Malware of the Day – Indicators of Compromise: Lateral Movement and Backup C2
What is Malware of the Day?
Lab Setup
Malware: N/A
Application: Covenant using Brutes (A cross-platform .NET Core implant)
Traffic Type: Generic
MITRE Tactics: TA0008 Lateral Movement, TA0011 Command and Control, T1534 Internal Spearphishing
Connection Type: Reverse HTTP
C2 Platform: Covenant
Origin of Sample: https://github.com/cobbr/Covenant
Host Payload Delivery Method: C# Implant
Target Host/Victim: 10.0.0.31, 10.0.0.80, 10.0.0.61 – Windows 10 x64
C2 Server: 157.230.93.100
Beacon Timing: 30s & 1800s
Jitter: 10%
Brief
Our focus is on identifying and detecting network beaconing behavior. We are using AC-Hunter/RITA as our network threat detection platform to visualize the traffic generated by compromised hosts beaconing back to a server running Covenant C2. Covenant is an open-source post-exploitation command and control platform framework utilizing the .NET platform. It includes payloads for Windows, Mac and Linux, and allows for code modification directly through the web interface.
This week we are simulating what lateral movement can look like within a network and how we can detect communications to external sources. Even for a sophisticated attacker, compromising one system is usually not enough. According to MITRE ATT&CK: “Reaching their objective often involves pivoting through multiple systems and accounts to gain. Adversaries might install their own remote access tools to accomplish Lateral Movement or use legitimate credentials with native network and operating system tools, which may be stealthier.”
Once attackers have a foothold into the internal network there are a variety of methods for moving between systems at their disposal. In this simulation, Internal Spearfishing was used. Gaining additional channels makes the adversary more resilient, since in the case that if the main command and control channel goes down or gets discovered, they have a pool of backup hosts waiting for them to be activated to take over as the primary communications channel.
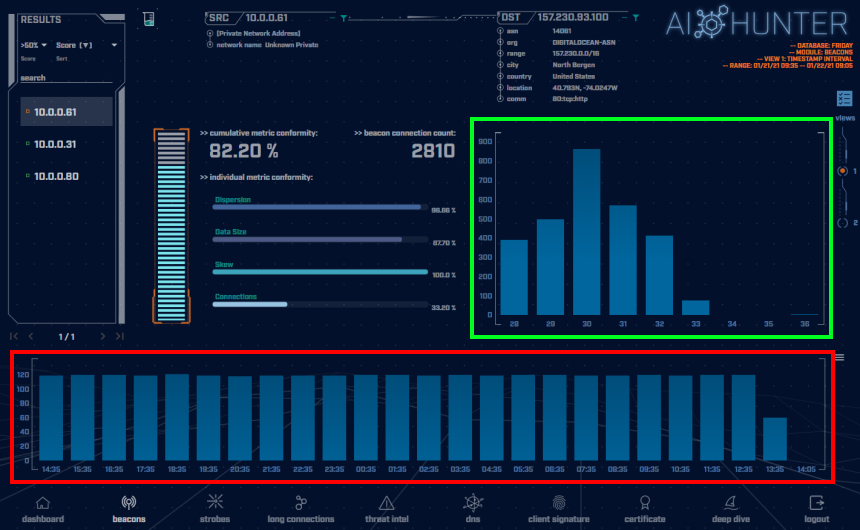
The screenshot below shows the beacon screen of the AC-Hunter interface displaying the connection behavior for the main command and control channel. The host is connecting once every thirty seconds (+/- 10%) indicated by the beacon timing graph in the green highlighted box. Even with 10% jitter introduced into the timing, this connection still gets a fairly high beacon score of 82.20%. Note also how the total connection counts per hour are very consistent, indicated by the flat histogram in the red highlighted box.
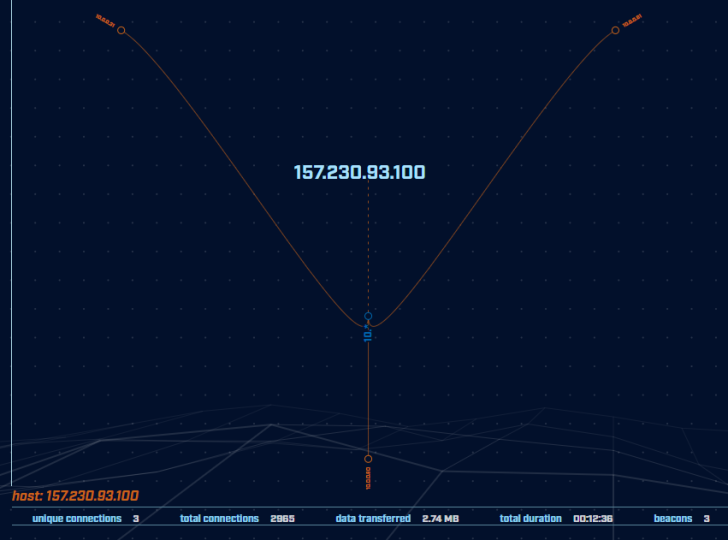
Once you discover one command and control channel, AC-Hunter makes it very easy to see which other machines may be compromised. Clicking the IP of the external server and choosing “deep dive” from the pop-up menu switches us into the deep dive module and provides us a graph showing all systems the given address is talking to.
Here we see that the server in question (157.230.93.100) was connecting to a total of three internal addresses. Connections drawn in orange indicate AC-Hunter has flagged these connections as suspicious. This makes it much easier to track down the sneakier communications that are showing signs of potentially malicious behavior.
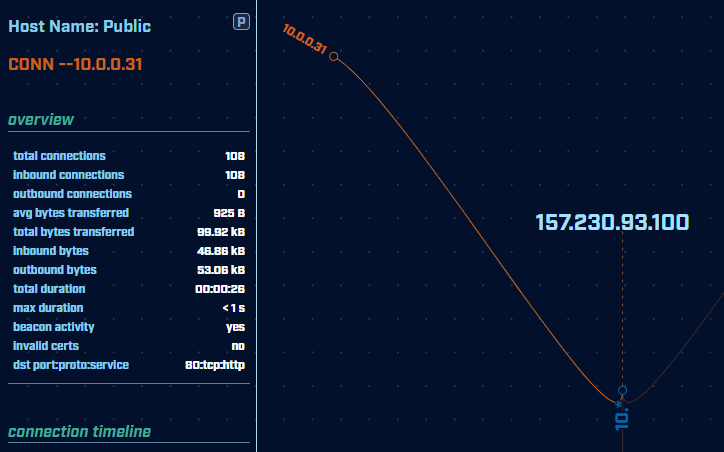
Hovering over an IP gives us more details about that specific connection. We can see the average data transfer size as well as the total amount of inbound and outbound traffic. A high amount of outbound traffic can be a great indicator of whether data is being stolen from your network.
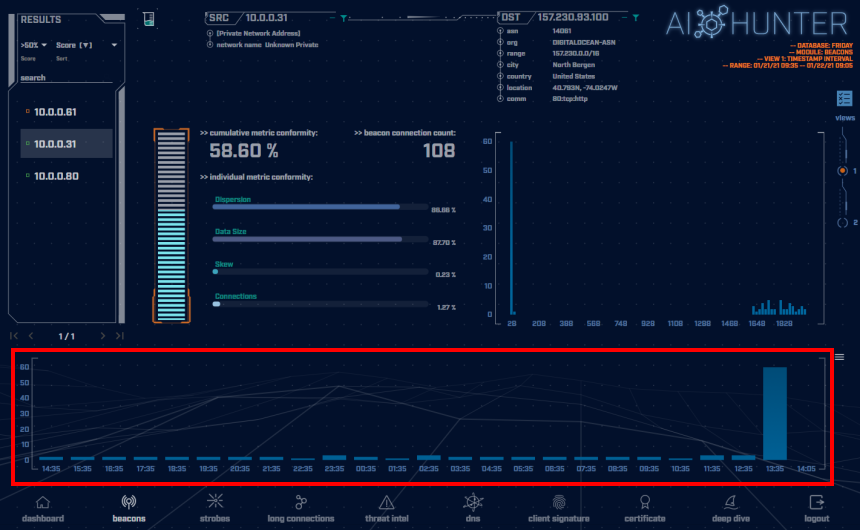
With this new information, going back to the beacon screen gets a bit more interesting. The screenshot below shows the beacon timing for a “dormant” host on the internal network communicating to the same external server. Here the timing graph tells more of a story. Within the first hour after the implant connected, the adversary set the timing delay to once every 30 minutes to avoid detection. While this makes it less likely to get noticed by beaconing detection, it also makes it relatively unusable due to the time the attacker would have to wait both for instructions to be sent and replies to be received between connections.
Notice there is a spike in connections near the end of the histogram graph which indicates the attacker “re-activated” the communication, likely in order to make use of the host.
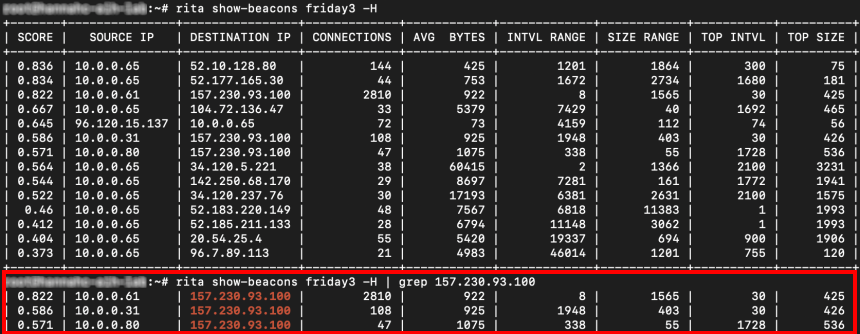
A similar analysis can also be performed using our open-source tool RITA. Analyzing a larger enterprise network one may be bombarded with a lot more data to sort through. Luckily once we become suspicious of a particular IP, we can pipe the output of the show-beacons command into our good old friend grep for a much more informative view, as shown above.
We have shown that once you find one indicator of compromise, it is imperative to dive a little deeper and see who/what else might be hiding out and communicating to the same destination. Attackers are constantly becoming more creative, and you never know what you’ll find… unless you are not looking. 🙂
We encourage you to download and use the PCAP files included in the next section to analyze them independently using your preferred threat hunt platform to test your detection capabilities.
Capture Files
Because… PCAPs, or it didn’t happen. 😊
The following PCAP files are packet captures taken from the same lab environment over a one-hour time frame and a 24-hour time frame. The files were generated using Wireshark from the target host. The PCAPs are safe, standard PCAP files and do not include any actual malware.
Lateral Backup C2 1 Hour Capture
lateral_backup_c2_1hr.pcap (served by Dropbox)
Size: 218 KB
MD5 Checksum: 48e30ed3e87f1819948f5787862ae1bc
Lateral Backup C2 24 Hour Capture
lateral_backup_c2_24hr.pcap (served by Dropbox)
Size: 3.40 MB
MD5 Checksum: b9f8c5c7336dd85120be87308c521b9d
Discussion
Want to talk about this or anything else concerning threat hunting? Want to share how good (or not so good) other detection tools were able to detect this sample?
You are welcome to join our Discord server titled “Threat Hunter Community” to discuss topics surrounding threat hunting. We invite you to join our server here.
Additional Resources
https://attack.mitre.org/tactics/TA0011/
https://attack.mitre.org/tactics/TA0008/
Until the next!

Hannah joined Active Countermeasures as an intern in 2020. She is currently a graduate student at the University of Utah.