 EST.
Capture Files
Because… PCAPs, or it didn’t happen. 😊
The AC-Hunter results above are a 24-hour observation and analysis from Zeek logs running in a lab 24/7. The following PCAP files are packet captures taken from the same lab environment over a one-hour time frame and a 24-hour time frame. The files were generated using Wireshark from the target host and include normal Windows OS traffic and normal network broadcast traffic. They have not been edited. The PCAPs are safe, standard PCAP files and do not include any actual malware.
TeamViewer 1 Hour Capture
teamviewer_1hr.pcap
Size: 46.45 MB
MD5 Checksum: 3ff0008d74dc1d80ef578dbd2024b372
TeamViewer 24 Hour Capture
teamviewer_24hr.pcap
Size: 308.94 MB
MD5 Checksum: f0309526de66dda8cda4226c541cb7e0
Discussion
Want to talk about this or anything else concerning threat hunting? Want to share how good (or not so good) other detection tools were able to detect this sample?
You are welcome to join our Discord server titled “Threat Hunter Community” to discuss topics surrounding threat hunting. We invite you to join our server here.
Additional Resources
https://www.teamviewer.com/en-us/
Until the next!

Keith’s appreciation for computing and processes originates from working with his first personal computer in 1982, a TI-99/4A. Keith sees himself as fortunate for the opportunity to apply his passion towards a career that assists in the advance of technology and continuing education.